Managed SIEM Service
Extend, simplify, and centralize your security visibility while automating advanced threat detection using the managed SIEM solutions of LevelBlue Managed Threat Detection and Response.
Why Managed SIEM with LevelBlue?
Help reduce the cost and complexity of threat detection and response
Detecting and responding to advanced threats relies heavily on an organization’s visibility into their network and an understanding of what’s being monitored. Traditional security information event management (SIEM) requires significant effort to integrate multiple disparate security data sources to provide visibility, and an equally material amount of internal cybersecurity expertise to be of real value in most organizations.
LevelBlue Managed Threat Detection and Response is an MDR service that helps you to detect and respond to threats before they impact your business. It provides 24 x 7 proactive security monitoring, alarm validation, security orchestration and automation, and more in one service, helping you to enhance your security posture quickly and cost effectively.
Comprehensive 24x7 security monitoring
Detect threats using data from a wide range of built-in security monitoring technologies and sources in one unified solution.
Respond to threats faster
Our team of analysts monitor alerts to validate threats, providing guided and automated response to internal IT teams.
Stay ahead of the latest threats
Continuously updated threat intelligence from LevelBlue Labs empowers our ability to effectively detect advanced threats.
SIEM made cost-effective
Get managed SIEM as a part of our broader MDR offering without the additional costs of setup, staffing, and threat intelligence.
Resources
Learn more about threat detection and response
Traditional SIEMs get their value in the consolidation and correlation of security event data, but a SIEM is only as good as the information put into it and how easy it is to consume.
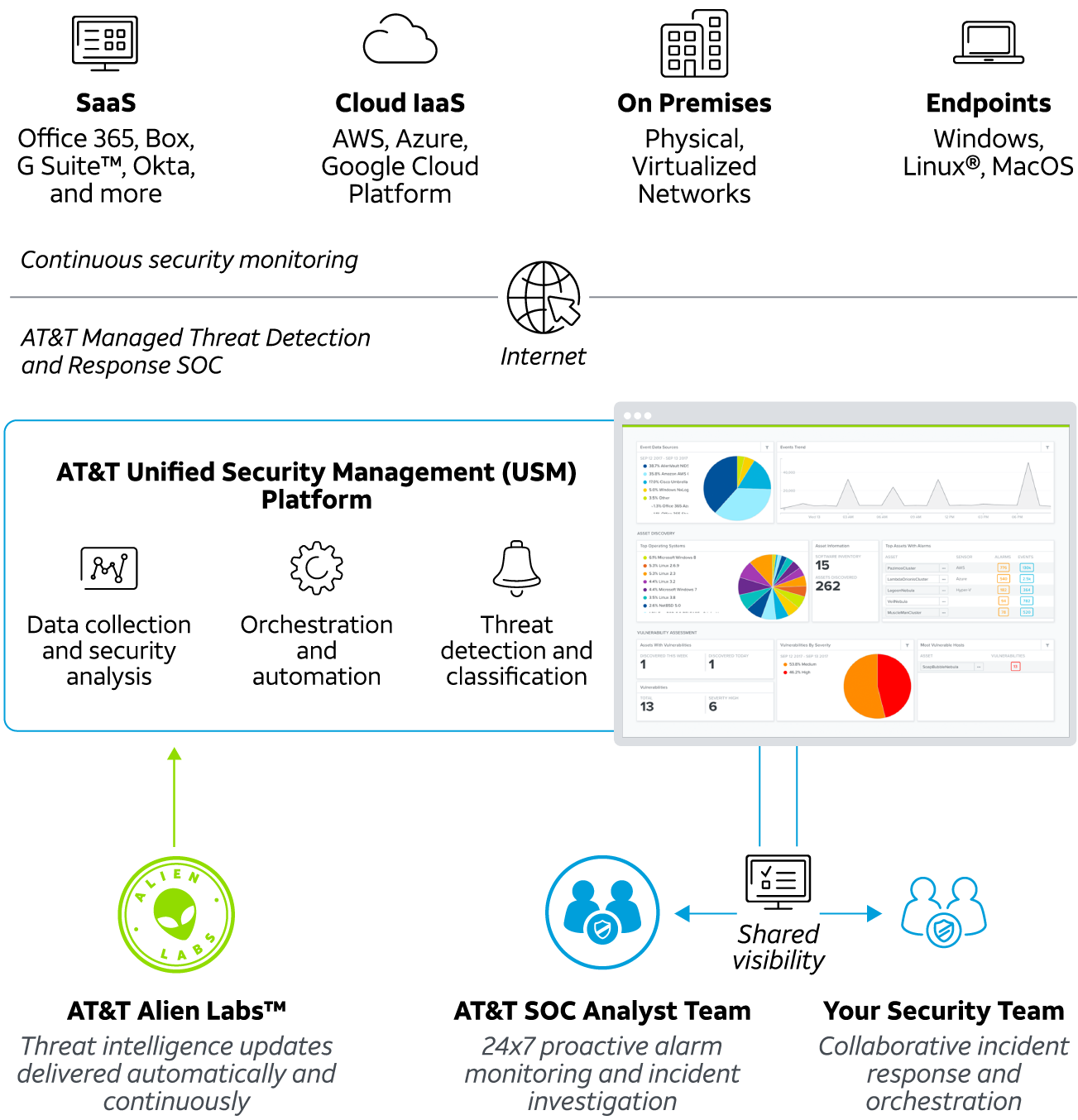
Our managed SIEM functionality is built on the LevelBlue Unified Security Management (USM) platform that combines multiple essential security capabilities in one unified console that helps support earlier detection, fewer false positives, and faster response.
- Traditional event and log sources
- Asset discovery
- Network IDS
- Host IDS
- File integrity monitoring
- Cloud (AWS, Azure, Google Cloud Platform)
- Vulnerability assessment
- Endpoint detection and response
- Threat intelligence
AlienApp integrations for continuous monitoring and security orchestration
The highly extensible architecture of the USM platform makes it possible to readily extend its security orchestration and automation capabilities through modular software components called AlienApps. Some of the 300+ pre-built AlienApps include Microsoft Office 365, Box, Salesforce, Google G Suite™, Cisco Umbrella™, Palo Alto Networks®, CarbonBlack, and more.
Many “threats” are merely best guesses based on correlated events that are anomalous and, therefore, are given a degree of suspicion. Threat detection can’t be a guessing game of “too many false positives” – this becomes costly, ineffective, and increases the risk of a successful cyberattack.
LevelBlue Managed Threat Detection and Response takes traditional managed SIEM and brings context and insight to anomalous events to quickly detect current, emerging, and evolving threats with continuous threat intelligence from LevelBlue Labs.
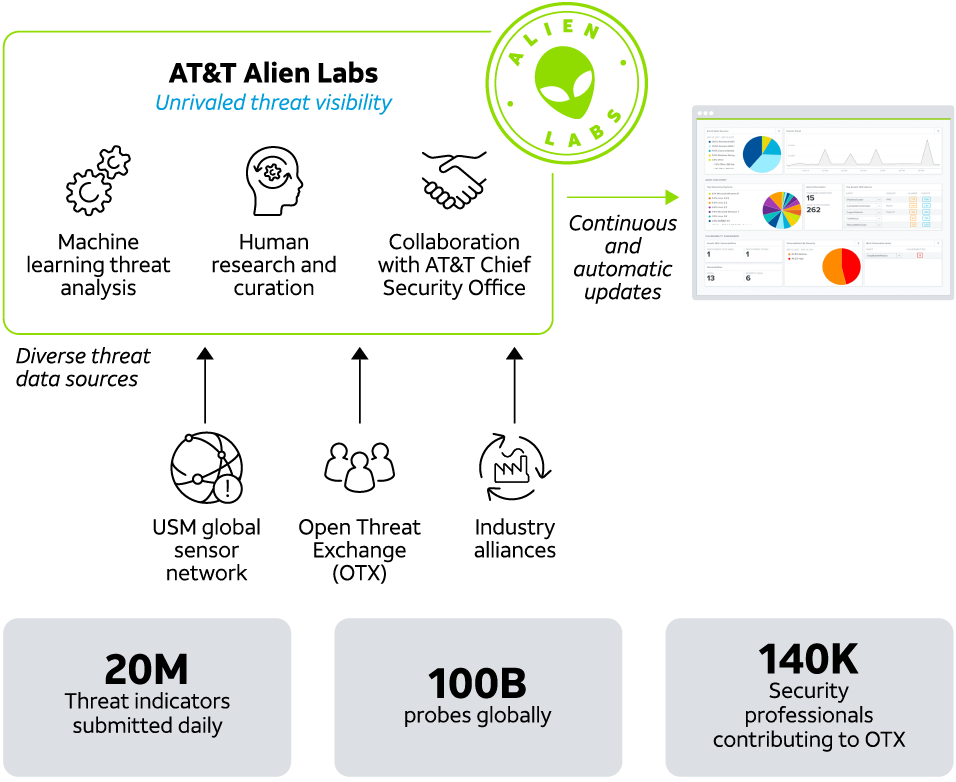
Unrivaled threat visibility
LevelBlue Labs has visibility into the LevelBlue IP backbone, the global USM Sensor network, the Open Threat Exchange (OTX), and other sources of threat data.
Deep insights into adversaries and attacks
The Alien Labs research team uses proprietary analytics, machine learning (ML), and a global team of threat researchers to analyze and interpret the huge volume of threat data we collect. This team goes beyond simply delivering threat indicators to performing deep, qualitative research that provides insight into adversary tools, tactics, and procedures (TTPs) to our customers and the larger intel community.
There are two inherent problems with traditional SIEM. First, you have to know what you’re looking at, and second, you need to know what to do about it. Internal IT teams – while experts on their internally supported systems and applications – are often not experts in advanced, evolving, and emerging threats.
With managed SIEM as part of LevelBlue Managed Threat Detection and Response, protecting your organization from advanced threats is simplified.
Every part of your network, monitored
Your critical infrastructure is monitored 24x7 by our team of advanced security experts and analysts.
Every alarm and incident, reviewed
Our analyst team reviews every SIEM alarm, determining which ones are actionable, so your team can focus on actual attacks threatening your organization.
Every detail and dashboard, accessible
You can log onto the very same USM instance as our team of experts to assess, review, report, or respond to potential threats.
Every response, a team effort
We provide your internal response team with detail, context, and recommendations on how to swiftly and effectively respond to and remediate detected threats.
Putting a traditional SIEM in place – one that effectively detects threats and not just anomalous event “noise” – is no simple feat. It requires significant time, money, and internal expert staffing just to implement, let alone maintain.
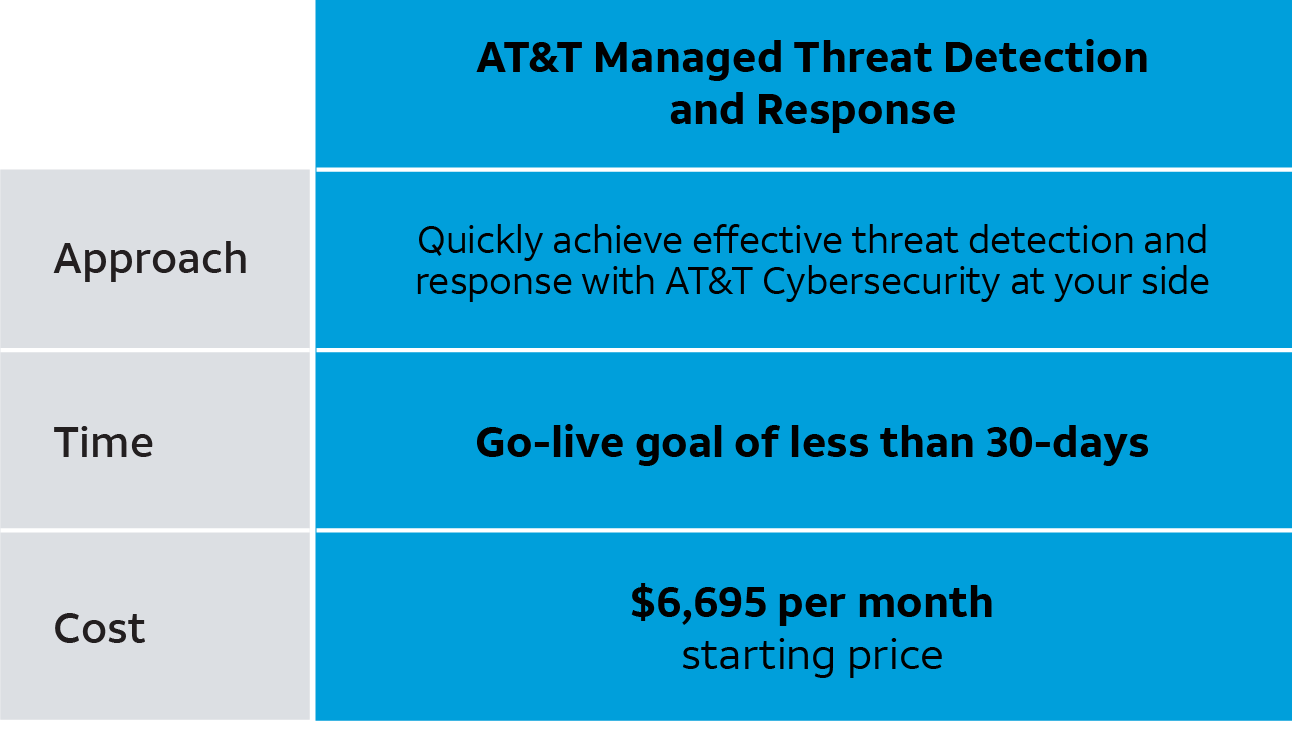
Instead, with managed SIEM as part of LevelBlue Managed Threat Detection and Response, it’s possible to expand well beyond the expectation of simple security event management to include helping protect your business 24x7. With the goal of your managed SIEM being up and fully functional in 30 days, our MDR offering takes less time to deploy and costs less than hiring a single security analyst.
Use cases
Managed SIEM helps IT teams deliver effective security
Better security detail and intelligence
Knowing what a threat looks like makes or breaks a SIEM. With over 450+ integrations matched with continually updated threat intelligence, your organization is best positioned to detect and respond to a wide range of advanced threats.
Hands-on cybersecurity expertise
Having an expert in threat detection and incident response on staff isn’t common practice for most organizations. By working with LevelBlue’s team of security experts, operating in concert with internal IT teams, organizations gain the immediate expertise of seasoned analysts that have seen the USM platform deployed in hundreds of other customer environments.
Enhanced security at a fraction of the cost
Organizations that see the value of a SIEM know all too well the cost and complexity of establishing and maintaining it. LevelBlue Managed Threat Detection and Response provides organizations with a fast and simple SIEM implementation in a goal of 30 days thanks to our high touch service delivery model and SaaS platform deployment, resulting in a faster time to value.
What differentiates your managed SIEM offering?
LevelBlue Managed Threat Detection and Response is based on the LevelBlue USM platform which combines essential security capabilities, supports an extensible security architecture through integrations with other IT and security tools using the AlienApps framework, and combines continuous threat intelligence, threat detection, and cybersecurity analysts to help detect and respond to threats.
What does managed SIEM cost?
The monthly cost of our managed SIEM as part of our MDR offering starts at just $6,695 per month. Taking only a fraction of the time and expense of establishing a SIEM internally, LevelBlue's MDR offering provides organizations with people, processes, and technology for less than you can implement SIEM yourself, providing a fast return on your SIEM investment.
Get a quote
We're here to help! Complete the form and we will be in touch soon.