A way to manage too much data
To protect the business, security teams need to be able to detect and respond to threats fast. The problem is the average organization generates massive amounts of data every day. Information floods into the Security Operations Center (SOC) from network tools, security tools, cloud services, threat intelligence feeds, and other sources. Reviewing and analyzing all this data in a reasonable amount of time has become a task that is well beyond the scope of human efforts.
AI-powered tools are changing the way security teams operate. Machine learning (which is a subset of artificial intelligence, or “AI”)—and in particular, machine learning-powered predictive analytics—are enhancing threat detection and response in the SOC by providing an automated way to quickly analyze and prioritize alerts.
Machine learning in threat detection
So, what is machine learning (ML)? In simple terms, it is a machine's ability to automate a learning process so it can perform tasks or solve problems without specifically being told do so. Or, as AI pioneer Arthur Samuel put it, “. . . to learn without explicitly being programmed.”
ML algorithms are fed large amounts of data that they parse and learn from so they can make informed predictions on outcomes in new data. Their predictions improve with “training”–the more data an ML algorithm is fed, the more it learns, and thus the more accurate its baseline models become.
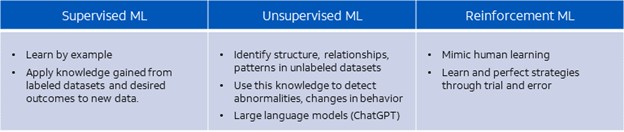
While ML is used for various real-world purposes, one of its primary use cases in threat detection is to automate identification of anomalous behavior. The ML model categories most commonly used for these detections are:
Supervised models learn by example, applying knowledge gained from existing labeled datasets and desired outcomes to new data. For example, a supervised ML model can learn to recognize malware. It does this by analyzing data associated with known malware traffic to learn how it deviates from what is considered normal. It can then apply this knowledge to recognize the same patterns in new data.
 Unsupervised models do not rely on labels but instead identify structure, relationships, and patterns in unlabeled datasets. They then use this knowledge to detect abnormalities or changes in behavior. For example: an unsupervised ML model can observe traffic on a network over a period of time, continuously learning (based on patterns in the data) what is “normal” behavior, and then investigating deviations, i.e., anomalous behavior.
Unsupervised models do not rely on labels but instead identify structure, relationships, and patterns in unlabeled datasets. They then use this knowledge to detect abnormalities or changes in behavior. For example: an unsupervised ML model can observe traffic on a network over a period of time, continuously learning (based on patterns in the data) what is “normal” behavior, and then investigating deviations, i.e., anomalous behavior.
Large language models (LLMs), such as ChatGPT, are a type of generative AI that use unsupervised learning. They train by ingesting massive amounts of unlabeled text data. Not only can LLMs analyze syntax to find connections and patterns between words, but they can also analyze semantics. This means they can understand context and interpret meaning in existing data in order to create new content.
Finally, reinforcement models, which more closely mimic human learning, are not given labeled inputs or outputs but instead learn and perfect strategies through trial and error. With ML, as with any data analysis tools, the accuracy of the output depends critically on the quality and breadth of the data set that is used as an input.
A valuable tool for the SOC
The SOC needs to be resilient in the face of an ever-changing threat landscape. Analysts have to be able to quickly understand which alerts to prioritize and which to ignore. Machine learning helps optimize security operations by making threat detection and response faster and more accurate.
ML-powered tools automate and improve the analysis of large amounts of event and incident data from multiple different sources in near real time. They identify patterns and anomalies in the data and then prioritize alerts for suspected threats or critical vulnerabilities that need patching. Analysts use this real-time intelligence to enhance their own insights and understand where they can scale their responses, or where there are time-sensitive detections they need to investigate.
Traditional threat detection methods, such as signature-based tools that alert on known bad traffic can be augmented with ML. By combining predictive analytics that alert based on behavioral anomalies with existing knowledge about bad traffic, ML helps to reduce false positives.
ML also helps make security operations more efficient by automating workflows for more routine security operations response. This frees the analyst from repetitive, manual, and time-consuming tasks and gives them time to focus on strategic initiatives.
New capabilities enhance threat intelligence in USM Anywhere
The USM Anywhere platform has long utilized both supervised and unsupervised machine learning models from BlueLabs and the BlueLabs Open Threat Exchange (OTX) for most of its curated threat intelligence. The Open Threat Exchange is among the largest threat intelligence sharing platforms in the world. Its more than 200,000 members contribute new intelligence to the platform on a daily basis.
BlueLabs uses ML models in several ways, including to automate the extraction of indicators of compromise (IOCs) from user threat intelligence submissions in the OTX and then enrich these IOCs with context, such as associated threat actors, threat campaigns, regions and industries being targeted, adversary infrastructure, and related malware.
The behind-the-scenes capabilities in USM Anywhere have been reinforced by new, high-value machine learning models to help security teams find today’s most prevalent threats.
These new models help the platform generate higher-confidence alerts with less false positives and provide advanced behavioral detections to facilitate more predictive identification of both insider and external threats. Its supervised models can identify and classify malware into clusters and families to predict behaviors. They can also detect obfuscated PowerShell commands, domain generation algorithms, and new command-and-control infrastructure.
Since the platform has an extensible architecture, new models can be introduced as the threat landscape dictates, and existing models can be continuously refined.
For more on how machine learning is transforming today’s SOC and to learn how the USM Anywhere platform’s own analytics capabilities have evolved, tune in to our webinar on June 28.