Stories from the SOC is a blog series that describes recent real-world security incident Investigations conducted and reported by the LevelBlue SOC analyst team for LevelBlue Managed Threat Detection and Response customers.
Executive summary
Malware infections are common and are often missed by antivirus software. Their impact to critical infrastructure and applications can be devastating to an organization's network, brand and customers if not remediated. With the everchanging nature of cyberattacks, organizations need a layered security strategy. They shouldn’t depend solely on a single layer of security to keep them protected. A multi-layered approach can help to provide anything that slips through the cracks is caught before it effects their business.
The LevelBlue Managed Threat Detection and Response (MTDR) analyst team received an alarm indicating detection of a potentially malicious executable on a customer's SQL server that was presented as mitigated by their antivirus software. Despite the mitigated status, the team completed more analysis and discovered a history of similar events on the host. Based on the review of the server's event history, the team determined the threat was not mitigated and engaged the customer for remediation. MTDR served as the second layer of defense for this customer, quickly detecting a threat that slipped through the cracks before any damage was done.
Investigation
Initial Alarm Review
Indicators of Compromise (IOC)
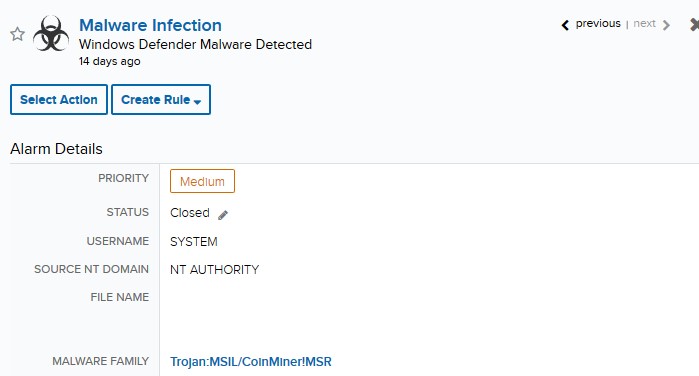
The initial alarm surfaced as the result of multiple events indicating that malware had been detected, removed, and no longer posed a threat to our customer's SQL server.
Expanded Investigation
Alarm Detail
Malware infection alarms are common, but anti-malware software ordinarily attends to malicious files effectively, not requiring any further action. Upon review of the server's alarm and event history, the team found that similar ‘Malware Detected' alarms were observed days before. The older alarms were isolated, first-time occurrences and were successfully mitigated by the security controls the customer had in place. These alarms were closed as auto-mitigated.
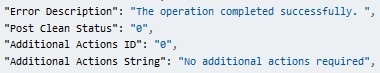
Response
Building the Investigation
Reviewing instances of this nature should be considered standard practice. A detailed history of the involved asset or of others affected by similar malware usually serve as indicators of a persisting malware infection.
Armed with historical context, we concluded this was likely a persisting malware infection affecting this server. All of the identified files, alarms, and events were gathered into an Investigation and presented to the customer with a recommendation to perform extensive scans on the asset at their earliest convenience.
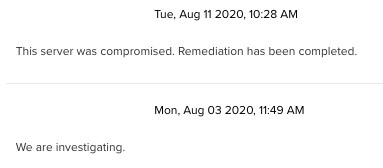
Customer Interaction
The customer began their investigation shortly following the creation of the Investigation and the notification from our team. They confirmed the server had been compromised and were able to remediate the infection soon after.
This incident serves as a reminder on why centralized logging and threat detection is important; the server's detailed history allowed us to conclude that there was a compromise despite anti-malware logs stating no further actions were required for mitigation.