The proliferation of cloud computing, mobile device use, and the Internet of Things has dissolved traditional network boundaries. Today, the network perimeter has evolved as workloads have moved to the cloud while non-managed, mobile devices have become the norm rather than the exception. The location of applications, users, and their devices are no longer static. Data is no longer confined to the corporate data center. Gaps in visibility and protection continue to widen as the attack surface evolves, forcing companies to bolt on multiple, disconnected tools to see and secure everything
A Zero Trust cybersecurity approach removes the assumption of trust from users and networks. It focuses on securely accessing resources regardless of network location, user, and device, enforcing rigorous access controls, and continually inspecting, monitoring, and logging network traffic. This requires data-level protections, a robust identity architecture, and strategic micro-segmentation to create granular trust zones around an Organization’s digital resources.
Zero Trust evaluates access requests and network traffic behaviors in real-time over the length of open connections while continually and consistently recalibrating access to the organization’s resources. Designing for Zero Trust enables enterprises to securely accommodate the complexity of a diverse set of business cases by informing virtually all access decisions and interactions between systems.
Organizations must approach a Zero Trust cybersecurity model with the tenet that any endpoint connecting to a network should not be trusted by default. With Zero Trust, everything - including users, devices, and endpoints —must be appropriately verified before allowing access to the network.
The protocols for a Zero Trust network ensure that specific rules are in place to govern the amount of access granted and are based upon the type of user, location, and other variables. If the security status of any connecting endpoint or user cannot be resolved, the Zero Trust network will deny the connection by default. If the connection can be verified, it will be subject to a restrictive policy for the duration of its network access.
Zero Trust networks operate under the least-privilege principle, in which all programs, processes, devices, or users are limited to the minimum privileges required to carry out their functions. Access rights don’t need to be too restrictive as they are balanced against privileges that can range from full access to no rights at all, depending on the circumstances. Think of it like the government or military’s “need-to-know” policy.
It’s essential to distinguish that Zero Trust is not a technology and a holistic approach to network security. Automated technology is a necessary tool for obtaining access, scanning and assessing threats, adapting to behavior changes, and continually re-evaluating confidence in communications. However, achieving Zero Trust Architecture (ZTA) in today’s threat landscape does require some form of automation, especially in support of dynamic policy, authorization and authentication.
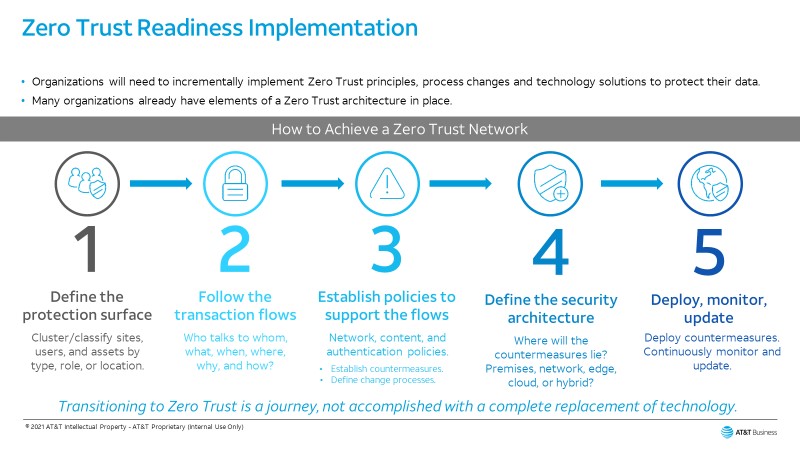
The Zero Trust journey
Everyone can agree that implementing a Zero Trust Architecture can stop data breaches. Yet Zero Trust Architecture means different things to different people because many organizations already have certain aspects of Zero Trust in place. A Zero Trust Architecture can be designed and executed in several different ways. The journey will depend on an Organization’s use cases, business flows, risk profile, and the business function of the network.
Many organizations have found, traditional detection and prevention technologies are no longer sufficient to mitigate the threats posed by opportunistic actors. Information into how previous attacks were carried out only provides so much. The key is always to plan for the worst and assume breach. This means organizations need to consider that all networks – and their applications and devices – are insecure and that the organization has already been breached. Both users and devices must be continuously authenticated and granted access to resources through disciplined verification.
To help support this, we recommend that organizations aim to implement a holistic Zero Trust approach that focuses on safeguarding critical digital resources and assets. As I mentioned previously, no one solution will get organizations there, but focusing on identity management and Zero Trust segmentation will launch enterprises in the right direction.
Equally, from a network perspective, visibility into communication across the network is vital to ensure the appropriate segmentation policies are deployed.
Zero Trust can help enterprises become more resilient, reduce cyber risk, and drive digital transformation initiatives to move their business forward when done in the right way.

Zero trust network assessment
Zero Trust Readiness Assessment is designed for customers who need to evaluate their current state information security program and its maturity in attaining Zero Trust.
Learn moreImplementing Zero Trust
The ideal security strategy against ransomware must start with a Zero Trust model. Organizations that adopt the Zero Trust model can experience the right mix of authentication and micro-segmentation to create a much more challenging barrier for attackers to deal with when targeting any organization.
By utilizing Zero Trust and its core foundations of micro-segmentation and enforced authentication via Identity Providers, organizations can fully visualize networks and resources to ensure relevant least-privilege and secure access to corporate resources and control all aspects of all aspects network security across cloud and on-premise applications and services. Zero Trust provides the visibility, control, and threat inspection capabilities necessary to protect networks from ransomware, targeted attacks, and the unauthorized exfiltration of sensitive data. Every organization looking to establish secure “trust boundaries” according to the Zero Trust security model can improve their overall security posture.
Cybersecurity is a big priority for organizations today and there is increased engagement at the board level. The #1 question ends up being, if people get compromised, how do make sure that the lateral movement doesn't happen? The answer is simple. Don't connect people to your network, don't build a moat with firewalls and VPNs, focus on a zero-trust strategy and implementation, where you connect users to applications, not the network.