This blog was written by an independent guest blogger.
Even though SecTor had to be entirely online this year due to our unusual international circumstances, there have been plenty of excellent talks from many experienced cybersecurity professionals. The talks took place over the course of two days, October 21st and 22nd. Last time I covered the talks I attended on day one. Interestingly enough, the talks all had to do with threat detection and analysis. Maybe that’s just what I’m fixated on these days.
The talks I attended on the second day all covered matters businesses must be aware of these days and well into the future. On day two, I learned a lot about how to talk to non-technical executives about security, the unique challenges of cloud security, and the legal implications of cyber threats. Enjoy!
How to Talk to the Board About Cybersecurity
The first talk I attended on the second day was presented by Jeff Costlow, a CISO with nearly 25 years of industry experience. This is the description of the talk from SecTor’s web app:
“With the sudden shift of the global workforce from in-office to remote, IT teams quickly transformed their operations to accommodate the new realities of business — including large-scale adoption of work-from-home technologies, heightened activity on customer-facing networks, and greater use of online services. While these examples of agility allowed business to continue, they also greatly increased the risk of misconfigurations and cyberthreats. Now, it’s looking like they could be here to stay for a while. On top of that, bad actors have wasted no time trying to exploit new vulnerabilities. In the past several weeks, we’ve seen ransomware attacks affect several major organizations. These attacks come on the tail of a surge of attacks across the board brought on during the pandemic, as hackers scanned and took advantage of new workloads, and vulnerable VPN connections and misconfigurations left the gates to the network open.
When attacks like these make headlines, panicked board members have one question for CISOs: how can we be sure that won’t happen to us? Drawing from nearly 25 years of experience in the security industry, Jeff Costlow, CISO at ExtraHop, will share his top strategies for CISOs to lead board-level conversations about risk management amidst the stark new realities of IT.”
When risk enters an organization through devices that the IT department cannot control, securing a network becomes very difficult. Any devices and applications that connect to the network that administrators can’t administrate are considered to be “shadow IT.” This is often a consequence of bring-your-own-device habits, but not always.
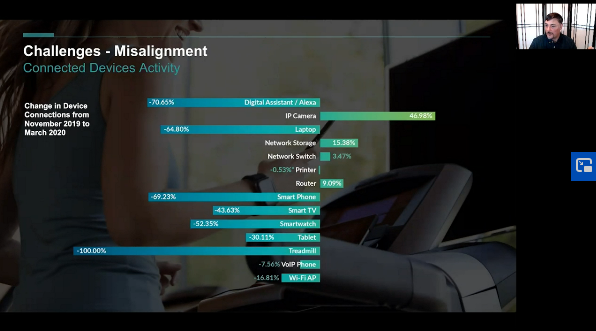
Costlow discussed the implications of shadow IT:
“All you have to do is Google or use the search engine of your choice. Search ‘shadow IT horror stories,’ and you will find a ton of these. There is the laptop that runs underneath someone's desk. It turns out it's a business critical piece of software that everyone's using, and it's just running on a laptop under a desk somewhere.
There are also plenty of stories. These are some of my favorites the ones about somebody just wanted to get their job done. And so they started forwarding all their business email to their Google account or their Yahoo account or something like that. Or maybe a personal Dropbox use. One of my favorites is unapproved chat clients. Or an even worse, operating those chat rooms. This is sometimes called ChatOps. We're inside a chat room, you set up robots and you make sure that things are happening and you can automate processes through a chat robot.
Those sorts of things are great because they get the job done right? This is innovation. They are doing what they need to get their job done and making everything work better. However, they haven't taken the secure approach to it. And that's where that's where my objections fall into it right talk to me. Let's talk about this. You want to run ChatOps. That's great. What tools do we have in order to enable you to use that? How can I make sure that the date of its going across that is not just somewhere out there that it's well secured. And what I found is that in my professional life and my personal life, the greatest changes of the greatest challenges come at the times of the greatest stress. I think that makes sense, but it certainly doesn't make the changes any less stressful.”
As much respect as I already had for CISOs, now I respect them even more!
Security Transformed
Two of the more significant ways IT has changed in recent years is the greater adoption of cloud services, and more people working from home. The unusual circumstances of 2020 have accelerated this trend even faster. Check Point VP Avi Rembaum discussed what this means for cybersecurity in his talk, “Security Transformed.”
This is the description of the talk from SecTor’s web app:
“Preceding the outbreak of COVID-19 was a trend across industries to transform the traditional IT stack into a new form of computing, one that was focused on enabling agility and innovation while also delivering cost reduction. This shift sought to leverage public cloud and cloud-like development methods as well as infrastructure design. The effort to transform information technologies, like all changes, introduces new considerations, especially in the areas of cyber, information and network security. This session will highlight some of the most significant security implications of cloud transformation. The session will also suggest key security technologies and processes that government agencies and private enterprise should consider when embarking on a transformation program.”
During his talk, Rembaum discussed infrastructure-as-a-service and DevOps matters, among other things:
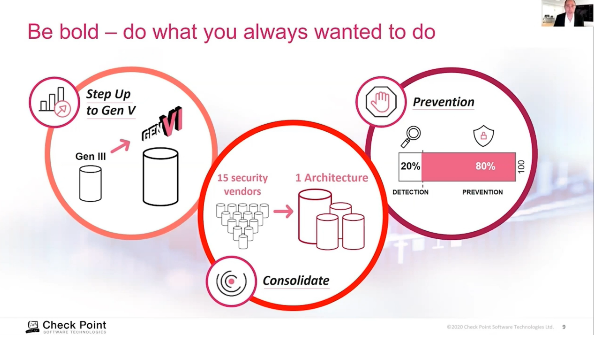
“Time becomes a key component of our security strategy and therefore we have to find ways of modifying transformation. I mean, in the traditional IT area, security teams, everything. Both in terms of the classification, and also in terms of building task control methods and user controls, and putting the right types of networking infrastructure in place. All of that is owned within the IT space as something that the IT team members of the agency or the organizational systems that they put in place.
This transformation process however removes that level of control when we start leveraging public infrastructure-as-a-service providers, like Azure or Google Cloud Platform. The infrastructure itself, the network itself starts to move over.
Let me go even deeper down or farther down this path of transformation. For example, platform-as-a-service. We lose control over many of the systems onto which applications operate and then the DevOps teams, or the concept of the security team itself also transition, such that the regular vulnerability of the structure itself. The selection of the system, the overall management of operational security within the third party organization-- those are controlled by others and this concept has very significant impact on the way in which security operates.
So what would our guidance to companies and organizations and agencies ends up being is that this requires a real a very well-thought-out transformation process? What are the critical systems what areas of the deliveries and the service is that an agency has that are that are critical to the day-to-day operation? What type of risk do I see with them and what types of goals do I have in place?”
Can't Stop This Train - Top Cases in Privacy Litigation
The final talk I attended on the final day was actually presented by a lawyer, Civil Litigator Stanislav Bodrov. Bodrov specializes in the legal implications of cybersecurity for businesses. His talk focused on privacy litigation.
This is the description of the talk from SecTor’s web app:
“One of the core purposes of cybersecurity is to protect data gathered by an organization. Numerous countries around the world have enacted statutes to force organizations to protect their users’ data. Although organizations are making efforts to comply with regulations and implementing revolutionary cybersecurity products into their operations, we continue to see breaches of businesses of all sizes.
It has been over two years since the implementation of the GDPR in the EU, the CCPA in California, and the amendments to the Canadian PIPEDA. We will review and highlight key cases in Canada and explore what has come of these regulations. This will include a discussion of who is being sued, the key takeaways from these lawsuits, and what the future looks like. Finally, we will look at how lawsuits outside of the Country are shaping the Canadian landscape.”
Bodrov discussed the importance of privacy impact assessments for companies:
“What that means is you look for your risk management practices and beliefs of risk, Inventory of all the type of risks that your company is vulnerable to like creating an inventory of the number of servers that you have. The number of users that you have, the number of the widgets, basically any ingress point into your network. You need to be aware of those. Create an inventory of all the users in your organization, and more importantly, identify risks your organization has. Rank them according to their impact and severity.
More importantly, you really have to determine who is in charge of your organization. So read a chain of command. Set up a time in order to determine who's in charge. You need to know who is going to be making a decision before breaching an app. For instance, who in the organization is responsible for making a call regarding a ransomware attack? Is your organization going to make ransomware payments or is it not? Who's responsible if that individual is on a plane and not accessible at the time of the breach occurs? Who is second-in-command, who is delegated that power? All of these things are needed to be considered before a breach occurred. When breaches occur, you don't want to be making those decisions on a whim. Additionally, you need to know who has the contact information of the individuals.”
I was sad that I couldn’t attend all of the talks. Some of the timeslots had three or four talks at once. But I enjoyed what I saw. I’m excited to share my experiences with you. And I look forward to covering SecTor 2021 next year, whether it’s online or offline!