Introduction
Limited budgets, limited staff, limited time. Any security professional will have dealt with all of these repeatedly while trying to launch new initiatives or when completing day-to-day tasks. They are possibly the most severe and dangerous adversaries that many cybersecurity professionals will face. They affect every organization regardless of industry, size, or location and pose an existential threat to even the most prepared company.
There is no easy way to contain them either, since no company has unlimited funding or time, and the lack of cybersecurity professionals makes filling roles incredibly tricky. Even in major cities like Los Angeles, finding staff that meets your requirements is a challenge. According to the website Cyberseek, there are around 22,000 available jobs in the LA area with a supply/demand ration of 1.5. With a national average for all other positions at 4.9, you begin to see why staffing these roles can be a challenge.
Resource prioritization
So how can organizations cope with these natural limitations? The answer is resource prioritization, along with a healthy dose of operational improvements. By identifying areas where processes can be streamlined and understanding what the most significant risks are, organizations can begin to help protect their systems while staying within their constraints. This task is not quite as impossible as it seems. The first step is to make sure you understand the following components:
- The goal of the organization
- Responsibilities and operations of the target department
- Any regulatory or internal requirements
Once you know those points, you can begin the actual work. The best way to find areas to improve processes is to work directly with the specific departments. While the focus of this blog is IT or security departments, this process can be used pretty much anywhere. Through a mixture of interviews and process documentation, you can begin to assemble a picture of how departments operate.
The graphic below outlines the basic review and improvement cycle that can be employed when conducting this type of work. Later in this blog is a more in-depth multi-level strategy that can be employed later down the line or immediately for companies that want to engage in a more long-term assessment and improvement cycle. As always these steps can also be integrated into any existing review or audit procedures as well.

Working with frontline employees is one of the most effective ways to understand what occurs in your organization. These employees will almost always be able to provide ideas or suggestions on how to improve workflow and general operations. All proposals should be reviewed for accuracy and effectiveness but getting data straight from the source is a great way to develop actionable plans.
It almost seems too simple to work. Can asking questions like "What can we do better" or "Where do we spend the most time" really lead to a better protected company? Of course! Freeing up your staff so they have more time to focus on security concerns is one of the most direct ways to combat the three-headed hydra introduced in the beginning. The hardest part of this process is finding the right employees and asking the right questions.
When it comes to selecting the employee(s) you talk to, you must pick the ones responsible for the work in question. If, for instance, you wanted to streamline or improve the ticketing system, you should talk to the service desk staff and manager. The closer you get to the actual work being done, the more valuable the insight you gain. Below are some sample questions you can use in these interviews:
- What are your primary day-to-day tasks?
- What task takes the most time for you to complete?
- Are there any repetitive tasks you conduct? (e.g., answering the same question, or resolving the same issue)
- Do you need to interact with other departments regularly?
- (If yes) Are there any issues in communication or response times for these tasks?
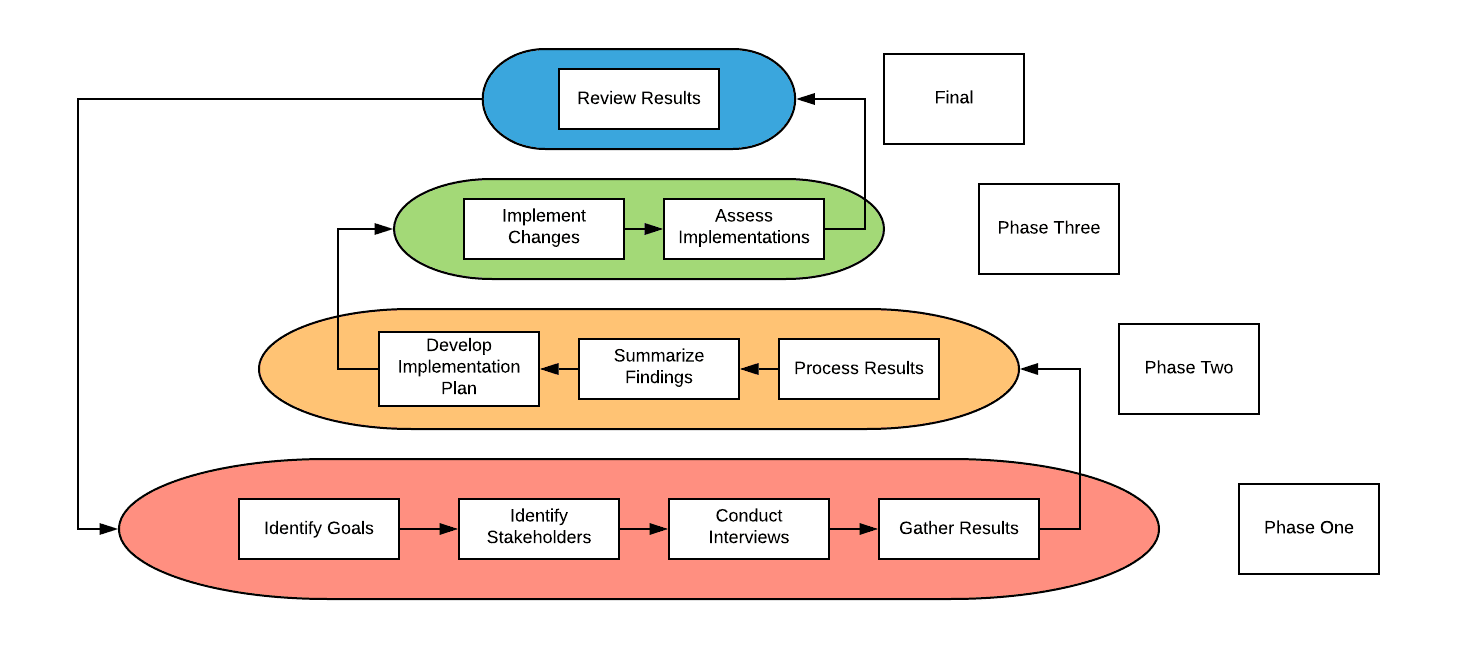
This method can help identify bottlenecks in your organization that is impacting your teams' ability to execute on their tasks. Implementing cybersecurity is quite a time-consuming task, so finding areas where you can save time or money allows you to reallocate those resources to security instead. Reducing the immediate cost impact of implementing cybersecurity programs can also aid in getting approval from management since adopting security would no longer add as many additional costs.
Conclusion
Implementing security is quickly becoming the top priority for organizations around the world. Trying to balance the need for protection against existing duties and budgets is difficult and, in some cases, impossible. By looking for ways to free up existing time, money, and staff security needs can be met without exceeding existing constraints. As security professionals, we must do our utmost to maintain our organizations to the best of our abilities.
This means finding creative ways to solve problems while continuing to uphold existing responsibilities. In a perfect world, cybersecurity would be prioritized, with the necessary funding and staffing dedicated to it, but unfortunately, that is not the world we live we occupy. Hopefully, by following the steps above, you can identify areas that will not only improve the workflow of the organization but also free up the necessary resources to address additional requirements introduced by security initiatives.