Remember Cryptolocker? While it might not be front-page news as of late, ransomware continues to wreak havoc in environments around the globe. It is also still very lucrative to extort money this way. This particular variant has netted over $75,000 since February, according to a recent FireEye report. While that pales in comparison to the estimated $3 million that cryptolocker has brought in since 2013, it is still quite a haul, given its recent inception and relatively limited distribution.
TeslaCrypt is spread via the Angler exploit kit (which we also detect) and encrypts a wide variety of system files. These can include pictures, spreadsheets, and other sensitive documents. Users have even reported save files of popular online games falling victim to the attack.
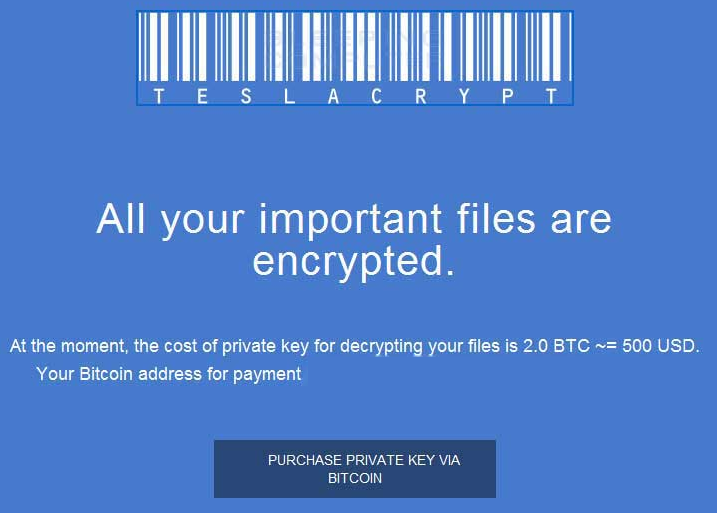
In the unlikely event that you do encounter this malware, you are presented with a notification and prompted to pay immediately. This can range anywhere from $150 to $1000 and, like most locker variants, require an anonymous form of payment like bitcoin or PayPal cash cards.
Having this happen to your personal computer is bad enough but the potential impact to your organization (especially when you handle payments or other sensitive client information) is immeasurable. To add insult to injury, we have seen some instances where the victim paid the full ransom only to find that the decryption didn’t even work.
The good news is that the AlienVault Labs team has already developed Threat Intelligence to aid in spotting this type of attack. This includes updates to the correlation rule sets identifying TeslaCrypt, CryptoLocker, and CoinMiner.
Ransomware’s Impact on you
- Encrypts your important files with a nearly unbreakable algorithm and demands payment (usually around $500). Once payment is received, you receive a key that will allow you to unlock the files.
- These types of threats can spread quickly if they go unnoticed.
- If this virus were to infect machines with sensitive data, you would likely be forced to pay.
- If payment is not received, the key is usually destroyed, leaving the files nearly impossible to recover.
How USM Helps
- Allows you to detect the threat quickly and mitigate the issue before spreading to other systems in your environment
- Identifies the IPs of malicious websites users are going to (or being redirected to) so you can take some short-term steps to block access and prevent attacks on the rest of your users
AlienVault Labs has already released the following threat intelligence updates
- System Compromise, Malware infection, Teslacrypt
- System Compromise, Trojan infection, CryptoLocker
- System Compromise, Malware infection, CoinMiner