This article was written by an independent guest author.
What does cybersecurity testing really mean?
Your organization may boast all the best cybersecurity hardware, software, services, policies, procedures and even culture. If this is the case, you’re way ahead of the curve. But no matter how confident you are about your overall cybersecurity posture, how can you really know?
Knowing is where cybersecurity testing comes in. Cybersecurity testing is all about validating that you’ve got all the security controls in place and that they are working correctly.
The value of regular cybersecurity testing
The main reason testing is so critical is because cybersecurity is so dynamic and constantly shifting. The threat landscape today may be completely different from what it is next month or even next week.
Sure, your teams might be working diligently to implement secure solutions frequently. But gaps are always a possibility: it could be a lack of understanding about new threats, perhaps it’s insufficient training, or maybe people have made mistakes. Or, what if systems have been unintentionally (or intentionally) misconfigured?
Periodically, you’ll need to get an internal or external third-party to test your systems to identify gaps and misconfigurations you may have missed. Having a third-party that brings a fresh perspective and expertise is critical in finding those little details that often go unchecked.
What constitutes a “test” in cyber?
A cybersecurity test can take many forms, leveraging different validation methods and levels to assess a company’s cybersecurity weaknesses. The most common tests you’ve probably heard about are penetration tests and vulnerability assessments.
People often confuse these two complementary forms of cybersecurity tests. Vulnerability scanning typically leverages software and automated processes to look for known vulnerabilities in various systems, and reports are generated on risk exposure. Penetration testing (or pen tests) leverages manual processes and is usually conducted by cybersecurity expert or experts as they find holes and exploits within your system architecture.
Essentially, all types of cybersecurity tests involve internal teams or third parties performing various activities and assessments that validate your security posture. When complete, testers create reports based on their findings so your organization can mitigate the risks and fix any problems.
The most common types of cybersecurity tests
To test the effectiveness of your cybersecurity controls, you have many options available, including vulnerability assessments and penetration tests mentioned above.
We’ve included a quick summary of each below.
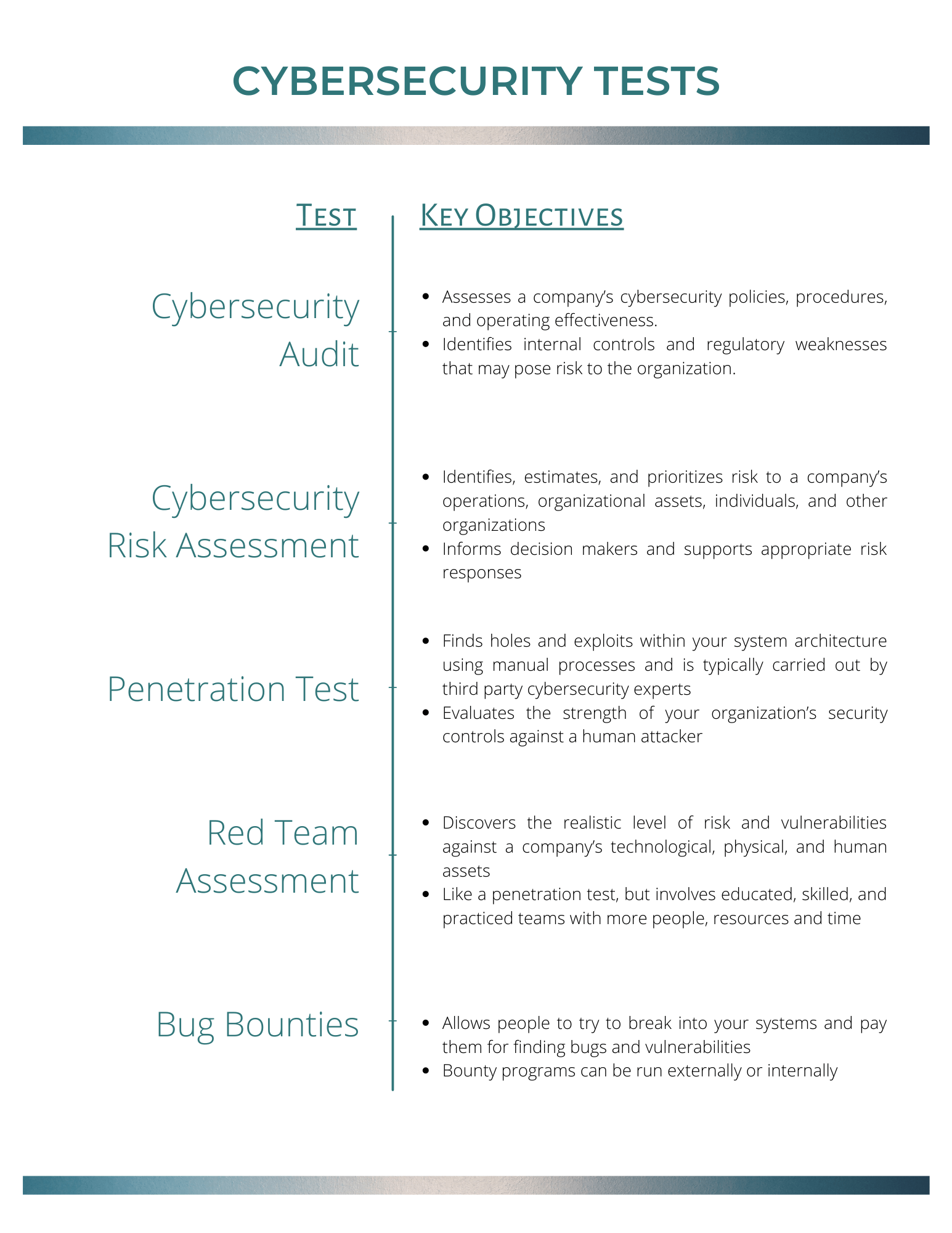
A cybersecurity audit is an assessment of a company’s cybersecurity policies, procedures, and operating effectiveness. The purpose of the audit is to identify internal controls and regulatory weaknesses that may pose risk to the organization.
Some audits provide details as to whether a control is effective or ineffective, while other audits won’t go into that detail. Auditors will typically interview key personnel and review system reports to determine if you have the right controls in place. In some cases, auditors may test your systems, depending on the access provided to them.
Auditors will always employ industry-standard best practices and adjust the audit to match your organization and industry.
Cybersecurity risk assessment
A cybersecurity risk assessment is much like an audit but may take things to the next level by determining the effectiveness of security controls. The purpose of the risk assessment is to identify, estimate, and prioritize risk to a company’s operations, organizational assets, individuals, and other organizations.
Vulnerability assessments fall into this category. They can determine, based on outstanding patches and/or common misconfigurations, the extent to which systems and sensitive information are vulnerable to compromise or attack.
Penetration tests
While vulnerability assessments are performed using software, penetration tests use manual processes to find holes and exploits within your system architecture. Pen tests are more effective when carried out by third-party security experts.
Penetration tests dig deeper than vulnerability assessments, examining exploitable configurations and interactions between devices and systems (and where they are located). Pen tests attempt to break into your systems, showing you how an attacker might compromise your system and also use it to access other systems or steal data.
Red Team Assessment
Red team assessments are much like pen tests but are usually conducted with a team of very educated, skilled and experienced individuals with more time, people and resources at their disposal. Red teams may operate with different objectives and may provide additional services, and functions than pen testers.
As such, because they may take pen testing a step further with their value adds, the costs for red teams can be higher for an organization.
Bug bounties
Why do your own vulnerability assessments when you can have the public at large do it for you? That’s the theory behind bug bounties, where you allow people to try to break into your systems or find vulnerabilities and pay them for their findings.
Large companies like Apple, Microsoft and Google all have a public bug bounty program.
Some bug bounty programs can be run internally, and in some cases, companies will outsource bug bounty programs to a third-party like Bugcrowd.
How often should a business have cybersecurity testing done?
It’s crucial to understand that cybersecurity testing represents a “moment in time” assessment. As the threat landscape expands and the attack surface widens in this accelerated business climate, cybersecurity testing should be conducted regularly.
For many organizations and industries, compliance requirements and mandates require cybersecurity tests to be done frequently anyway.
Generally speaking, the level of cyber testing a business needs and the frequency with which it is conducted will be hugely impacted by the type of industry they are in. For example, industries like healthcare, retail and finance have much more rigorous compliance needs, and therefore, more severe risk profiles to address compared to other industries.
For some industries, like manufacturing as an example, specific and frequent test cadences are probably overkill. In others, a quarterly cadence may be crucial.
There’s no specific rule that dictates how often an organization should be performing cybersecurity testing. If your company is in an industry that doesn’t require frequent testing, you should consider conducting some form of testing at least once per year.
Is cybersecurity testing too expensive?
For every industry, we cannot forget that if a breach occurs, the costs of dealing with the ramifications of the breach will almost always outweigh the costs of testing.
If you believe your company is too small to need cybersecurity testing, the numbers tell a different story. A 2019 Ponemon Institute study reports that 76% of US SMBs (small to medium sized businesses) have been targeted by a cyberattack. Throughout their business’s lifetime, 82% of U.S. respondents have experienced a cyberattack.
Unfortunately, a breach or attack for your organization is no longer a case of “if” but a case of “when.”
Rather than taking a reactive approach to security, being proactive—especially with testing—is the best way of addressing cybersecurity risk. A proactive approach puts you in a better position to understand your organization, systems, applications and your user customers.
Proactively testing your cybersecurity posture gives you the power to understand where your vulnerabilities are and how to mitigate them. That’s ultimately what cybersecurity is all about.