This blog was written by an independent guest blogger.
Dealing with the massive architecture of client-server networks requires effective security measures. Everyone has become painfully aware of all dangerous fishes roaming around the pool of the network, trying to get access to the system.
Having a weak password policy is a key vector for attackers to gain system access. However, admins can help protect password security of the wide-reaching network using Group Management Policy (GPO).
Let's get rolling about how we can configure Domain Password Policy for Active Directory.
But what's domain password policy?
To harden the client's passwords, Active Directory (AD) has a feature of default domain password policy. The policy says:
- Use encryption for passwords.
- Use long character passwords.
- Expire passwords after some time, and so on.
This policy helps to mitigate password attacks like brute force by pairing with several other policies like lockout policy.
Configure domain password policy
Password policies come under the group policy, which relates to the root domain. Follow these steps to configure the domain password policy.
- Run the 'gpmc.msc' command to open the Group Policy Management console in the Windows Server.
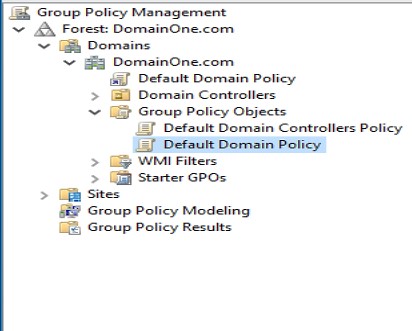
- Expand the window's left pane.
Group Policy Management -> Domains -> Group Policy Objects -> Default Domain Policy.
- Open the Group Policy Management Editor by right-clicking on the Default Domain Policy and select edit.
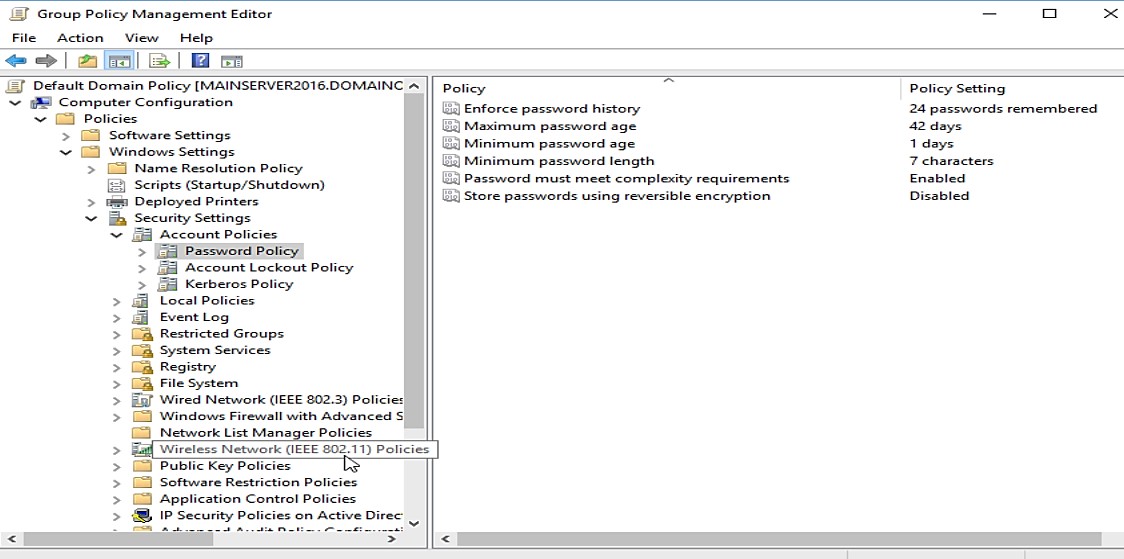
- A new window will pop up. Navigate to the Password Policy node from the left pane to see the policies on the right-side pane.
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
- Double-click any password policy you want to modify from the list.
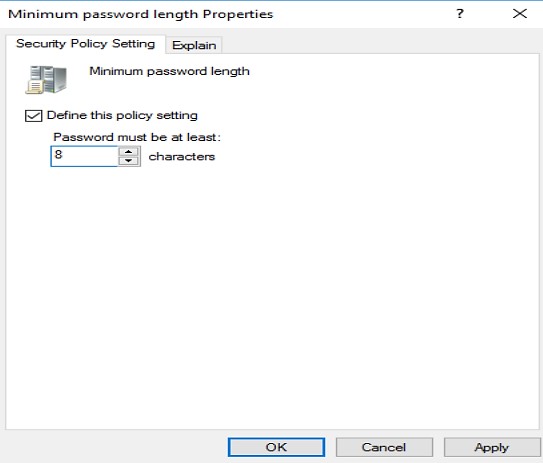
- I am selecting a Minimum Password Length policy.
Change the value -> Apply setting -> Click Ok.
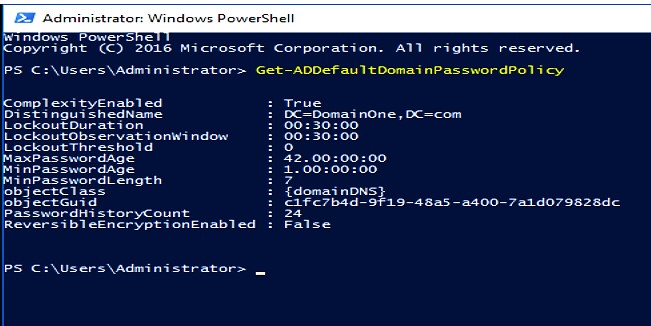
View domain password policy through PowerShell
- Search the PowerShell from the start -> Run it with admin rights.
- Enter the command -> Get-ADDefaultDomainPasswordPolicy
Guidelines for creating a password policy
The password policy must ensure that user account passwords are sufficiently unique, strong, and reset promptly. Several compliance regulations, such as PCI-DSS, HIPAA, SOX, NIST, and more, have set password policy standards.
The Password Policy Microsoft recommends is:
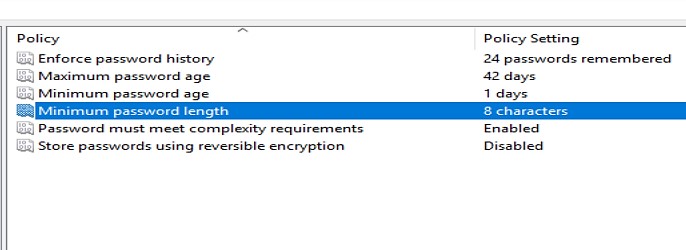
- Enforce Password History with a value of 24. It will help reduce the risks associated with password reuse.
- Based on the situation, set the Maximum Password Age to 30 to 90 days. A hacker will only have a short period to break a user's password and get admin rights to network services.
- We should set the Minimum Password Age to one day, as per Windows security baselines. When the duration is 0, you can change your password right away. That's not a good option to use.
- Set the Minimum Password Length to at least eight characters. An eight-character password is suggested for most situations as it's strong enough to offer protection while remaining concise for people to memorize.
- Enable Password Must Meet Complexity setting. This policy option, paired with an 8-character minimum password length, guarantees that a unique password has at least 218,340,105,584,896 distinct combinations. A brute force attack is challenging, but not unattainable, with this option.
- Disable Store Passwords Using Reversible Encryption. Enable it if you utilize CHAP through remote access or IAS or Digest Authentication in IIS.
It's a good practice to adopt the Windows recommendations, but you may also utilize options other than the Domain Password Policy.
- Passwords and lockout policies go together. The lockout policy prohibits hackers from employing brute-force attacks or dictionaries to acquire full rights to the network. If the hacker gets the username, he can attempt several password combos. The lockout will keep the amount of failed login tries to a minimum.
- If a user's password is about to expire, email notifications can act as a reminder. Users can receive email prompts when it's due to update their passwords before they expire.
- Admins should perform password audits periodically to prevent attacks from massive password dictionaries.
In a nutshell
Within a domain structure, users are the easy targets. The account login and password may be the only security precautions in place to secure their devices. Although the username may be simple to predict, we must not tolerate weak passwords.
Inside an AD domain, the Default Password Policy prevents users from setting simple passwords. However, you may want to change this password policy in rare situations because of restrictions or the usage of apps. Always follow best practices when changing the password policy options.