The USM Anywhere web user interface (UI) provides access to all the tools and capabilities that USM Anywhere makes available for managing the security of your organization’s network and the devices in it. From the USM Anywhere web UI, you can view all essential information about network devices, applications A software program that performs some collection of tasks on a computer or some other programmable device., user activity, and network traffic in your environment. You can begin monitoring Process of collecting all device status and event information and processing normalized events for evidence of vulnerabilities, possible attacks, and other malicious activity. information coming from devices and then go about defining orchestration rules to fine tune the behavior of your system. USM Anywhere includes by default correlation rules A correlation rule correlates incoming events based on previously defined relationships defined in the correlation directive, associating multiple events, of the same or different event types, from the same data source. to alert you of potential security issues and vulnerabilities.
The USM Anywhere web UI runs in a standard web browser. Your system administrator can provide the web address and credentials to log in Log in (verb): Process in which an individual gains access to a computer system after providing sufficient credentials to authenticate their unique identity. Login (noun): User credentials, typically a username and matching password. and access the features and functions appropriate to your role Tasks and responsibilities based on job description and position within an organization. A user's role is often used to define access to functionality and privileges to perform specific tasks and operations. in your organization’s security operation.
Note: The recommended screen resolution for viewing the USM Anywhere web UI is 1440 pixels wide.
When you first log in, the USM Anywhere web UI displays the main window.
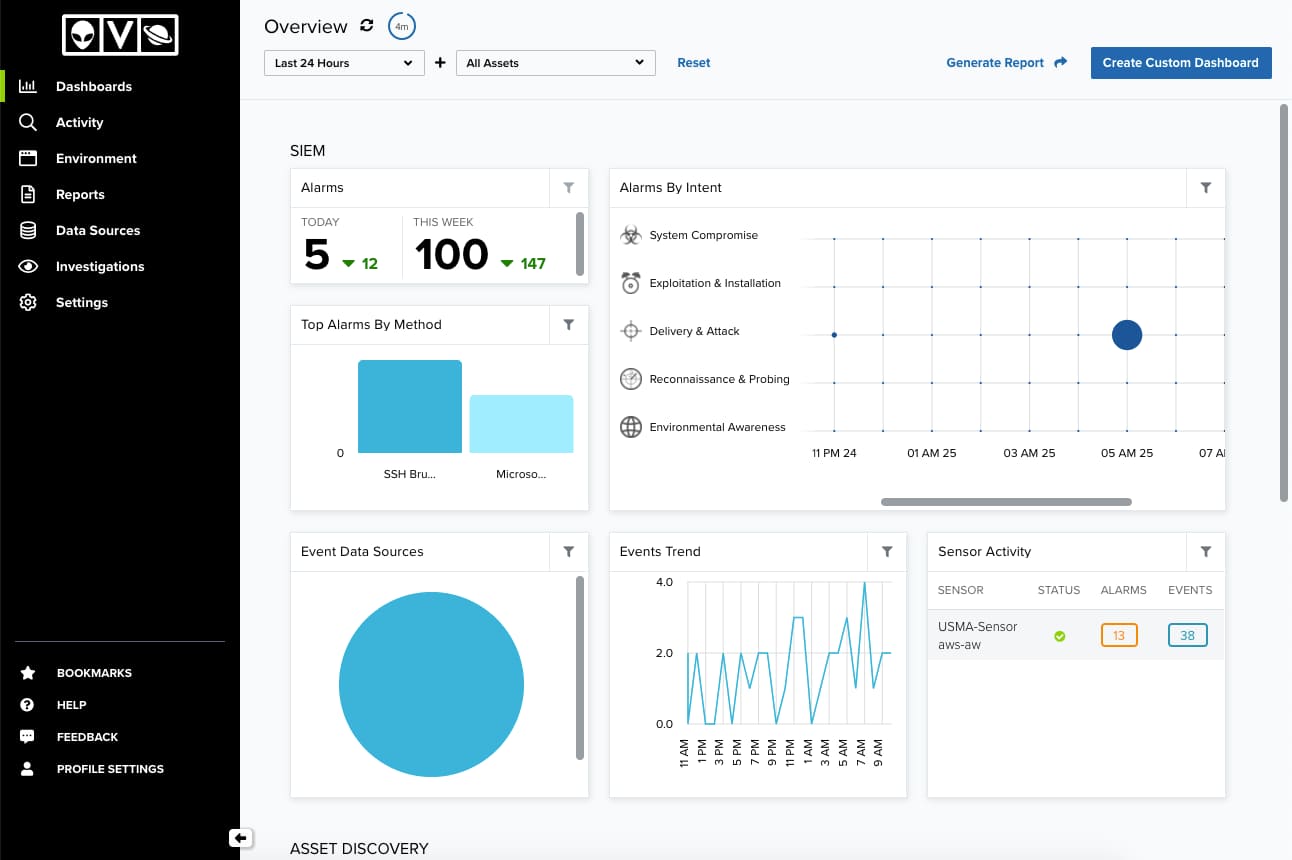
By default, the web UI displays a collection of high-level graphs and charts summarizing activity in your organization’s network. From this main window, you can select different menu options or click other links and buttons.
Important: You can also load the
The main navigable elements and expand selections are provided consistently through the web UI. Use the and
icons to expand or collapse the left navigation pane.
The primary menu provides access to the main functions or operations of USM Anywhere. These include:
- Dashboards. Provides charts, tables, and graphs. There are dashboards that will be displayed depending on the sensor Sensors are deployed into an on-premises, cloud, or multi-cloud environment to collect logs and other security-related data. This data is normalized and then securely forwarded to USM Anywhere for analysis and correlation. you have installed; there are also dashboards related to the AlienApp [[[Undefined variable Core.ProductBlueApps]]] extend the threat detection and security orchestration capabilities of the USM Anywhere platform to other security tools that your IT team uses, providing a consolidated approach to threat detection and response. you have configured and that will be visible if you have data for them. See USM Anywhere Dashboards for more information.
- Activity. Provides search, sorting, filtered selection, and visualization of Alarms Alarms provide notification of an event or sequence of events that require attention or investigation. and Events Any traffic or data exchange detected by LevelBlue products through a sensor or external devices such as a firewall.. See Alarms Management and Events Management for more information.
- Environment. Provides display and management of Assets An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers., Asset Groups Asset groups are administratively created objects that group similar assets for specific purposes., Vulnerabilities A known issue or weakness in a system, procedure, internal control, software package, or hardware that could be used to compromise security., and Configuration Issues An identified configuration of deployed software or features of software that is in use, which is known to be insecure.. See Asset Management, Vulnerability Assessment, and Configuration Issues Management for more information.
- Reports. Provides display and management of reports which are the result of export data that you can find in assets, asset groups, alarms, events, vulnerabilities, and configuration issues. You can also choose the format of the report (PDF and CSV). There are also Compliance and Event Type Templates. See USM Anywhere Reports for more information.
- Data Sources. Provides options to view and manage deployed USM Anywhere Sensors, the LevelBlue Agent, BlueApps, and Sensor Apps. See USM Anywhere Sensor Management, The LevelBlue Agent, USM Anywhere BlueApps Guide, The Graylog (GELF) Sensor App, The Syslog Server Sensor App, and Windows Event Collector Sensor App for more information.
- Investigations. Provides options to organize the information from your environment. See USM Anywhere Investigations for more information.
- Settings. Provides options to view and manage credentials and system events. There are administration options which let you manage users and asset fields, display the system status, schedule jobs, validate your OTX key, and manage orchestration rules. You can also display the data about your subscription and connect your USM Anywhere A SaaS security monitoring solution that centralizes threat detection, incident response, and compliance management across your cloud and on-premises environments. to USM Central A federation console that enables centralized security monitoring for multiple LevelBlue USM Anywhere and LevelBlue USM Appliance deployments. environments.
The secondary menu provides access to the system configuration, the user profile information, the help link, and the bookmarked items:
- Bookmarks. The
icon enables you to see and access alarms, events, or assets that you (or another user) bookmarked for easy access. The number on the icon indicates the number of items bookmarked.
- Help. The
icon includes the these options:
- Documentation: Links to online documentation
- Support: Links to the LevelBlue Support page
- Forums: Links to the LevelBlue Success Center
- Feedback. The
icon provides a direct communication with the USM Anywhere team.
- Profile Settings. The
icon shows your profile settings. You can change your email, full name, update your password, enable multi-factor authentication (MFA A method of access control in which a user is granted access only after successfully presenting several separate pieces of evidence to an authentication mechanism – typically at least two of the following categories: knowledge, possession, and inherence.) for the account, select your default landing page after you have logged in, configure an interval for auto-refreshing the dashboards and alarms pages, and the configuration of receiving alarm notifications. See Managing Your Profile Settings for more information.
The remainder of this guide describes best practices in performing common network security operations and provides step-by-step instructions for performing specific tasks. Following sections also describe the USM Anywhere web UI from which you can monitor network security and access all of USM Anywhere’s security operation features and functionality.
 Feedback
Feedback