USM Anywhere Trial Pre-Deployment Checklist
By conducting a USM Anywhere trial, you’ll quickly see real value in our solution. To prepare for your first trial call with an LevelBlue sales engineer, it’s important that you complete a basic deployment and configuration of the USM Anywhere Sensor. If you are unable to complete this prior to your scheduled call, please notify your LevelBlue sales representative at least 24 hours in advance to reschedule the call.
Important: At the end of your 14 day trial period, your trial implementation and all associated data will be deleted unless your trial license is converted to a production license before the end of those 14 days.
This checklist includes prerequisite requirements for deployments in the Amazon Web Services (AWS), Microsoft Azure, VMware, Microsoft Hyper-V, and Google Cloud Platform (GCP) environments.
Completing the prerequisite requirements enables LevelBlue to immediately validate your efforts and work with you to establish specific trial success criteria during the first trial call.
Trial Pre-Deployment Checklist for AWS, Azure, GCP, VMware, and Hyper-V
-
Sign up for the USM Anywhere Trial to receive an authentication code to deploy a USM Anywhere Sensor.
-
Review the requirements for the deployment type options and select the one that is a best fit.
Based on your selected deployment type, the Let's Get Started page provides an overview of the sensor deployment process.
-
Click the displayed download link (step 1 on the page) or navigate to the Sensor Downloads page on the LevelBlue website, and choose your deployment type.
-
Deploy the USM Anywhere Sensor:
-
AWS: Use the AWS CloudFormation stack from the template URL that you loaded (see Deploy the AWS Sensor for more information).
Note: There is an option under the Permissions section for choosing an IAM role. You can choose an IAM role that CloudFormation uses to create, modify, or delete resources in your stack; otherwise, the CloudFormation template uses the permissions defined in your account. You can skip this if you have permissions defined in your account that allow you to create resources in a stack.
- Azure: Use the virtual machine (VM) template from the URL (Azure Marketplace) that you loaded (see Deploy the USM Anywhere Sensor from the Azure Marketplace for details).
- GCP: Use the Google Cloud Deployment Manager template that you downloaded (see Deploying the GCP Sensor for more information).
- VMware: Use the
USM_sensor-node.ovffile that you downloaded to import and deploy the sensor VM on a VMware ESXi instance (see Create the VMware Virtual Machine for more information). - Hyper-V: Use the usm-anywhere-sensor-hyperv.zip package that you downloaded to create, configure, and start the sensor VM (see Create the Hyper-V Virtual Machine for more information).
-
-
Activate the sensor and provision your USM Anywhere instance:
- Enter the public IP address assigned to your sensor in your web browser and navigate to the activation user interface UI.
- (Optional.) Enter a sensor name and sensor description.
-
Enter the authentication code displayed in the Let's Get Started page.
-
Click Start Setup.
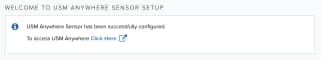
This activates the sensor and launches the USM Anywhere provisioning process, which takes approximately 15 - 20 minutes to complete. Upon completion, you’ll see a welcome message that provides an access link (Click Here).
-
Click the link and set the password to use for the default administrator of USM Anywhere.
With this initial login, you can get started with the Setup Wizard. You will also receive a welcome email that includes your URL for the hosted solution, as well as other information to help you set up USM Anywhere.
-
Click Get Started and complete the steps in the sensor Setup Wizard.
This is where asset discovery, network and cloud security monitoring, log management, and authenticated scanning immediately starts pulling in data for analysis:
-
AWS Sensor: Before you complete these steps, ensure that there is logging and connectivity within your AWS environment so that USM Anywhere can access the data during discovery and scanning.
- Ensure that there are AWS logging configurations, such as AWS Elastic Load Balancing (ELB), Amazon CloudWatch, and Amazon Simple Storage Service (S3) storage services.
- For Amazon Virtual Private Cloud (VPC) environments, ensure that there is network connectivity between VPCs (if you plan to monitor more than one). If the VPC does not use a public IP, you can monitor all assets in your networks using VPC Peering.
-
Azure Sensor: Before you complete these steps, make sure you have the Azure environment information that is required for connectivity.
- To retrieve your tenant ID, view this information on the Microsoft documentation site.
- To retrieve you Azure subscription ID (GUID), view this information.
- To create an application and obtain Azure credentials, view this information.
- To find your application key, view this information on the Microsoft documentation site.
- GCP Sensor
- VMware Sensor
- Hyper-V Sensor
-
-
Configure your network assets for Log Collection.
Note: For a successful trial, you should have a least one of these assets where you have Administrative credentials and you want to collect log data.
- (Optional.) Configure firewalls or other devices capable of exporting security logs using UDP syslog. This configuration requires Port 514 UDP and the “informational” level of syslog (or equivalent).
- Configure logs from Linux systems.
- Configure logs from Microsoft Windows systems.
-
Configure your assets for authenticated asset scanning.
During an authenticated scan, USM Anywhere performs a vulnerability assessment in addition to discovering what services or software packages are running on the assets. For all assets that you want to include, verify the requirements for the assets.
- Ensure SSH and Microsoft Windows Remove Management (WinRM) connectivity between the network where the sensor is deployed and your Linux or Windows hosts.
- Verify that WinRM is running on the Windows hosts.
- Verify that the Windows host firewalls are configured to allow access to port 5985.
- Review the information in System Settings for Authenticated Scans.


 Feedback
Feedback