Microsoft Azure resource logs (previously referred to as diagnostic logs) provide insight into operations performed within an Azure resource, such as Microsoft Azure Internet Information Services (IIS) or Microsoft Azure SQL Server. USM Anywhere discovers and collects these logs through the Azure APIs. A USM Anywhere Sensor deployed in your Azure environment is preconfigured to automatically discover logs from your Azure storage account. You can enable or disable the predefined jobs from the
To supplement the default log location or to add log collection for Microsoft Azure Web Apps, you can create custom log collection jobs that operate through the Azure Sensor app.
Note: What an Azure log job collects depends on whether you granted contributor permissions to one of your resources or to your entire Azure subscription for the USM Anywhere application. Depending on the Azure credentials configured for the deployed Azure Sensor, the sensor could have access to individual resource groups or the whole subscription. See Create an Application and Obtain Azure Credentials for more information.
Microsoft Azure Monitor (formerly Azure Insights) provides base-level infrastructure metrics and logs for most services in Azure. It helps you to track user activities within an Azure subscription, including when users log on, deploy or shut down virtual machines (VMs), and more. Through the Microsoft Azure Monitor Representational State Transfer (REST) API, USM Anywhere captures those logs and creates events.
You need to perform a specific configuration of Azure Monitor in the Azure console for USM Anywhere to collect the Azure-related logs. You need to enable the archive to a storage account option on the Azure subscription, which then enables USM Anywhere to automatically detect and create a job for the Azure-related jobs. When you complete the Log Collection step for your Azure Sensor setup, you can enable this default job, which runs every 20 minutes.
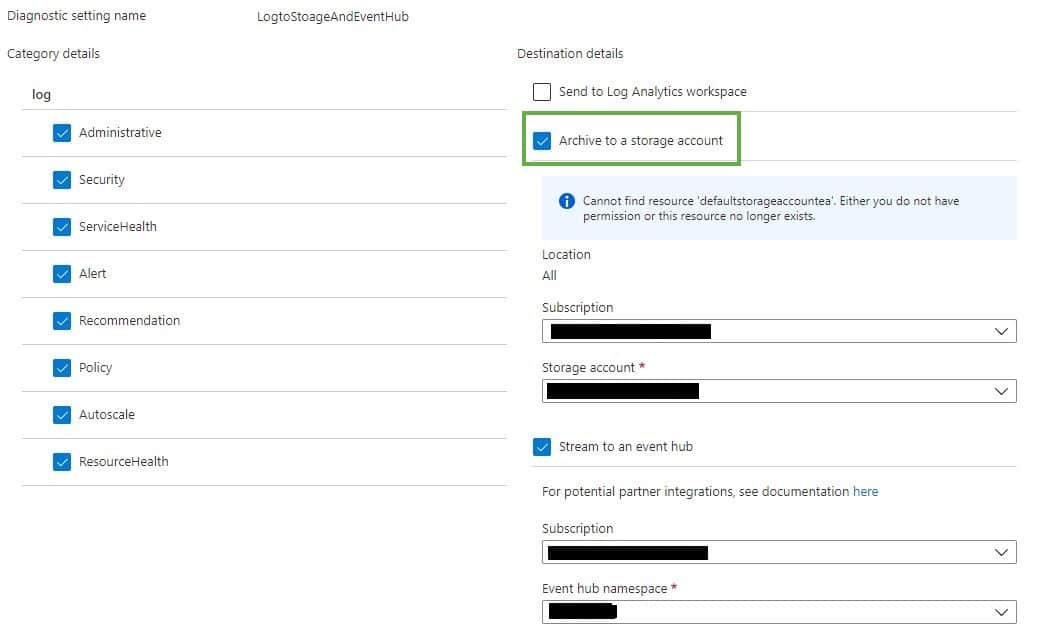
You can also enable or disable this default job in the USM Anywhere Scheduler page. When you select the job in this page, you can review the history for the scheduled job.

Microsoft Azure Security Center is an Azure service that continuously monitors your Azure environment and applies analytics to automatically detect a wide range of potentially malicious activity. It surfaces these detections as security alerts. Security Center performs this function by collecting data from your VMs, which is enabled for all VMs in your subscription by default. You can also customize this data collection in the Security Center policy.
You do not need to perform a specific configuration of the Azure Security Center alerts in the Azure console to be able to collect these logs. USM Anywhere automatically detects these logs and creates a job for Azure Security Center alerts logs. When you complete the Log Collection step for your Azure Sensor setup, you can enable this default job, which runs every 20 minutes.
You can also enable or disable this default job in in the USM Anywhere Scheduler page. When you select the job in this page, you can review the history for the scheduled job.

For individual VMs running IIS with Azure diagnostics enabled, you can designate storage for the IIS logs. USM Anywhere automatically detects these logs through the Azure APIs and Azure software development kits (SDKs). For each Azure Storage container locations with Azure IIS logs that it detects, USM Anywhere creates a default log collection job. When you complete the Log Collection step for your Azure Sensor setup, you can enable these default jobs, which run every five minutes.
Warning: If there are network restrictions in your environment restricting access to the storage account, those restrictions must allow access to the sensor.
Note: This type of IIS implementation is different than Azure Web Apps, which is a platform service and uses a different logging configuration. See Azure Web Apps Logs for information about collecting logs for web apps.
You can also enable or disable this default job in the Job Scheduler. When you select the job in this page, you can review the history for the scheduled job. You could choose to disable this default job based on the IIS log locations that USM Anywhere discovers, and create a custom Azure IIS log collection job for a location that you specify.

When you configure the new job, set the App Action option to Process Azure IIS Logs. You must also specify the Resource Group, Storage Account, and Blob Container for the custom log collection job. See Create a New Azure Log Collection Job for more information about scheduling an Azure log collection job.
For individual VMs running an Azure SQL Server with Azure diagnostics enabled, you can designate storage for the IIS logs. You must configure this to use Microsoft Azure Table storage. To simplify the tracking of related security issues, USM Anywhere treats the SQL service as an asset, and maps events and other security issues directly with the SQL service. When it detects Azure Table storage locations with Azure SQL Server logs, USM Anywhere creates a default log collection job for each. When you complete the Log Collection step for your Azure Sensor setup, you can enable these default jobs, which run every five minutes.
Important: The Azure SQL Server job is deprecated. Use the Event Hub Integration to collect Azure SQL Server logs. See Collect Logs from Azure Event Hubs for more information.
If you want to supplement this automatic Azure log collection in USM Anywhere, you can create an additional Azure SQL Server log collection job.

When you configure the new job, set the App Action option to Process Azure SQL Server Logs. You must also specify the Resource Group, Storage Account, and Table Container for the custom log collection job. See Create a New Azure Log Collection Job for more information about creating a new Azure log collection job.
Warning: If there are network restrictions in your environment restricting access to the storage account, those restrictions must allow access to the sensor.
Azure App Service Web Apps is a fully managed compute platform that is optimized for hosting websites and web applications. A web app represents the compute resources that Azure provides for hosting a website or web application. These compute resources may be on shared or dedicated VMs. For each deployed web application in your Azure environment, you can enable diagnostic logging to capture and store the web server and application information.
Important: When configuring Azure Web Apps logs, you must use the World Wide Web Consortium (W3C) format and select the following fields:
date, time, s-sitename, cs-method, cs-uri-stem, cs-uri-query, s-port, cs-username, c-ip, cs(User-Agent), cs(Cookie), cs(Referer), cs-host, sc-status, sc-substatus, sc-win32-status, sc-bytes, cs-bytes, time-taken
Unlike the other supported Azure logs, the USM Anywhere Sensor does not perform an automatic discovery job for Web Apps to look for the storage location. If you want USM Anywhere to collect the log data for your Web Apps, you must create a new log job and specify the storage location parameters.

When you configure the new job, set the App Action option to Process Azure Web Apps Logs. You must also specify the Resource Group, Storage Account, and Blob Container for the custom log collection job. See Create a New Azure Log Collection Job for more information about creating a new Azure log collection job.
Warning: If there are network restrictions in your environment restricting access to the storage account, those restrictions must allow access to the sensor.
For individual VMs running Microsoft Windows with Azure diagnostics enabled, Azure stores the Windows Events logs by default. USM Anywhere automatically detects these logs through Azure APIs and Azure SDKs. When it detects Azure Storage container locations with Azure Windows logs, USM Anywhere creates a default log collection job for each. When you complete the Log Collection step for your Azure Sensor setup, you can enable these default jobs, which run every five minutes.
If you want to supplement this automatic Azure log collection in USM Anywhere, you can create an additional Azure Windows log collection job.

When you configure the new job, set the App Action option to Process Azure Windows Logs. You must also specify the Resource Group, Storage Account, and Blob Container for the custom log collection job. See Create a New Azure Log Collection Job for more information about creating a new Azure log collection job.
 Related Video Content
Related Video Content Feedback
Feedback