| Applies to Product: |
|
|
Important: Note that the configurations outlined in this section are very important. This is the section that most of our partners have problems with. Not taking this section seriously can result in massive headaches and turn into a time-suck. Please proceed with care.
Setting Up VPN
A managed USM Appliance service requires full-time connectivity to your USM Appliance installation. LevelBlue includes virtual private network (VPN) tunneling software (OpenVPN) for creating point-to-point VPN links between components.
Follow the instructions on Configure a VPN Between USM Appliance Systems. Keep in mind that when using the VPN tunnel, you need to add the servers with the tunnel IP and not the original IP address of the components. In addition,
- In terms of routing and gateways, the only prerequisite is that the VPN client is able to access port 33800 of the external IP of the VPN server.
- Because a USM Appliance system cannot serve both as a VPN server and a VPN client at the same time, you cannot configure a USM Appliance Server as a VPN client (to the Federation Server) and a VPN server (to the USM Appliance Sensor) unless your Federation Server is hosted in AWS, see Federation Server in AWS Deployment Checklist.
- Because a USM Appliance Enterprise Server consists of two hardware pieces, an Enterprise Server and an Enterprise DB, you cannot configure a USM Appliance Enterprise Server as a VPN client.
- You must change the VPN server's IP to its public IP, see Additional Step When the VPN server and VPN client Reside in Different Networks.
-
Disable client-to-client VPN communication.
By default, client-to-client VPN communication is enabled. As an MSSP, you want to disable this so your clients cannot communicate with each other using the VPN setup.
 To disable client-to-client VPN communication
To disable client-to-client VPN communication
- SSH to the Federation Server.
-
On the LevelBlue Setup main menu, select Jailbreak System to gain command line access.
Select Yes when prompted. You will be in the root directory.
- Open the file /etc/openvpn/AVinfraestructure.conf.
- Locate the line "client-to-client" and comment it out by putting a "#" in front of it.
-
Restart the VPN service:
# service openvpn restart
Accessing Client USM Appliance from a Local Computer
After you have set up the VPN connection between the Federation Server and your client's USM Appliance, you can access the client USM Appliance over HTTPS or SSH from the Federation Server, using the VPN IP address. You can also access your client's USM Appliance though the VPN tunnel from any computer on your network, by leveraging the -L option in SSH and connecting to the Federation Server first.
To access client USM Appliance from your local computer
-
Run this command on your local computer:
$ ssh -L 40443: <Client_USM_Appliance_VPN_IP>:443 root@<Federation_Server_admin_ip>
- Then you can access client USM Appliance's web UI from your browser using this URL: https://127.0.0.1:40443.
Note: If using PuTTY on Windows, you can put the above commands into the SSH Tunnels section in the PuTTY Configuration Window.
Displaying Events from the Client USM Appliance Database
You can view events stored in your client's USM Appliance database directly in the Federation Server web UI by following the procedure below. a USM Appliance system cannot serve both as a VPN server and a VPN client at the same time, you cannot configure a USM Appliance Server as a VPN client (to the Federation Server) and a VPN server (to the USM Appliance Sensor)
Important: Step 1 below is only required if you are running USM Appliance versions prior to 5.6. If running version 5.6 or later, you can start with Step 2.
If you have updated to version 5.6 from a previous version and you have configured external databases before, you must modify the existing setup (Analysis > Security Event (SIEM) > External Databases, and click Modify) to enter new credentials.
To view events stored in your client USM Appliance's database from the Federation Server
-
(For version 5.5 and below) Authorize access from Federation Server to the client USM Appliance database.
-
From the Federation Server, SSH to the client USM Appliance.
The LevelBlue Setup menu displays.
-
On the LevelBlue Setup main menu, select Jailbreak System to gain command line access.
Select Yes when prompted. You will be in the root directory.
-
Add a firewall rule to allow Federation Server to connect to the client USM Appliance database, which is blocked by default.
Edit the file /etc/ossim/firewall_include and add the following line:
-I INPUT -s <Fed-Server-VPN-IP> -p tcp –m state --state NEW –-dport 3306 -j ACCEPT
Note: USM Appliance uses port 3306 for its database by default.
-
Grant database access to the Federation Server.
Connect to the database by typing the following:
ossim-db
Run the following commands:
GRANT ALL ON alienvault.* TO <user>@'<fed_server_vpn_ip>' IDENTIFIED BY '<user_pass>';
GRANT ALL ON alienvault_siem.* TO <user>@'<fed_server_vpn_ip>' IDENTIFIED BY '<user_pass>';
GRANT ALL ON datawarehouse.* TO <user>@'<fed_server_vpn_ip>' IDENTIFIED BY '<user_pass>';
FLUSH PRIVILEGES;
Where:
<user> refers to the user that you will enter in Step 2c below.
<fed_server_vpn_ip> refers to the VPN IP address of the Federation Server, which you will enter in Step 2c below.
<user_pass> refers to the password you will enter in Step 2c below.
Close the database connection:
quit;
-
Restart all services for changes to apply:
alienvault-reconfig -c -v -d
-
Check that the added rule is active:
iptables –nvL | grep 3306
-
-
Add the client USM Appliance database in the Federation Server web UI.
- Login to the Federation Server web UI.
- Go to Analysis > Security Event (SIEM) > External Databases, and click New.
-
Fill out the form and click Save.
An icon appears beneath the SIEM menu indicating the current database displayed.
-
Display events from the client USM Appliance database.
- From the Federation Server web UI, go to Analysis > Security Event (SIEM) > SIEM.
-
Click the Current database icon (
 ) to select the client USM Appliance database.
) to select the client USM Appliance database. 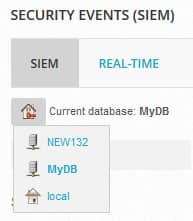
 Feedback
Feedback