 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
USM Anywhere delivers vulnerability assessment Vulnerability assessment uses active network vulnerability scanning and continuous vulnerability monitoring to provide one of the five essential capabilities. as part of a complete package of security monitoring Process of collecting all device status and event information and processing normalized events for evidence of vulnerabilities, possible attacks, and other malicious activity. and management capabilities for efficient threat detection. USM Anywhere does this to improve security in your network. To generate a vulnerability assessment, you first need to know what is vulnerable.
Vulnerability assessment is a functionality of USM Anywhere used for defining, identifying, classifying, and prioritizing the vulnerabilities in your system. The universal open and standardized method for rating IT vulnerabilities and determining the urgency of response is the Common Vulnerability Scoring System (CVSS). This method assigns severity scores to vulnerabilities. Scores range from 0 to 10, with 10 being the most severe.
USM Anywhere works on both CVSS Open framework for communicating the characteristics and severity of software vulnerabilities that helps to prioritize actions according to their threat. version 3 (CVSSv3) and the previous version 2 (CVSSv2) for scoring.
About Vulnerability Assessment in USM Anywhere
USM Anywhere detects vulnerabilities in assets An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. and controls these scanning functions:
- Running and scheduling vulnerability A known issue or weakness in a system, procedure, internal control, software package, or hardware that could be used to compromise security. scans (see Performing Vulnerability Scans for more information)
- Generating and examining reports (see Viewing Vulnerabilities Scan Results for more information)
- Generating system events when a vulnerability is detected (see Events Generated When a Vulnerability Is Detected)
USM Anywhere detects vulnerabilities using an authenticated scan Authenticated scans are performed from inside the machine using a user account with appropriate privileges. wherein the USM AnywhereSensor Sensors are deployed into an on-premises, cloud, or multi-cloud environment to collect logs and other security-related data. This data is normalized and then securely forwarded to USM Anywhere for analysis and correlation. initiates a credentialed connection to the asset (SSH Program to securely log into another computer over a network, execute commands in a remote machine, and move files from one machine to another through Secure Copy (SCP). in Linux systems or Microsoft Windows Remote Management (WinRM) in Windows systems), and remotely runs a series of commands for host-based assessment.
Vulnerability detection is based on an implementation of the Security Content Automation Protocol (SCAP) and the Open Vulnerability and Assessment Language (OVAL) 5.11.2 schema version. The National Vulnerability Database (NVD) is the U.S. government's content repository for SCAP. The OVAL schema is maintained by The MITRE Corporation and developed by the public OVAL community website at http://oval.mitre.org.
LevelBlue Labs™ Open Threat Exchange® (OTX™) queries NVD and MITRE every hour to search for the latest vulnerabilities. Every time you run a vulnerability scan, USM Anywhere queries OTX to update vulnerabilities information.
For Linux variants, USM Anywhere performs a series of generic UNIX and independent schema tests in addition to flavor-specific tests for IBM AIX, FreeBSD, Hewlett Packard Enterprise HP-UX, and Linux. For Windows, USM Anywhere performs a series of Windows schema and independent schema tests.
Warning: USM Anywhere removes vulnerabilities older than 90 days from the database.
About Vulnerability Severity
Discovering a vulnerability by itself is important but can be of little use without the ability to estimate the associated severity to an asset. For this reason, USM Anywhere assigns a severity to each vulnerability found in the system according to the severity score of the CVSS.
The following table shows the CVSS v2.0 and v3.0 ratings.
| Severity | v2 Score Range | v3 Score Range |
|---|---|---|
| None | N/A | 0.0 |
| Low |
0.0-3.9 |
0.1-3.9 |
| Medium | 4.0-6.9 | 4.0-6.9 |
| High | 7.0-10.0 | 7.0-8.9 |
| Critical | N/A | 9.0-10.0 |
Important: There is also an Under Analysis severity. This severity displays when the National Vulnerability Database (NVD) has not assigned a CVSS base score to the vulnerability. OTX queries NVD and MITRE every hour to search for the latest vulnerabilities. Every time you run a vulnerability scan, USM Anywhere queries OTX to update the vulnerabilities information. If the NVD has updated the CVSS base score for that vulnerability, USM Anywhere will update the status after you run a new vulnerability scan.
To see the CVSS score of a vulnerability
About Active and Inactive Vulnerabilities
In USM Anywhere you can find active vulnerabilities and inactive vulnerabilities. When you run a scan on an asset and USM Anywhere finds a vulnerability, this vulnerability is active for that specific asset. Only vulnerabilities found in the most recent scan on a particular asset are considered active, while any vulnerabilities present in previous scans but not found in the most recent scan will be considered inactive.
A Practical Example
USM Anywhere finds 15 vulnerabilities when you run a scan over an asset, and your product shows "active: 15, inactive: 0". After the scan, you remediate all of the vulnerabilities that were discovered. A week later, you run a scan over the same asset, and this new scan finds 3 vulnerabilities. Now, your product will show 3 vulnerabilities active out of 15 vulnerabilities found and will display "active: 3, inactive: 12".
Searching Active or Inactive Vulnerabilities
When you go to Environment > Vulnerabilities, USM Anywhere displays all active vulnerabilities by default.
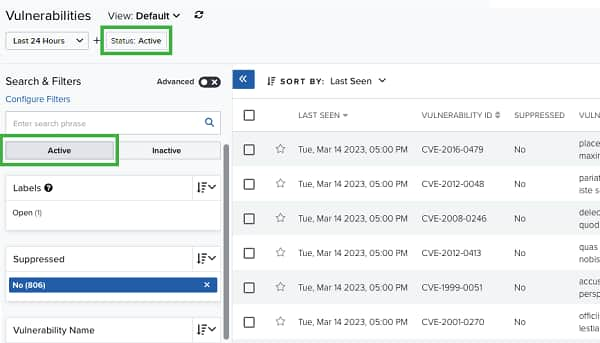
If you want to see the inactive vulnerabilities, select the Inactive filter. USM Anywhere displays the list of your inactive vulnerabilities.
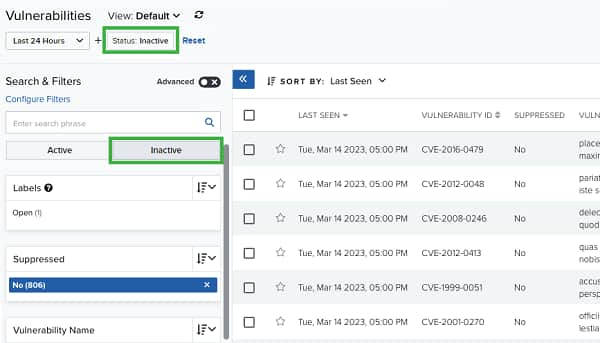
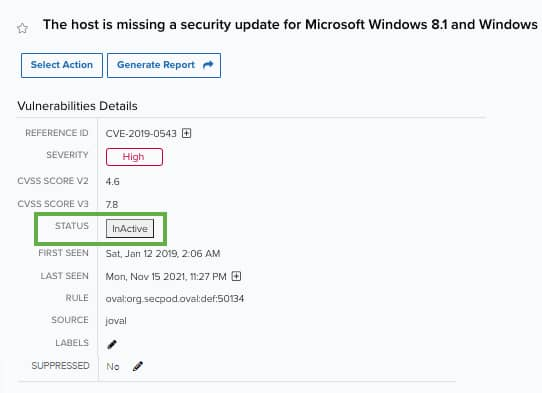
You can also see whether a vulnerability is active or inactive by opening the full details screen of the vulnerability.
Events Generated When a Vulnerability Is Detected
You can configure your USM Anywhere to generate an event whenever a vulnerability is detected.
Note: Enabling this feature will generate system events for each newly discovered
To enable event creation upon vulnerability detection
- Go to Settings > System and then select Vulnerability Settings.
-
Toggle Generate a System Event on Vulnerability Discovery to enable this setting.
Toggle this off to disable event creation.
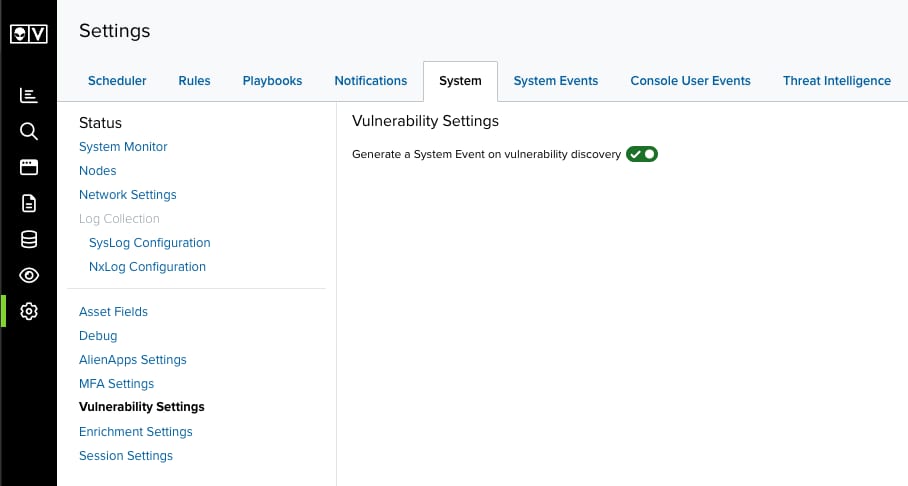
Important: This setting is only accessible to users in a Manager role.

 Feedback
Feedback