 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
USM Anywhere provides a centralized view of regular events and system events Any traffic or data exchange detected by LevelBlue products through a sensor or external devices such as a firewall..
From now on, and during a grace period, the following regular events are also generated as system events:
- Sensor appears offline (see Sensor Disconnected from the USM Anywhere Service for more information)
- Sensor reconnected (see Sensor Disconnected from the USM Anywhere Service for more information)
- Event from asset not received (see Events Created When an Asset Stops Sending Data for more information)
- Event from BlueApp not received (see Events Created When BlueApps Stop Receiving Data for more information)
Warning: Soon the previously listed regular events will be generated only as system events. LevelBlue will announce this change in advance. Meanwhile, LevelBlue recommends that you disable all orchestration rules in your environment regarding these kinds of regular events and create new orchestration rules based on these system events. See Orchestration Rule for the "Sensor Appears Offline" System Event, Orchestration Rule for the "Sensor Reconnected" System Event,Orchestration Rule for the "Event from Asset Not Received" System Event, and Orchestration Rule for the "Event from BlueApp Not Received" System Event for more information.
Disable Orchestration Rules
LevelBlue recommends that you disable all orchestration rules you have created in your environment regarding these events:
- Sensor appears offline
- Sensor reconnected
- Event from asset not received
- Event from BlueApp not received
To disable an orchestration rule
- Go to Settings > Rules.
- In the enabled column, click the
icon of the rule you want to disable.
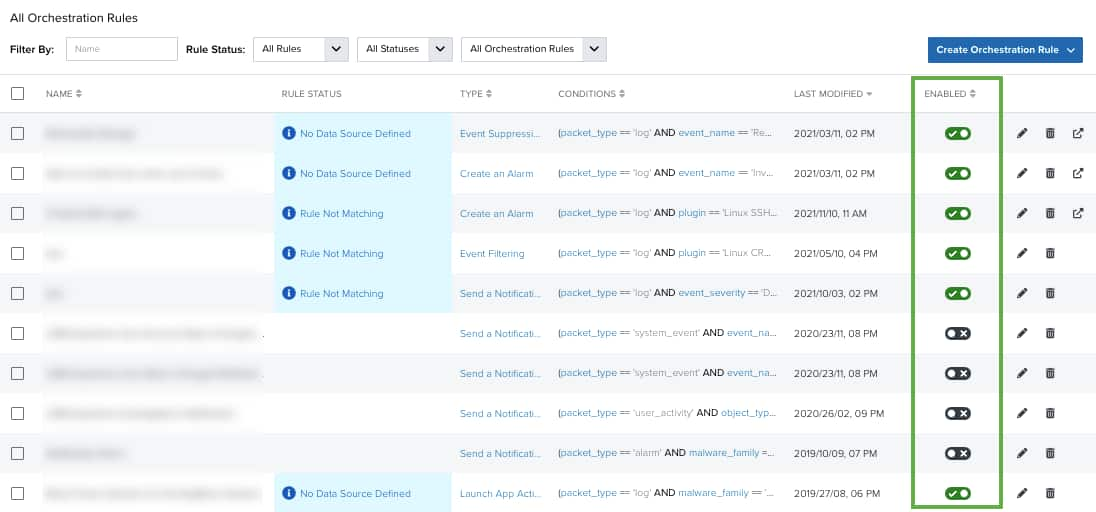
This turns the icon gray and disables the orchestration rule.
 Feedback
Feedback