 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
Correlation Correlation identifies potential security threats by identifying relationships between multiple types of events occurring in two or more assets. is the processing of the event Any traffic or data exchange detected by LevelBlue products through a sensor or external devices such as a firewall. stream to identify important events or patterns of events within large volumes of data. The logic to identify these events is encapsulated in a correlation rule A correlation rule correlates incoming events based on previously defined relationships defined in the correlation directive, associating multiple events, of the same or different event types, from the same data source.. The LevelBlue Labs™ Security Research Team creates correlation rules, which associate multiple events from one or more data sources to identify potential security threats. These rules identify patterns associated with malicious activity Activity in a system that exceeds or misuses that access in a manner that negatively affects the confidentiality, integrity, or availability of the organization's information systems.. Alarms Alarms provide notification of an event or sequence of events that require attention or investigation. are generated by an explicit call within these rules.
These correlation rules are created by the Security Research Team and you are not able to modify them. However, you can use orchestration rules to modify the way USM Anywhere treats events. See Orchestration Rules for more information.
Important: The "Suspicious Behavior - OTX Indicators of Compromise" correlation rule generates alarms if the pulse comes from the LevelBlue OTX account.
What Is Correlation?
Correlation is a process performed by the correlation engine in USM Anywhere. It identifies potential security threats by detecting behavior patterns across different types of assets An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers., which produce disparate yet related events. Correlation links different events, turning data into more useful information.
The logs received and processed by USM Anywhere carry important information such as what your users are doing, what data is being accessed, how your system and network are performing, and if there are any security threats or attacks taking place. However, reading logs has these disadvantages:
- Logs vary from system to system or even from version to version on the same system.
- Logs have limited perspective because each system sees events from its own perspective.
- Logs are static, fixed points in time without the full context or sequence of related events.
The correlation process provides answers to these challenges, putting the events into full context. For example, a network firewall Virtual or physical device designed to defend against unauthorized access to data, resources, or a private network. A firewall’s primary purpose is to create segregation between two or more network resources, blocking undesirable traffic between them. sees packets and network sessions, while an application A software program that performs some collection of tasks on a computer or some other programmable device. sees users, data, and requests. While different systems report logs of similar activities, the way in which they articulate these activities is quite different. With the help of correlation rules, USM Anywhere can correlate the two types of events, generating an alarm if a threat exists.
Event correlation enables the security analysts and the incident responders to do the following:
- Make informed decisions on how to respond to security threats
- Validate the effectiveness of existing security controls
- Measure and report compliance
- Detect policy violations
Correlation Rules Structure
This is the structure of correlation rules: Intent — Strategy — Method.
The structure uses a three-tiered model for describing an observed behavior:
-
Intent: The first tier is the "intent" of the behavior. This roughly maps to the "intrusion kill chain" to provide an understanding of the context of the behavior.
-
Strategy: The second tier is the strategy the attacker One who maliciously attempts to bypass security restrictions or negatively impact a system or resource. took, used to describe the methodology employed.
-
Method: The third tier is the "method" of the behavior, used to describe the details of the particular methodology.
The intent describes the context of the behavior that is being observed. These intents roughly map to the stages of the intrusion kill chains but are collapsed to ensure that each is discrete.
From highest to lowest, these are the threat categories:
| Intent | Description |
|---|---|
| System Compromise State or indication that an intruder has bypassed security measures and gained unauthorized access to resources, installed malicious software, or modified existing software or configurations in an attempt to cause damage or steal information. | Behavior indicating a compromised system. |
| Exploitation & Installation | Behavior indicating a successful exploit Piece of software, data, or a sequence of commands that takes advantage of a flaw or vulnerability to cause unintended or unanticipated behavior to occur in software or hardware, that result in gaining increased privileges and access privileged data. of a vulnerability A known issue or weakness in a system, procedure, internal control, software package, or hardware that could be used to compromise security., backdoor, or remote access trojan being installed on the system. |
| Delivery & Attack | Behavior indicating an attempted delivery of an exploit. This can include detection of malicious email attachments, network-based detection of known attack payloads, or analysis-based detection of known attack strategies such as an SQL injection. |
| Reconnaissance & Probing |
Behavior indicating an actor attempting to discover information about your organization. This is broad-based, including everything from port scans Process in which a series of messages are sent to a computer to probe for open ports. to social engineering Using people's inherent goodwill against them in order to violate security. to open-source intelligence. |
| Environmental Awareness | Behavior and status about the environment being monitored. This includes information about services running, behavior of users in the environment, and the configuration of the systems. |
The strategy describes the broad-based strategy or behavior that is detected. It is a description of the strategy the malicious user is using to achieve their goal. For example, when trying to exploit a known vulnerability in a web browser, the attacker is launching a "Client-Side Attack - Known Vulnerability".
The method describes the approach that the actor employs. To further the previous example, the method would provide additional detail on the target of the attack and the vulnerability "Firefox - CVE-2008-4064".
USM Anywhere Correlation Rules
USM Anywhere provides built-in rules and adds more every week through the LevelBlue Labs™ Threat Intelligence Subscription The LevelBlue Labs™ Threat Intelligence Subscription provides subscribers with the ability to detect the latest threats with continually updated correlation rules, IDS signatures, vulnerability audits, asset discovery signatures, IP reputation data, collection and integrations, and report templates.. Some of these rules are generic, which means that the rule can match data from different data sources. For example, the following rule matches data from different application firewalls:
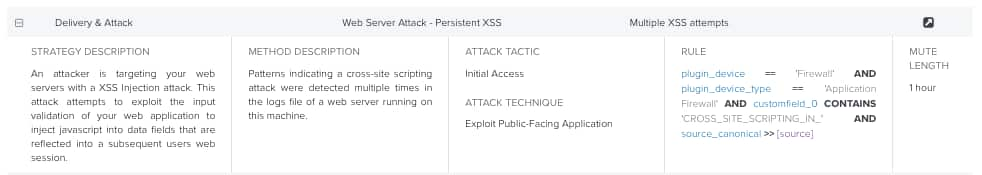
Some rules are more specific, which means that the rule only matches a particular data source. For example, the following rule only matches data from Watchguard XTM:
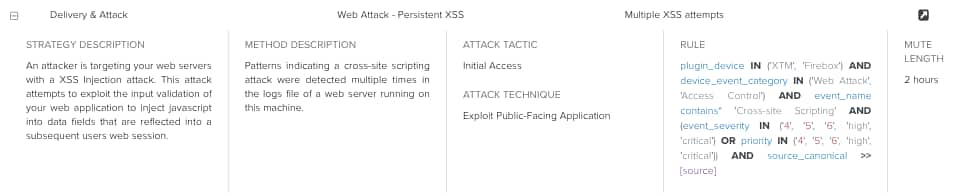
Note: When a more specific rule exists in USM Anywhere, it takes precedence over the generic rule.
To see correlation rules
- Go to Settings > Rules > Correlation Rules.
- You can use the search field above the table to search for a rule by entering the search text in the field and then clicking the
icon.
-
Click the rule to expand the details of the rule.
You can see the strategy, the method, and the rule itself.
Important: Correlation rule details are not visible to users with a trial license.
-
Click the
icon to open the Alarms List view page.
The page includes Rules Name as a filter so that you can see how many alarms match the selected rule.
Note: The mute length indicates during how long that rule is not going to generate an alarm.
 Feedback
Feedback