Amazon Web Services (AWS) CloudTrail produces log data for numerous AWS cloud services. Depending on the size and activity in your AWS account, the AWS CloudTrail log collection in USM Anywhere can produce an excessive number of events. Some of these events reflect normal activity and you will most likely want to create suppression rules to eliminate these events in the future. For other event types that are important and require attention, you may want to generate alarms Alarms provide notification of an event or sequence of events that require attention or investigation. or send notifications Communication of an important event, typically through an email message or other desktop display. In USM Appliance, notifications are typically triggered by events, policies, and correlation directives, and in USM Anywhere, they are typically triggered by notification rules or directly from alarms..
USM Anywhere uses the logged action to populate the name for the event during the normalization process. You can use the Event Name field to specify a match condition for the events you want to manage using a rule.
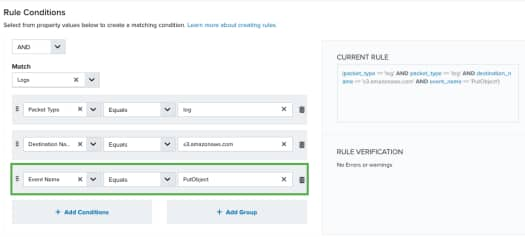
Important: The order of the conditions is significant because USM Anywhere follows a specific order when it evaluates the rule conditions, reading them from left to right. If your rule includes the packet_type and plugin_device fields, these should always occur first in the order.
For more information about creating rules, see Orchestration Rules.
CloudTrail Event Names by Type
The AWS SDK for Java provides a Java API for AWS infrastructure services, including Amazon S3, Route 53, Redshift, and RDS. This allows developers to programmatically manage these resources from an application.
The CloudTrail data source provides normalization for AWS access control policy actions supported by the AWS SDK for Java API, such as:
amazonaws/auth/policy/actions/S3Actions.html
amazonaws/auth/policy/actions/Route53Actions.html
amazonaws/auth/policy/actions/RedshiftActions.html
amazonaws/auth/policy/actions/RDSActions.html
For each logged action, the data source parses the event and retains the raw <enum> value as the event name. If you want to create and alarm or notification rule that triggers for an S3 policy action event, the matching condition expression would contain
event_name == '<enum>'
where <enum> is the enumerated value for the action.
Amazon Elastic Compute Cloud (Amazon EC2) is a core web service available for an AWS account that provides secure, resizable compute capacity in the cloud. It is designed to make web-scale cloud computing easier for developers.
The CloudTrail data source provides normalization for the event types supported by the Amazon EC2 API (https://docs.aws.amazon.com/AWSEC2/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add inbound network traffic rule to security group | Adds one or more ingress rules to a security group. | AuthorizeSecurityGroupIngress |
| Add new subnet into route table | Associates a subnet with a route table. | AssociateRouteTable |
| Add outbound network traffic rule to security group | Adds one or more egress rules to a security group for use with a VPC. | AuthorizeSecurityGroupEgress |
| Assign elastic IP address | Associates an Elastic IP address with an instance or a network interface. | AssociateAddress |
| Assign private IP | Assigns one or more secondary private IP addresses to the specified network interface. | AssignPrivateIpAddresses |
| Associate VPC with public gateway | Attaches an Internet gateway to a VPC, enabling connectivity between the Internet and the VPC. | AttachInternetGateway |
| Attach EBS volume | Attaches an EBS volume to a running or stopped instance and exposes it to the instance with the specified device name. | AttachVolume |
| Attach network interface | Attaches a network interface to an instance. | AttachNetworkInterface |
| Backup EBS volume | Copies a point-in-time snapshot of an EBS volume and stores it in Amazon S3. | CreateSnapshot |
| Backup instance |
Bundles an Amazon instance store-backed Windows instance. During bundling, only the root device volume (C:\) is bundled. Data on other instance store volumes is not preserved. |
BundleInstance |
| Backup instance to S3 | Exports a running or stopped instance to an S3 bucket. | CreateInstanceExportTask |
| Cancel instance backup | Cancels a bundling operation for an instance store-backed Windows instance. | CancelBundleTask |
| Cancel instance export |
Cancels an active export task. This operation removes all artifacts of the export, including any partially-created Amazon S3 objects. |
CancelExportTask |
| Cancel reserve instance listing | Cancels the specified Reserved Instance listing in the Reserved Instance Marketplace. | CancelReservedInstancesListing |
| Cancel spot instance request | Cancels one or more Spot Instance requests. | CancelSpotInstanceRequests |
| Canceled import of a machine image or volume |
Cancels an active conversion task (import of a machine image or volume). This operation removes all artifacts of the conversion, including a partially uploaded volume or instance. |
CancelConversionTask |
| Clone AMI | Creates an Amazon EBS-backed AMI from an Amazon EBS-backed instance that is either running or stopped. | CreateImage |
| Confirm you are a customer of a marketplace product | Determines whether a product code is associated with an instance. | ConfirmProductInstance |
| Connect virtual private gateway to a VPC | Attaches a virtual private gateway to a VPC. | AttachVpnGateway |
| Copy AMI between regions | Initiates the copy of an AMI from the specified source region to the current region. | CopyImage |
| Copy EBS backup to S3 | Copies a point-in-time snapshot of an EBS volume and stores it in Amazon S3. | CopySnapshot |
| Create a ACL entry | Creates an entry (a rule) in a network ACL with the specified rule number. | CreateNetworkAclEntry |
| Create a network interface | Creates a network interface in the specified subnet. | CreateNetworkInterface |
| Create a subnet in VPC | Creates a subnet in an existing VPC. | CreateSubnet |
| Create ACL for a VPC | Creates a network ACL in a VPC. | CreateNetworkAcl |
| Create connection between VPW and VPN gateway | Creates a VPN connection between an existing virtual private gateway and a VPN customer gateway. | CreateVpnConnection |
| Create datafeed for spot instance | Creates a data feed for Spot Instances, enabling you to view Spot Instance usage logs. | CreateSpotDatafeedSubscription |
| Create DHCP options | Creates a set of DHCP options for a VPC. | CreateDhcpOptions |
| Create EBS volume | Creates an EBS volume that can be attached to an instance in the same Availability Zone. | CreateVolume |
| Create key pair | Creates a 2048-bit RSA key pair with the specified name. | CreateKeyPair |
| Create new VPC | Creates a VPC with the specified IPv4 CIDR block. | CreateVpc |
| Create or update tag | Adds or overwrites one or more tags for the specified Amazon EC2 resource or resources. | CreateTags |
| Create placement group | Creates a placement group for launching instances. | CreatePlacementGroup |
| Create public gateway for VPC | Creates an Internet gateway for use with a VPC. | CreateInternetGateway |
| Create reserved instance listing | Creates a listing for Amazon EC2 Standard Reserved Instances to be sold in the Reserved Instance Marketplace. | CreateReservedInstancesListing |
| Create route in VPC | Creates a route in a route table within a VPC. | CreateRoute |
| Create security group | Creates a security group. | CreateSecurityGroup |
| Create static route for VPC | Creates a route table for the specified VPC. | CreateRouteTable |
| Create static route for VPN | Creates a static route associated with a VPN connection between an existing virtual private gateway and a VPN customer gateway. | CreateVpnConnectionRoute |
| Create VPN gateway | Provides information to AWS about a VPN customer gateway device. | CreateCustomerGateway |
| Create VPN gateway | Creates a virtual private gateway. | CreateVpnGateway |
| Delete a VPC peering connection | Deletes a VPC peering connection. | DeleteVpcPeeringConnection |
| Delete ACL | Deletes the specified network ACL. | DeleteNetworkAcl |
| Delete ACL entry | Deletes the specified ingress or egress entry (rule) from the specified network ACL. | DeleteNetworkAclEntry |
| Delete customer gateway | Deletes the specified customer gateway. | DeleteCustomerGateway |
| Delete DHCP options | Deletes the specified set of DHCP options. | DeleteDhcpOptions |
| Delete Flow Logs | Deletes one or more flow logs. | DeleteFlowLogs |
| Delete inbound network traffic restriction from security group | Removes one or more ingress rules from a security group. | RevokeSecurityGroupIngress |
| Delete network interface | Deletes the specified network interface, which must be in a detached state. | DeleteNetworkInterface |
| Delete network route | Deletes the specified route from the specified route table. | DeleteRoute |
| Delete outbound network traffic rule from security group |
Removes one or more egress rules from a security group for EC2-VPC. This operation does not apply to security groups for use in EC2-Classic. |
RevokeSecurityGroupEgress |
| Delete placement group | Deletes the specified placement group. | DeletePlacementGroup |
| Delete public (internet) gateway | Deletes the specified Internet gateway, which must be detached from the VPC. | DeleteInternetGateway |
| Delete public key | Deletes the specified key pair by removing the public key from Amazon EC2. | DeleteKeyPair |
| Delete route table | Deletes the specified route table, which must be disassociated from any subnets. | DeleteRouteTable |
| Delete security group | Deletes a security group, which cannot be associated with an instance or referenced by another security group. | DeleteSecurityGroup |
| Delete snapshot | Deletes the specified snapshot. | DeleteSnapshot |
| Delete spot instance datafeed | Deletes the data feed for Spot Instances. | DeleteSpotDatafeedSubscription |
| Delete subnet | Deletes the specified subnet, which must have all running instances terminated. | DeleteSubnet |
| Delete tag from resource | Deletes the specified set of tags from the specified set of resources. | DeleteTags |
| Delete virtual private gateway | Deletes the specified virtual private gateway. | DeleteVpnGateway |
| Delete volume | Deletes the specified EBS volume, which must be in the available state (not attached to an instance). | DeleteVolume |
| Delete VPC | Deletes the specified VPC, which must have all gateways and resources detached or deleted. | DeleteVpc |
| Delete VPN connection | Deletes the specified VPN connection. | DeleteVpnConnection |
| Delete VPN to gateway network route | Deletes the specified static route associated with a VPN connection between an existing virtual private gateway and a VPN customer gateway. | DeleteVpnConnectionRoute |
| Detach EBS volume from instance | Detaches an EBS volume from an instance. | DetachVolume |
| Detach public gateway from VPC | Detaches an Internet gateway from a VPC, disabling connectivity between the Internet and the VPC. | DetachInternetGateway |
| Detach virtual private gateway from VPC | Detaches a virtual private gateway from a VPC. | DetachVpnGateway |
| Disable AMI |
Deregisters the specified AMI so that it cannot be used to launch new instances. This does not affect any existing instances launched from the AMI. |
DeregisterImage |
| Disable monitoring for instance | Disables detailed monitoring for a running instance. | UnmonitorInstances |
| Disallow VPC from accepting routes from gateway | Disables a virtual private gateway (VGW) from propagating routes to a specified route table of a VPC. | DisableVgwRoutePropagation |
| Disassociate elastic IP address | Disassociates an Elastic IP address from the instance or network interface. | DisassociateAddress |
| Disassociate private IP address | Unassigns one or more secondary private IP addresses from a network interface. | UnassignPrivateIpAddresses |
| Enable volume i/o | Enables I/O operations for a volume that had I/O operations disabled because the data on the volume was potentially inconsistent. | EnableVolumeIO |
| Enabled VPC to accept routes from gateway | Enables a virtual private gateway (VGW) to propagate routes to the specified route table of a VPC. | EnableVgwRoutePropagation |
| Get console output for instance | Returns the console output for the specified instance. | GetConsoleOutput |
| Get elastic IP address | Allocates an Elastic IP address. | AllocateAddress |
| Get windows password | Returns the encrypted administrator password for a running Windows instance. | GetPasswordData |
| Import instance | Creates an import instance task using metadata from the specified disk image. | ImportInstance |
| Import public key | Imports the public key from an RSA key pair created with a third-party tool. | ImportKeyPair |
| Import volume to amazon | Creates an import volume task using metadata from the specified disk image. | ImportVolume |
| Initialize DHCP options with VPC | Associates a set of DHCP options with the specified VPC, or associates no DHCP options with the VPC. | AssociateDhcpOptions |
| Pause instance |
Stops an Amazon EBS-backed instance. The root partition Amazon EBS volume remains and continues to persist the data, and continues to incur charges for Amazon EBS volume usage. |
StopInstances |
| Provide feedback to amazon | Submits feedback about the status of a running instance to Amazon. | ReportInstanceStatus |
| Purchase reserve instance | Purchases a Reserved Instance for use with the account. | PurchaseReservedInstancesOffering |
| Re-Start instance | Starts an Amazon EBS-backed instance that is in a stopped state. | StartInstances |
| Reboot instance | Requests a reboot of one or more instances. | RebootInstances |
| Register AMI with amazon | Registers an AMI, which is the final step before users can launch an instance from the AMI. | RegisterImage |
| Reject VPC peering connection request | Rejects a VPC peering connection request. | RejectVpcPeeringConnection |
| Release elastic IP | Releases the specified Elastic IP address. | ReleaseAddress |
| Remove network interface from instance | Detaches a network interface from an instance. | DetachNetworkInterface |
| Remove subnet from route table | Disassociates a subnet from a route table. | DisassociateRouteTable |
| Request spot instance | Creates a Spot Instance request. | RequestSpotInstances |
| Request VPC peer connection | Requests a VPC peering connection between two VPCs. | CreateVpcPeeringConnection |
| Reset AMI setting | Resets an attribute of an AMI to its default value. | ResetImageAttribute |
| Reset instance setting | Resets an attribute of an instance to its default value. | ResetInstanceAttribute |
| Reset network interface setting | Resets a network interface attribute. | ResetNetworkInterfaceAttribute |
| Reset snapshot setting | Resets permission settings for the specified snapshot. | ResetSnapshotAttribute |
| Shut down instance | Shuts down one or more instances. | TerminateInstances |
| Start instance monitoring | Enables detailed monitoring for a running instance. | MonitorInstances |
| Start instances | Launches the specified number of instances using an AMI. | RunInstances |
| Update ACL | Replaces an entry (rule) in a network ACL. | ReplaceNetworkAclEntry |
| Update AMI details | Modifies the specified attribute of the specified AMI. | ModifyImageAttribute |
| Update instance details | Modifies the specified attribute of the specified instance. | ModifyInstanceAttribute |
| Update network interface settings | Modifies the specified network interface attribute. | ModifyNetworkInterfaceAttribute |
| Update reserved instance count in availability zone | Modifies the Availability Zone, instance count, instance type, or network platform (EC2-Classic or EC2-VPC) of Reserved Instances. | ModifyReservedInstances |
| Update route in route table | Replaces an existing route within a route table in a VPC. | ReplaceRoute |
| Update route table for VPC | Changes the route table associated with a given subnet in a VPC. | ReplaceRouteTableAssociation |
| Update snapshot permission settings | Adds or removes permission settings for the specified snapshot. | ModifySnapshotAttribute |
| Update subnet setting | Modifies a subnet attribute. | ModifySubnetAttribute |
| Update subnet/ACL association | Changes the network ACL association for a subnet. | ReplaceNetworkAclAssociation |
| Update volume property | Modifies a volume attribute. | ModifyVolumeAttribute |
| Update VPC attribute | Modifies the specified attribute of the specified VPC. | ModifyVpcAttribute |
| View account details | Returns attributes of the AWS account. | DescribeAccountAttributes |
| View ACL for network | Returns one or more network ACLs. | DescribeNetworkAcls |
| View AMI details | Returns the specified attribute of the specified AMI. | DescribeImageAttribute |
| View availability zones | Returns one or more of the Availability Zones that are available to the user. | DescribeAvailabilityZones |
| View available AWS regions | Returns one or more regions that are currently available to the user. | DescribeRegions |
| View details of conversion tasks | Returns one or more of the user's conversion tasks. | DescribeConversionTasks |
| View DHCP options | Returns one or more of the user's DHCP options sets. | DescribeDhcpOptions |
| View EBS volumes | Returns the specified EBS volumes. | DescribeVolumes |
| View Elastic IP addresses | Returns one or more of the user's Elastic IP addresses. | DescribeAddresses |
| View export tasks | Returns one or more of the user's export tasks. | DescribeExportTasks |
| View image details | Returns one or more of the images (AMIs, AKIs, and ARIs) available to the user. | DescribeImages |
| View Instance details | Returns the specified attribute of the specified instance. | DescribeInstanceAttribute |
| View Instance details | Returns one or more of the user's instances. | DescribeInstances |
| View instance status | Returns the status of one or more instances. | DescribeInstanceStatus |
| View key pair | Returns one or more of the user's key pairs. | DescribeKeyPairs |
| View network interface settings | Returns a network interface attribute. | DescribeNetworkInterfaceAttribute |
| View network interfaces | Returns one or more of the user's network interfaces. | DescribeNetworkInterfaces |
| View network routes | Returns one or more of the user's route tables. | DescribeRouteTables |
| View placement group details | Returns one or more of the user's placement groups. | DescribePlacementGroups |
| View public gateway details | Returns one or more of the user's Internet gateways. | DescribeInternetGateways |
| View purchased reserved instances | Returns one or more of the purchased Reserved Instances. | DescribeReservedInstances |
| View reserve instance offerings | Returns Reserved Instance offerings that are available for purchase. | DescribeReservedInstancesOfferings |
| View reserved instance listings | Returns your account's Reserved Instance listings in the Reserved Instance Marketplace. | DescribeReservedInstancesListings |
| View Reserved Instance modification | Returns the modifications made to your Reserved Instances. | DescribeReservedInstancesModifications |
| View security group details | Returns one or more of the user's security groups. | DescribeSecurityGroups |
| View snapshot details | Returns one or more of the EBS snapshots available to the user. | DescribeSnapshots |
| View snapshot setting | Returns the specified attribute of the specified snapshot. | DescribeSnapshotAttribute |
| View spot instance datafeed details | Returns the data feed for Spot Instances. | DescribeSpotDatafeedSubscription |
| View spot instance requests | Returns the specified Spot Instance requests. | DescribeSpotInstanceRequests |
| View spot price history | Returns the Spot price history. | DescribeSpotPriceHistory |
| View subnet | Returns one or more o.f the user's subnets | DescribeSubnets |
| View tags | Returns one or more of the tags for the user's EC2 resources. | DescribeTags |
| View virtual private gateway | Returns one or more of the user's virtual private gateways. | DescribeVpnGateways |
| View volume settings | Returns the specified attribute of the specified volume. | DescribeVolumeAttribute |
| View volume status | Returns the status of the specified volumes. | DescribeVolumeStatus |
| View VPC details | Returns the specified attribute of the specified VPC. | DescribeVpcAttribute |
| View VPC details | Returns one or more of your VPCs. | DescribeVpcs |
| View VPC peering connections | Returns one or more of your VPC peering connections. | DescribeVpcPeeringConnections |
| View VPN connections | Returns one or more of the user's VPN connections. | DescribeVpnConnections |
| View VPN gateway information | Returns one or more of the user's VPN customer gateways. | DescribeCustomerGateways |
| View windows backup tasks | Returns one or more of the user's bundling tasks. | DescribeBundleTasks |
| VPC Peering connection established | Accepts a VPC peering connection request. | AcceptVpcPeeringConnection |
Amazon EC2 Auto Scaling is an automated scaling service available for EC2 assets within an AWS account. This service automatically launches or terminates EC2 instances based on user-defined policies, schedules, and health checks.
The CloudTrail data source provides normalization for the event types supported by the Amazon EC2 Auto Scaling API (https://docs.aws.amazon.com/autoscaling/ec2/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Attach Instances | Attaches one or more EC2 instances to a specified Auto Scaling group. | AttachInstances |
| Complete Lifecycle Action | Completes the lifecycle action for a specified token or instance with the specified result. | CompleteLifecycleAction |
| Create Auto Scaling Group | Creates an Auto Scaling group with the specified name and attributes. | CreateAutoScalingGroup |
| Create Launch Configuration | Creates a launch configuration used to launch new EC2 instances. | CreateLaunchConfiguration |
| Create Or Update Tags | Creates or updates tags for a specified Auto Scaling group. | CreateOrUpdateTags |
| Delete Auto Scaling Group |
Deletes a specified Auto Scaling group. If the group has policies, deleting the group deletes the policies, the underlying alarm actions, and any alarm that no longer has an associated action. |
DeleteAutoScalingGroup |
| Delete Launch Configuration | Deletes a specified launch configuration that is not attached to an Auto Scaling group. | DeleteLaunchConfiguration |
| Delete Lifecycle Hook | Deletes a specified lifecycle hook. | DeleteLifecycleHook |
| Delete Notification Configuration | Deletes a specified notification configuration. | DeleteNotificationConfiguration |
| Delete Policy |
Deletes a specified Auto Scaling policy. Deleting a policy deletes the underlying alarm action, but does not delete the alarm, even if it no longer has an associated action. |
DeletePolicy |
| Delete Scheduled Action | Deletes the specified scheduled action. | DeleteScheduledAction |
| Describe Account Limits | Retrieves information about the current Auto Scaling resource limits for the AWS account. | DescribeAccountLimits |
| Describe Adjustment Types | Retrieves information about the policy adjustment types for use with PutScalingPolicy. | DescribeAdjustmentTypes |
| Describe Auto Scaling Groups | Retrieves information about one or more Auto Scaling groups. | DescribeAutoScalingGroups |
| Describe Auto Scaling Instances | Retrieves information about one or more Auto Scaling instances. | DescribeAutoScalingInstances |
| Describe Auto Scaling Notification Types | Retrieves information about the notification types that are supported by Auto Scaling. | DescribeAutoScalingNotificationTypes |
| Describe Launch Configurations | Retrieves information about one or more launch configurations. | DescribeLaunchConfigurations |
| Describe Lifecycle Hooks | Retrieves information about the lifecycle hooks for a specified Auto Scaling group. | DescribeLifecycleHooks |
| Describe Lifecycle Hook Types | Retrieves information about the available types of lifecycle hooks. | DescribeLifecycleHookTypes |
| Describe Metric Collection Types | Retrieves information about the available CloudWatch metrics for Auto Scaling. | DescribeMetricCollectionTypes |
| Describe Notification Configurations | Retrieves information about the notification actions associated with the specified Auto Scaling group. | DescribeNotificationConfigurations |
| Describe Policies | Retrieves information about the policies for the specified Auto Scaling group. | DescribePolicies |
| Describe Scaling Activities | Retrieves information about one or more scaling activities for the specified Auto Scaling group. | DescribeScalingActivities |
| Describe Scaling Process Types | Retrieves information about the scaling process types for use with ResumeProcesses and SuspendProcesses. | DescribeScalingProcessTypes |
| Describe Scheduled Actions | Retrieves information about the actions scheduled for a specified Auto Scaling group that haven't run. | DescribeScheduledActions |
| Describe Termination Policy Types | Retrieves information about the termination policies supported by Auto Scaling. | DescribeTerminationPolicyTypes |
| Detach Instances | Removes one or more instances from a specified Auto Scaling group. | DetachInstances |
| Disable Metrics Collection | Disables group metrics for a specified Auto Scaling group. | DisableMetricsCollection |
| Enable Metrics Collection | Enables group metrics for a specified Auto Scaling group. | EnableMetricsCollection |
| Enter Standby | Moves the specified instances into the standby state. | EnterStandby |
| Execute Policy | Executes a specified policy. | ExecutePolicy |
| Exit Standby | Moves the specified instances out of the standby state. | ExitStandby |
| Put Lifecycle Hook |
Creates or updates a lifecycle hook for a specified Auto Scaling Group. A lifecycle hook tells Auto Scaling to perform an action on an instance that is not actively in service, such as when the instance launches or before the instance terminates. |
PutLifecycleHook |
| Put Notification Configuration | Configures an Auto Scaling group to send notifications when specified events take place. | PutNotificationConfiguration |
| Put Scaling Policy | Creates or updates a policy for an Auto Scaling group. | PutScalingPolicy |
| Put Scheduled Update Group Action | Creates or updates a scheduled scaling action for an Auto Scaling group. | PutScheduledUpdateGroupAction |
| Record Lifecycle Action Heartbeat |
Records a heartbeat for the lifecycle action associated with a specified token or instance. This extends the timeout by the length of time defined using PutLifecycleHook. |
RecordLifecycleActionHeartbeat |
| Resume Processes | Resumes the specified suspended Auto Scaling processes, or all suspended process, for a specified Auto Scaling group. | ResumeProcesses |
| Set Desired Capacity | Sets the size of a specified Auto Scaling group. | SetDesiredCapacity |
| Set Instance Health | Sets the health status of a specified instance. | SetInstanceHealth |
| Suspend Processes | Suspends the specified Auto Scaling processes, or all processes, for a specified Auto Scaling group. | SuspendProcesses |
| Terminate Instance In Auto Scaling Group | Makes a termination request for a specified instance and optionally adjusts the desired group size. | TerminateInstanceInAutoScalingGroup |
| Update Auto Scaling Group | Updates the configuration for a specified Auto Scaling group. | UpdateAutoScalingGroup |
Amazon CloudWatch is a monitoring service available for an AWS account. This service can monitor the AWS resources and the applications running in the environment.
The CloudTrail data source provides normalization for the event types supported by the Amazon CloudWatch API (https://docs.aws.amazon.com/AmazonCloudWatch/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Delete Alarms | Deletes the specified alarms | DeleteAlarms |
| Describe Alarm History |
Returns the history for a specified alarm, or all alarms if an alarm name is not specified CloudWatch retains the history of an alarm even if you delete the alarm. |
DescribeAlarmHistory |
| Describe Alarms |
Returns a specified alarm, or all alarms if an alarm name is not specified |
DescribeAlarms |
| Describe Alarms For Metric | Returns the alarms for a specified metric | DescribeAlarmsForMetric |
| Disable Alarm Actions |
Disables the actions for the specified alarms |
DisableAlarmActions |
| Enable Alarm Actions | Enables the actions for the specified alarms | EnableAlarmActions |
| Get Metric Statistics | Returns statistics for the specified metric | GetMetricStatistics |
| List Metrics | Returns a list of the specified metrics | ListMetrics |
| Put Metric Alarm | Creates or updates an alarm and associates it with a specified metric | PutMetricAlarm |
| Put Metric Data |
Publishes metric data points to Amazon CloudWatch CloudWatch associates the data points with the specified metric. If the specified metric does not exist, CloudWatch creates the metric. |
PutMetricData |
| Set Alarm State | Temporarily sets the state of an alarm for testing purposes | SetAlarmState |
Amazon DynamoDB is a database service available for an AWS account. This service can manage a database table used to store and retrieve any amount of data, and serve any level of request traffic.
The CloudTrail data source provides normalization for the event types supported by the Amazon DynamoDB API (https://docs.aws.amazon.com/amazondynamodb/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Batch Get Item | Returns the attributes of one or more items from one or more database tables | BatchGetItem |
| Batch Write Item | Puts or deletes multiple items in one or more database tables | BatchWriteItem |
| Create Table | Adds a new database table to the AWS account | CreateTable |
| Delete Item | Deletes a single item in a database table by primary key | DeleteItem |
| Delete Table | Deletes a database table and all of its items | DeleteTable |
| Describe Table | Retrieves information about a database table, including the current status of the table, the creation date/time, the primary key schema, and any indexes on the table | DescribeTable |
| Get Item | Returns a set of attributes for an item with the given primary key | GetItem |
| List Tables | Returns an array of database table names associated with the current account and endpoint | ListTables |
| Put Item | Creates a new item, or replaces an old item with a new item | PutItem |
| Query | Finds and returns items based on primary key values | Query |
| Scan | Returns one or more items and item attributes by accessing every item in a database table or a secondary index | Scan |
| Update Item | Edits the attributes for an existing item, or adds a new item to the database table if it does not already exist | UpdateItem |
| Update Table | Modifies the provisioned throughput settings, global secondary indexes, or DynamoDB Streams settings for a specified database table | UpdateTable |
Amazon ElastiCache is a distributed caching service available for an AWS account. This service provides simple scaling and cluster failure handling to avoid the overhead of a self-managed cache solution deployment. Applications using ElastiCache must be running on Amazon EC2, and Amazon EC2 security groups are used as the authorization mechanism.
The CloudTrail data source provides normalization for the event types supported by the Amazon ElastiCache API (https://docs.aws.amazon.com/AmazonElastiCache/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Authorize Cache Security Group Ingress | Allows network ingress to a cache security group | AuthorizeCacheSecurityGroupIngress |
| Create Cache Cluster | Creates a new cache cluster | CreateCacheCluster |
| Create Cache Parameter Group |
Creates a new Amazon ElastiCache cache parameter group An ElastiCache cache parameter group is a collection of parameters and their values that are applied to all of the nodes in any cluster or replication group using the CacheParameterGroup. |
CreateCacheParameterGroup |
| Create Cache Security Group | Creates a new cache security group that is used to control access to one or more clusters | CreateCacheSecurityGroup |
| Create Cache Subnet Group | Creates a new cache subnet group for use with clusters in an Amazon Virtual Private Cloud (VPC). | CreateCacheSubnetGroup |
| Create Replication Group | Creates a Redis (cluster mode disabled) or a Redis (cluster mode enabled) replication group | CreateReplicationGroup |
| Delete Cache Cluster | Deletes a previously provisioned cluster | DeleteCacheCluster |
| Delete Cache Parameter Group | Deletes a specified cache parameter group | DeleteCacheParameterGroup |
| Delete Cache Security Group | Deletes a specified cache security group | DeleteCacheSecurityGroup |
| Delete Cache Subnet Group | Deletes a cache subnet group if it is not associated with any clusters | DeleteCacheSubnetGroup |
| Delete Replication Group | Deletes a specified replication group | DeleteReplicationGroup |
| Describe Cache Clusters | Retrieves information about a specified cache cluster, or all provisioned clusters if no cluster identifier is specified | DescribeCacheClusters |
| Describe Cache Engine Versions | Returns a list of the available cache engines and their versions | DescribeCacheEngineVersions |
| Describe Cache Parameter Groups | Returns a list of cache parameter group descriptions | DescribeCacheParameterGroups |
| Describe Cache Parameters | Returns the detailed parameter list for a specified cache parameter group | DescribeCacheParameters |
| Describe Cache Security Groups | Returns a list of cache security group descriptions | DescribeCacheSecurityGroups |
| Describe Cache Subnet Groups | Returns a list of cache subnet group descriptions | DescribeCacheSubnetGroups |
| Describe Replication Groups | Returns information about a specified replication group | DescribeReplicationGroups |
| Describe Reserved Cache Nodes | Returns information about all reserved cache nodes for the account, or a specified reserved cache node | DescribeReservedCacheNodes |
| Describe Reserved Cache Nodes Offerings | Returns a list of available reserved cache node offerings | DescribeReservedCacheNodesOfferings |
| Modify Cache Cluster | Modifies the settings for a specified cluster | ModifyCacheCluster |
| Modify Cache Parameter Group | Modifies the parameters of a specified cache parameter group | ModifyCacheParameterGroup |
| Modify Cache Subnet Group | Modifies a specified cache subnet group | ModifyCacheSubnetGroup |
| Modify Replication Group | Modifies the settings for a specified replication group | ModifyReplicationGroup |
| Purchase Reserved Cache Nodes Offering | Used to purchase a reserved cache node offering | PurchaseReservedCacheNodesOffering |
| Reboot Cache Cluster | Reboots some, or all, of the cache nodes within a provisioned cluster | RebootCacheCluster |
| Reset Cache Parameter Group | Modifies the parameters of a specified cache parameter group to the engine or system default value | ResetCacheParameterGroup |
| Revoke Cache Security Group Ingress | Revokes ingress from a cache security group | RevokeCacheSecurityGroupIngress |
Amazon Relational Database Service (Amazon RDS) is a relational database service available for an AWS account. This service provides cost-efficient, resizable capacity for an industry-standard relational database and manages common database administration tasks to support applications running the cloud environment.
The CloudTrail data source provides normalization for the event types supported by the Amazon RDS API (https://docs.aws.amazon.com/AmazonRDS/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Source Identifier To Subscription | Adds a source identifier to an existing RDS event notification subscription | AddSourceIdentifierToSubscription |
| Add Tags To Resource | Adds metadata tags to an Amazon RDS resource | AddTagsToResource |
| Authorize DB Security Group Ingress | Enables ingress to a DBSecurityGroup using one of two forms of authorization | AuthorizeDBSecurityGroupIngress |
| Copy DB Parameter Group | Copies the specified DB parameter group | CopyDBParameterGroup |
| Copy DB Snapshot | Copies the specified DB snapshot, which must be in an available state | CopyDBSnapshot |
| Copy Option Group | Copies the specified option group | CopyOptionGroup |
| Create DB Instance | Creates a new DB instance | CreateDBInstance |
| Create DB Instance Read Replica | Creates a new DB instance that acts as a Read Replica for an existing source DB instance | CreateDBInstanceReadReplica |
| Create DB Parameter Group | Creates a new DB parameter group | CreateDBParameterGroup |
| Create DB Security Group | Creates a new DB security group, which is used to control access to a DB instance | CreateDBSecurityGroup |
| Create DB Snapshot | Creates a DBSnapshot from a DB instance that is in an available state | CreateDBSnapshot |
| Create DB Subnet Group | Creates a new DB subnet group | CreateDBSubnetGroup |
| Create Event Subscription | Creates an RDS event notification subscription | CreateEventSubscription |
| Create Option Group | Creates a new option group | CreateOptionGroup |
| Delete DB Instance |
Deletes a previously provisioned DB instance This operation deletes all automated backups for that instance and they cannot be recovered. |
DeleteDBInstance |
| Delete DB Parameter Group | Deletes a specified DB Parameter Group that is not associated with any DB instances | DeleteDBParameterGroup |
| Delete DB Security Group | Deletes a specified DB security group that is not associated with any DB instances | DeleteDBSecurityGroup |
| Delete DB Snapshot | Deletes a specified DB Snapshot that is in the available state | DeleteDBSnapshot |
| Delete DB Subnet Group | Deletes a specified DB subnet group that is not associated with any DB instances | DeleteDBSubnetGroup |
| Delete Event Subscription | Deletes an RDS event notification subscription | DeleteEventSubscription |
| Delete Option Group | Deletes a specified option group | DeleteOptionGroup |
| Describe DB Engine Versions | Returns a list of the available DB engines | DescribeDBEngineVersions |
| Describe DB Instances | Returns information about provisioned RDS instances | DescribeDBInstances |
| Describe DB Log Files | Returns a list of DB log files for a specified DB instance | DescribeDBLogFiles |
| Describe DB Parameter Groups | Returns a list of DB Parameter Group descriptions | DescribeDBParameterGroups |
| Describe DB Parameters | Returns the detailed parameter list for a specified DB parameter group | DescribeDBParameters |
| Describe DB Security Groups | Returns a list of DB Security Group descriptions | DescribeDBSecurityGroups |
| Describe DB Snapshots | Returns information about DB snapshots for a specified DB instance | DescribeDBSnapshots |
| Describe DB Subnet Groups | Returns a list of DB Subnet Group descriptions | DescribeDBSubnetGroups |
| Describe Engine Default Parameters | Returns the default engine and system parameter information for the specified database engine | DescribeEngineDefaultParameters |
| Describe Event Categories | Returns a list of categories for all event source types, or for a specified source type | DescribeEventCategories |
| Describe Events | Returns events related to DB instances, DB security groups, DB snapshots, and DB parameter groups for the past 14 days | DescribeEvents |
| Describe Event Subscriptions | Returns subscription descriptions for the account, including Subscription Name, SNS Topic ARN, Customer ID, Source Type, Source ID, Creation Time, and Status | DescribeEventSubscriptions |
| Describe Option Group Options | Returns a list of all available options for Option Groups | DescribeOptionGroupOptions |
| Describe Option Groups | Returns a list of all available Option Groups | DescribeOptionGroups |
| Describe Orderable DB Instance Options | Returns a list of orderable DB instance options for the specified engine | DescribeOrderableDBInstanceOptions |
| Describe Reserved DB Instances | Returns information about reserved DB instances for the account, or about a specified reserved DB instance | DescribeReservedDBInstances |
| Describe Reserved DB Instances Offerings | Returns a list of available reserved DB instance offerings | DescribeReservedDBInstancesOfferings |
| Download DB Log File Portion | Downloads all or a portion of the specified log file, up to 1 MB in size | DownloadDBLogFilePortion |
| List Tags For Resource | Returns a list of all tags on a specified Amazon RDS resource | ListTagsForResource |
| Modify DB Instance | Updates the settings for a specified DB instance | ModifyDBInstance |
| Modify DB Parameter Group | Updates the parameters of a specified DB parameter group | ModifyDBParameterGroup |
| Modify DB Subnet Group | Updates the settings for a specified DB Subnet group | ModifyDBSubnetGroup |
| Modify Event Subscription | Updates the settings for a specified RDS event notification subscription | ModifyEventSubscription |
| Modify Option Group | Updates the settings for a specified Option Group | ModifyOptionGroup |
| Promote Read Replica | Promotes a Read Replica DB instance to a standalone DB instance | PromoteReadReplica |
| Purchase Reserved DB Instances Offering | Used to purchase a reserved DB instance offering | PurchaseReservedDBInstancesOffering |
| Reboot DB Instance |
Reboots the specified DB instance, usually for changes to take effect Rebooting a DB instance restarts the database engine service and results in a momentary outage. |
RebootDBInstance |
| Remove Source Identifier From Subscription | Removes a source identifier from a specified RDS event notification subscription | RemoveSourceIdentifierFromSubscription |
| Remove Tags From Resource | Removes metadata tags from a specified Amazon RDS resource | RemoveTagsFromResource |
| Reset DB Parameter Group | Updates the parameters of a DB parameter group to the engine/system default value, or only the specified parameters | ResetDBParameterGroup |
| Restore D B Instance From D B Snapshot | Creates a new DB instance from a specified DB snapshot | RestoreDBInstanceFromDBSnapshot |
| Restore DB Instance To Point In Time | Restores a specified DB instance to an arbitrary point in time | RestoreDBInstanceToPointInTime |
| Revoke DB Security Group Ingress | Revokes ingress from a DB Security Group for previously authorized IP ranges for EC2 or VPC Security Groups | RevokeDBSecurityGroupIngress |
Amazon Simple Workflow Service (Amazon SWF) is a build task management service available for an AWS account. This service coordinates tasks across an application, while managing intertask dependencies, scheduling, and concurrency in accordance with the logical flow of the application.
The CloudTrail data source provides normalization for the event types supported by the Amazon SWF API (https://docs.aws.amazon.com/amazonswf/latest/apireference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Count Closed Workflow Executions | Returns the number of closed workflow executions within the specified domain that meet the specified filtering criteria. | CountClosedWorkflowExecutions |
| Count Open Workflow Executions | Returns the number of open workflow executions within the specified domain that meet the specified filtering criteria. | CountOpenWorkflowExecutions |
| Count Pending Activity Tasks | Returns the estimated number of activity tasks in the specified task list. | CountPendingActivityTasks |
| Count Pending Decision Tasks | Returns the estimated number of decision tasks in the specified task list. | CountPendingDecisionTasks |
| Deprecate Activity Type |
Deprecates the specified activity type. After an activity type is deprecated, new tasks of that activity type cannot be created. Tasks of that type that were scheduled before deprecation continue to run. |
DeprecateActivityType |
| Deprecate Domain |
Deprecates the specified domain. After a domain is deprecated, it cannot be used to create new workflow executions or register new types. Deprecating a domain also deprecates all activity and workflow types registered in the domain. Executions that started before deprecation of the domain continue to run. |
DeprecateDomain |
| Deprecate Workflow Type |
Deprecates the specified workflow type. After a workflow type is deprecated, new executions of that type cannot be created. Executions that started before deprecation of the type continue to run. |
DeprecateWorkflowType |
| Describe Activity Type | Returns information about the specified activity type. | DescribeActivityType |
| Describe Domain | Returns information about the specified domain, including description and status. | DescribeDomain |
| Describe Workflow Execution | Returns information about the specified workflow execution, including its type and some statistics. | DescribeWorkflowExecution |
| Describe Workflow Type | Returns information about the specified workflow type. | DescribeWorkflowType |
| Get Workflow Execution History | Returns the history of the specified workflow execution. | GetWorkflowExecutionHistory |
| List Activity Types | Returns information about all activities registered in the specified domain that match the specified name and registration status. | ListActivityTypes |
| List Closed Workflow Executions | Returns a list of closed workflow executions in the specified domain that meet the filtering criteria. | ListClosedWorkflowExecutions |
| List Domains | Returns the list of domains registered in the account. | ListDomains |
| List Open Workflow Executions | Returns a list of open workflow executions in the specified domain that meet the filtering criteria. | ListOpenWorkflowExecutions |
| List Workflow Types | Returns information about workflow types in the specified domain. | ListWorkflowTypes |
| Poll For Activity Task | Initiates a long poll to return an Activity Task from the specified activity task list, where the service holds the HTTP connection open and responds as soon as a task becomes available. | PollForActivityTask |
| Poll For Decision Task | Initiates a long poll to return a Decision Task from the specified decision task list, where the service holds the HTTP connection open and responds as soon as a task becomes available. | PollForDecisionTask |
| Record Activity Task Heartbeat | Reports progress information about the Activity Task represented by the specified task token. | RecordActivityTaskHeartbeat |
| Register Activity Type | Registers a new activity type along with its configuration settings in the specified domain. | RegisterActivityType |
| Register Domain | Registers a new domain. | RegisterDomain |
| Register Workflow Type | Registers a new workflow type and its configuration settings in the specified domain. | RegisterWorkflowType |
| Request Cancel Workflow Execution | Records a Workflow Execution Cancel Requested event in the currently running workflow execution identified by the specified domain, workflow ID, and run ID. | RequestCancelWorkflowExecution |
| Respond Activity Task Canceled | Reports that the Activity Task identified by the specified task token was successfully canceled. | RespondActivityTaskCanceled |
| Respond Activity Task Completed | Reports that the Activity Task identified by the specified task token was successfully completed successfully with a result (if provided). | RespondActivityTaskCompleted |
| Respond Activity Task Failed | Reports that the Activity Task identified by the specified task token has failed with a reason (if specified). | RespondActivityTaskFailed |
| Respond Decision Task Completed | Reports that the Decision Task identified by the specified task token was successfully completed successfully. | RespondDecisionTaskCompleted |
| Signal Workflow Execution | Records a Workflow Execution Signaled event in the workflow execution history and creates a Decision Task for the workflow execution identified by the specified domain, workflow ID, and run ID. | SignalWorkflowExecution |
| Start Workflow Execution | Starts an execution of the workflow type in the specified domain using the specified workflow ID and input data. | StartWorkflowExecution |
| Terminate Workflow Execution | Records a Workflow Execution Terminated event and forces closure of the workflow execution identified by the specified domain, run ID, and workflow ID. | TerminateWorkflowExecution |
AWS CloudFormation is an infrastructure service available for an AWS account. This service leverages other AWS products, such as Amazon Elastic Compute Cloud, Amazon Simple Notification Service, Elastic Load Balancing, and Auto Scaling, to build applications using templates that define a collection of resources as a single unit called a stack.
The CloudTrail data source provides normalization for the event types supported by the AWS CloudFormation API (https://docs.aws.amazon.com/AWSCloudFormation/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Cancel Update Stack |
Cancels an update on the specified stack. This operation rolls back the stack update and reverts it to the previous stack configuration. |
CancelUpdateStack |
| Describe Stack Events | Returns all stack related events for a specified stack in reverse chronological order. | DescribeStackEvents |
| Describe Stack Resource | Returns a description of the specified resource in a specified stack. | DescribeStackResource |
| Describe Stack Resources | Returns AWS resource descriptions for running and deleted stacks. | DescribeStackResources |
| Estimate Template Cost | Returns a URL query for the estimated monthly cost of the specified template. | EstimateTemplateCost |
| Get Stack Policy | Returns the stack policy for a specified stack. | GetStackPolicy |
| Get Template | Returns the template body for a specified stack. | GetTemplate |
| Get Template Summary | Returns information about a new or existing template. | GetTemplateSummary |
| List Stack Resources | Returns descriptions of all resources of a specified stack. | ListStackResources |
| List Stacks | Returns the summary information for stacks matching the specified stack status filter. | ListStacks |
| Set Stack Policy | Sets a stack policy for a specified stack. | SetStackPolicy |
| Signal Resource | Sends a signal to the specified resource with a success or failure status. | SignalResource |
| Validate Template | Validates a specified template by checking for valid JSON or YAML. | ValidateTemplate |
AWS CloudTrail is a logging service available for an AWS account. This service records AWS API calls for your AWS account and delivers log files to an Amazon S3 bucket.
Note: The CloudTrail service logs events from the other AWS services, and you can create trails to deliver those logs to S3 buckets. These logged CloudTrail events reflect the actions used to manage your CloudTrail configurations, such as creating, updating, and deleting trails.
CloudTrail also supports logging non-API service events to an S3 bucket. These events are related to AWS services, but are not directly triggered by a request to a public AWS API.
- For AWS Service Events, the event type (event name) is AwsServiceEvent.
- For AWS Console Sign-In Events, the event type (event name) is Console Login.
The CloudTrail data source provides normalization for the event types supported by the AWS CloudTrail API (https://docs.aws.amazon.com/awscloudtrail/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Create Trail | Creates a trail that specifies the settings for delivery of log data to an Amazon S3 bucket. | CreateTrail |
| Delete Trail | Deletes a specified trail. | DeleteTrail |
| Describe Trails | Returns settings for the trail associated with the current region for the account. | DescribeTrails |
| Get Trail Status | Returns a JSON-formatted list of information about a specified trail, including delivery errors, Amazon SNS and Amazon S3 errors, and start and stop logging times for each trail. | GetTrailStatus |
| Start Logging | Starts the recording of AWS API calls and log file delivery for a specified trail. | StartLogging |
| Stop Logging | Suspends the recording of AWS API calls and log file delivery for a specified trail. | StopLogging |
| Update Trail | Updates the settings that specify delivery of log files for a specified trail. | UpdateTrail |
Amazon Simple Queue Service (Amazon SQS) is a queue service available for an AWS account. This service stores messages as they travel between applications or microservices and moves data between distributed application components.
The CloudTrail data source provides normalization for the event types supported by the Amazon SQS API (https://docs.aws.amazon.com/AWSSimpleQueueService/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Permission | Adds a permission to a queue for a specified principal, allowing sharing access to the queue. | AddPermission |
| Change Message Visibility | Changes the visibility timeout of a specified message in a queue to a new value, up to 12 hours. | ChangeMessageVisibility |
| Change Message Visibility Batch | Changes the visibility timeout of multiple specified messages. | ChangeMessageVisibilityBatch |
| Create Queue | Creates a new standard or FIFO (first in, first out) queue. | CreateQueue |
| Delete Message | Deletes the specified message from a specified queue. | DeleteMessage |
| Delete Message Batch | Deletes up to ten specified messages from a specified queue. | DeleteMessageBatch |
| Delete Queue |
Deletes a specified queue. After this operation completes, any messages in the queue are no longer available. |
DeleteQueue |
| Get Queue Attributes | Returns attributes for a specified queue. | GetQueueAttributes |
| Get Queue Url | Returns the URL of a specified queue. | GetQueueUrl |
| List Dead Letter Source Queues | Returns a list of queues that have the RedrivePolicy attribute configured with a dead-letter queue. | ListDeadLetterSourceQueues |
| List Queues | Returns a list of queues. | ListQueues |
| Receive Message | Returns one or more messages (up to 10) from a specified queue. | ReceiveMessage |
| Remove Permission | Revokes any permissions that match the specified Label parameter within the policy for a specified queue. | RemovePermission |
| Send Message | Delivers a message to a specified queue. | SendMessage |
| Send Message Batch | Delivers one or more messages (up to 10) to the specified queue. | SendMessageBatch |
| Set Queue Attributes | Sets the value of one or more attributes for the specified queue. | SetQueueAttributes |
The AWS Support service is a case management service available for an AWS account. This service enables developers to manage AWS Support cases programmatically. It uses HTTP methods that return results in JSON format.
The CloudTrail data source provides normalization for the event types supported by the AWS Support API (https://docs.aws.amazon.com/awssupport/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Attachments To Set | Adds one or more attachments to a specified attachment set, or creates a new attachment set. | AddAttachmentsToSet |
| Add Communication To Case | Adds additional customer communication to an AWS Support case. | AddCommunicationToCase |
| Create Case | Creates a new case in the AWS Support Center. | CreateCase |
| Describe Attachment | Returns the attachment that has the specified ID. | DescribeAttachment |
| Describe Cases | Returns a list of case IDs according to the specified attributes. | DescribeCases |
| Describe Communications | Returns communications (and attachments) for one or more support cases. | DescribeCommunications |
| Describe Services | Returns the current list of AWS services and a list of service categories that applies to each one. | DescribeServices |
| Describe Severity Levels | Returns the list of severity levels that you can assign to an AWS Support case. | DescribeSeverityLevels |
| Describe Trusted Advisor Check Refresh Statuses | Returns the refresh status of the Trusted Advisor checks that have a specified check IDs. | DescribeTrustedAdvisorCheckRefreshStatuses |
| Describe Trusted Advisor Check Result | Returns the results of the Trusted Advisor check that has the specified check ID. | DescribeTrustedAdvisorCheckResult |
| Describe Trusted Advisor Checks | Returns information about all available Trusted Advisor checks, including name, ID, category, description, and metadata. | DescribeTrustedAdvisorChecks |
| Describe Trusted Advisor Check Summaries | Returns the summaries of the results of the Trusted Advisor checks that have a specified check IDs. | DescribeTrustedAdvisorCheckSummaries |
| Refresh Trusted Advisor Check | Requests a refresh of the Trusted Advisor check that has a specified check ID. | RefreshTrustedAdvisorCheck |
| Resolve Case | Submits a request to resolve a specified case and returns the initial state of the case along with the state of the case after the request is completed. | ResolveCase |
Amazon Cognito Federated Identities is an identity management service available for an AWS account. This service provides scoped temporary credentials to mobile devices and other untrusted environments. It uniquely identifies a device and supplies the user with a consistent identity over the lifetime of an application.
The CloudTrail data source provides normalization for the event types supported by the Amazon Cognito Federated Identities API (https://docs.aws.amazon.com/cognitoidentity/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Create Identity Pool |
Creates a new identity pool The identity pool is a store of user identity information that is specific to the AWS account |
CreateIdentityPool |
| Delete Identity Pool | Deletes an identity pool | DeleteIdentityPool |
| Describe Identity Pool | Returns details about a specified identity pool, including the pool name, ID description, creation date, and current number of users | DescribeIdentityPool |
| Get Id | Generates (or retrieves) a Cognito ID | GetId |
| Get Open Id Token | Returns an OpenID token, using a known Cognito ID | GetOpenIdToken |
| Get Open Id Token For Developer Identity | Registers (or retrieves) a Cognito ID and an OpenID Connect token for a user authenticated by the backend authentication process. | GetOpenIdTokenForDeveloperIdentity |
| List Identities | Returns a list of identities in a specified identity pool | ListIdentities |
| List Identity Pools | Returns a list of the Cognito identity pools registered for the account | ListIdentityPools |
| Lookup Developer Identity | Returns the Identity ID associated with a specified Developer User Identifier or the list of Developer User Identifier values associated with a specified Identity ID | LookupDeveloperIdentity |
| Merge Developer Identities | Merges two users having different Identity IDs, existing in the same identity pool, and identified by the same developer provider | MergeDeveloperIdentities |
| Unlink Developer Identity | Unlinks a Developer User Identifier from an existing identity | UnlinkDeveloperIdentity |
| Unlink Identity | Unlinks a federated identity from a specified account | UnlinkIdentity |
| Update Identity Pool | Updates a specified identity pool | UpdateIdentityPool |
AWS Config is a configuration management service available for an AWS account. This service keeps track of the configurations of all the AWS resources associated with the AWS account. It can also provide the current and historical configurations of each AWS resource and information about the relationship between the resources.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS Config API (https://docs.aws.amazon.com/config/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Delete Delivery Channel | Deletes a specified delivery channel. | DeleteDeliveryChannel |
| Deliver Config Snapshot | Schedules delivery of a configuration snapshot to the Amazon S3 bucket in a specified delivery channel. | DeliverConfigSnapshot |
| Describe Configuration Recorders | Returns the details for a specified configuration recorder, or details for all configuration recorders associated with the account if not specified. | DescribeConfigurationRecorders |
| Describe Configuration Recorder Status | Returns the current status for a specified configuration recorder, or status for all configuration recorders associated with the account if not specified. | DescribeConfigurationRecorderStatus |
| Describe Delivery Channels | Returns the details for a specified delivery channel, or details for all delivery channels associated with the account if not specified. | DescribeDeliveryChannels |
| Describe Delivery Channel Status | Returns the current status for a specified delivery channel, or status for all delivery channels associated with the account if not specified. | DescribeDeliveryChannelStatus |
| Get Resource Config History | Returns a list of configuration items for a specified resource, including details about each state of the resource during the specified time interval. | GetResourceConfigHistory |
| Put Configuration Recorder | Creates a new configuration recorder to record the specified resource configurations. | PutConfigurationRecorder |
| Put Delivery Channel | Creates a delivery channel object to deliver configuration information to a specified Amazon S3 bucket and Amazon SNS topic. | PutDeliveryChannel |
| Start Configuration Recorder | Starts recording configurations of the AWS resources that are selected to record in the AWS account. | StartConfigurationRecorder |
| Stop Configuration Recorder | Stops recording configurations of the AWS resources that are selected to record in the AWS account. | StopConfigurationRecorder. |
AWS Data Pipeline is a workflow management service available for an AWS account. This service handles the details of scheduling and ensuring that data dependencies are met so that applications can focus on processing data.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS Data Pipeline API (https://docs.aws.amazon.com/datapipeline/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Activate Pipeline | Validates a specified pipeline and starts processing pipeline tasks. | ActivatePipeline |
| Create Pipeline | Creates a new, empty pipeline. | CreatePipeline |
| Delete Pipeline | Deletes a specified pipeline, its pipeline definition, and its run history. | DeletePipeline |
| Describe Objects | Returns the object definitions for a set of objects associated with a specified pipeline. | DescribeObjects |
| Describe Pipelines | Retrieves metadata about one or more specified pipelines, including the name of the pipeline, the pipeline identifier, its current state, and the user account that owns the pipeline. | DescribePipelines |
| Evaluate Expression | Evaluates a string in the context of a specified object. | EvaluateExpression |
| Get Pipeline Definition | Returns the definition of a specified pipeline. | GetPipelineDefinition |
| List Pipelines | Returns a list of pipeline identifiers for all active pipelines that the user has permission to access. | ListPipelines |
| Poll For Task | Returns a task to perform from AWS Data Pipeline to the task runner. | PollForTask |
| Put Pipeline Definition | Adds tasks, schedules, and preconditions to a specified pipeline. | PutPipelineDefinition |
| Query Objects | Queries a specified pipeline for the names of objects that match the specified set of conditions. | QueryObjects |
| Report Task Progress | Returns progress status for a specified task from AWS Data Pipeline to the task runner. | ReportTaskProgress |
| Report Task Runner Heartbeat | Returns operational status for a specified task from the task runner to AWS Data Pipeline. | ReportTaskRunnerHeartbeat |
| Set Status | Requests an update to the status of specified physical or logical pipeline objects in a specified pipeline. | SetStatus |
| Set Task Status | Returns a notification to AWS Data Pipeline that a task is completed and provides information about the final status. | SetTaskStatus |
| Validate Pipeline Definition | Validates a specified pipeline definition to ensure that it is well-formed and can be run without error. | ValidatePipelineDefinition |
AWS Direct Connect is a network connection service available for an AWS account. This service establishes private connectivity between AWS and a private data center, office, or co-location environment.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS Direct Connect API (https://docs.aws.amazon.com/directconnect/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Allocate Connection On Interconnect | Creates a hosted connection on an interconnect. | AllocateConnectionOnInterconnect |
| Allocate Private Virtual Interface | Provisions a private virtual interface to be owned by another AWS customer. | AllocatePrivateVirtualInterface |
| Allocate Public Virtual Interface | Provisions a public virtual interface to be owned by another AWS customer. | AllocatePublicVirtualInterface |
| Confirm Connection | Confirms the creation of a hosted connection on an interconnect. | ConfirmConnection |
| Confirm Private Virtual Interface | Accepts ownership of a private virtual interface created by another AWS customer. | ConfirmPrivateVirtualInterface |
| Confirm Public Virtual Interface | Accepts ownership of a public virtual interface created by another AWS customer. | ConfirmPublicVirtualInterface |
| Create Connection | Creates a new connection between a network and a specific AWS Direct Connect location. | CreateConnection |
| Create Interconnect | Creates a new interconnect between an AWS Direct Connect partner's network and a specific AWS Direct Connect location. | CreateInterconnect |
| Create Private Virtual Interface | Creates a new private virtual interface, which is a VLAN that transports AWS Direct Connect traffic and supports sending traffic to a single virtual private cloud (VPC). | CreatePrivateVirtualInterface |
| Create Public Virtual Interface | Creates a new public virtual interface, which is a VLAN that transports AWS Direct Connect traffic and supports sending traffic to public AWS services (such as Amazon S3). | CreatePublicVirtualInterface |
| Delete Connection | Deletes a specified connection. | DeleteConnection |
| Delete Interconnect | Deletes a specified interconnect. | DeleteInterconnect |
| Delete Virtual Interface | Deletes a specified virtual interface. | DeleteVirtualInterface |
| Describe Connections | Returns information about all connection for the region, or for a specified connection. | DescribeConnections |
| Describe Connections On Interconnect | Returns a list of connections that are provisioned on a specified interconnect. | DescribeConnectionsOnInterconnect |
| Describe Interconnects | Returns a list of interconnects owned by the AWS account. | DescribeInterconnects |
| Describe Locations | Returns the list of AWS Direct Connect locations in the current region. | DescribeLocations |
| Describe Virtual Gateways | Returns a list of virtual private gateways owned by the AWS account. | DescribeVirtualGateways |
| Describe Virtual Interfaces | Returns information for all virtual interfaces owned by the AWS account, virtual interfaces for a specified connection, or a single specified interface. | DescribeVirtualInterfaces |
AWS Elastic Beanstalk is a web application deployment service available for an AWS account. This service automatically handles the details of capacity provisioning, load balancing, scaling, and application health monitoring for the hosted web application.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS Elastic Beanstalk API (https://docs.aws.amazon.com/elasticbeanstalk/latest/api/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Check DNS Availability | Checks if the specified CNAME is available. | CheckDNSAvailability |
| Create Application | Creates an application that has one configuration template named default and no application versions. | CreateApplication |
| Create Application Version | Creates an application version for the specified application. | CreateApplicationVersion |
| Create Configuration Template |
Creates a configuration template. Templates are associated with a specific application and are used to deploy different versions of the application with the same configuration settings. |
CreateConfigurationTemplate |
| Create Environment | Launches an environment for the specified application using the specified configuration. | CreateEnvironment |
| Create Storage Location | Creates the Amazon S3 storage location for the account. | CreateStorageLocation |
| Delete Application |
Deletes the specified application along with all associated versions and configurations. The application versions will not be deleted from your Amazon S3 bucket. |
DeleteApplication |
| Delete Application Version | Deletes the specified version from the specified application. | DeleteApplicationVersion |
| Delete Configuration Template | Deletes the specified configuration template. | DeleteConfigurationTemplate |
| Delete Environment Configuration | Deletes the draft configuration associated with the running environment. | DeleteEnvironmentConfiguration |
| Describe Applications | Returns the descriptions of existing applications. | DescribeApplications |
| Describe Application Versions | Returns descriptions for existing application versions. | DescribeApplicationVersions |
| Describe Configuration Options |
Describes the configuration options that are used in a particular configuration template or environment or that a specified solution stack defines. The description includes the values the options their default values and an indication of the required action on a running environment if an option value is changed. |
DescribeConfigurationOptions |
| Describe Configuration Settings | Returns a description of the settings for the specified configuration set that is either a configuration template or the configuration set associated with a running environment. | DescribeConfigurationSettings |
| Describe Environment Resources | Returns AWS resources for this environment. | DescribeEnvironmentResources |
| Describe Environments | Returns descriptions for existing environments. | DescribeEnvironments |
| List Available Solution Stacks | Returns a list of the available solution stack names. | ListAvailableSolutionStacks |
| Rebuild Environment | Deletes and recreates all of the AWS resources (such as the Auto Scaling group load balancer) for a specified environment and forces a restart. | RebuildEnvironment |
| Request Environment Info | Initiates a request to compile the specified type of information of the deployed environment. | RequestEnvironmentInfo |
| Restart App Server | Causes the environment to restart the application container server running on each Amazon EC2 instance. | RestartAppServer |
| Retrieve Environment Info | Retrieves the compiled information from a Request Environment Info request. | RetrieveEnvironmentInfo |
| Swap Environment C N A M Es | Swaps the CNAMEs of two environments. | SwapEnvironmentCNAMEs |
| Terminate Environment | Terminates the specified environment. | TerminateEnvironment |
| Update Application | Updates the specified application to have the specified properties. | UpdateApplication |
| Update Application Version | Updates the specified application version to have the specified properties. | UpdateApplicationVersion |
| Update Configuration Template | Updates the specified configuration template to have the specified properties or configuration option values. | UpdateConfigurationTemplate |
| Update Environment | Updates the environment description, deploys a new application version, updates the configuration settings to an entirely new configuration template, or updates select configuration option values in the running environment. | UpdateEnvironment |
| Validate Configuration Settings | Takes a set of configuration settings and either a configuration template or environment and determines whether those values are valid. | ValidateConfigurationSettings |
Elastic Load Balancing is a traffic load management service available for an AWS account. This service distributes incoming traffic across EC2 instances, and monitors the health of its registered instances and ensures that it routes traffic only to healthy instances.
The CloudTrail data source currently translates the event name for the following event types supported by the Elastic Load Balancing API (https://docs.aws.amazon.com/elasticloadbalancing/2012-06-01/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Apply Security Groups To Load Balancer |
Associates one or more security groups with your load balancer in Amazon Virtual Private Cloud (Amazon VPC). The provided security group IDs override any currently applied security groups. |
ApplySecurityGroupsToLoadBalancer |
| Attach Load Balancer To Subnets | Adds one or more subnets to the set of configured subnets in the Amazon VPC for the load balancer. | AttachLoadBalancerToSubnets |
| Configure Health Check | Specifies the health check settings to use for evaluating the health state of your back-end instances. | ConfigureHealthCheck |
| Create App Cookie Stickiness Policy |
Generates a stickiness policy with sticky session lifetimes that follow that of an application-generated cookie. |
CreateAppCookieStickinessPolicy |
| Create Load Balancer Cookie Stickiness Policy |
Generates a stickiness policy with sticky session lifetimes controlled by the lifetime of the browser (user-agent) or a specified expiration period. |
CreateLBCookieStickinessPolicy |
| Create Load Balancer | Creates a new load balancer. | CreateLoadBalancer |
| Create Load Balancer Listeners |
Creates one or more listeners on a load balancer for the specified port. If a listener with the given port does not already exist it will be created. Otherwise, the properties of the new listener must match the properties of the existing listener. |
CreateLoadBalancerListeners |
| Create Load Balancer Policy |
Creates a new policy that contains the necessary attributes depending on the policy type. Policies are settings that are saved for the load balancer and that can be applied to the front-end listener or the back-end application server depending on the policy type. |
CreateLoadBalancerPolicy |
| Delete Load Balancer | Deletes the specified load balancer. | DeleteLoadBalancer |
| Delete Load Balancer Listeners | Deletes listeners from the load balancer for the specified port. | DeleteLoadBalancerListeners |
| Delete Load Balancer Policy |
Deletes a policy from the load balancer. The specified policy must not be enabled for any listeners. |
DeleteLoadBalancerPolicy |
| Deregister Instances From Load Balancer |
Deregisters instances from the load balancer. When the instance is deregistered, it will stop receiving traffic from the load balancer. |
DeregisterInstancesFromLoadBalancer |
| Describe Instance Health |
Returns the current state of the specified instances registered with the specified load balancer. |
DescribeInstanceHealth |
| Describe Load Balancer Attributes | Returns detailed information about all of the attributes associated with the specified load balancer. | DescribeLoadBalancerAttributes |
| Describe Load Balancer Policies |
Returns detailed descriptions of the policies. |
DescribeLoadBalancerPolicies |
| Describe Load Balancer Policy Types |
Returns meta-information on the specified load balancer policies defined by the Elastic Load Balancing service. |
DescribeLoadBalancerPolicyTypes |
| Describe Load Balancers |
Returns detailed configuration information for all the load balancers created for the account. |
DescribeLoadBalancers |
| Detach Load Balancer From Subnets | Removes subnets from the set of configured subnets in the Amazon VPC for the load balancer. | DetachLoadBalancerFromSubnets |
| Disable Availability Zones For Load Balancer | Removes the specified EC2 Availability Zones from the set of configured Availability Zones for the load balancer. | DisableAvailabilityZonesForLoadBalancer |
| Enable Availability Zones For Load Balancer | Adds one or more EC2 Availability Zones to the load balancer. | EnableAvailabilityZonesForLoadBalancer |
| Modify Load Balancer Attributes | Modifies the attributes of a specified load balancer. | ModifyLoadBalancerAttributes |
| Register Instances With Load Balancer | Adds new instances to the load balancer. | RegisterInstancesWithLoadBalancer |
| Set Load Balancer Listener S S L Certificate |
Sets the certificate that terminates SSL connections for the specified listener. The specified certificate replaces any prior certificate that was used on the same load balancer and port. |
SetLoadBalancerListenerSSLCertificate |
| Set Load Balancer Policies For Backend Server |
Replaces the current set of policies associated with a port on which the back-end server is listening with a new set of policies. |
SetLoadBalancerPoliciesForBackendServer |
| Set Load Balancer Policies Of Listener | Associates updates or disables a policy with a listener on the load balancer. | SetLoadBalancerPoliciesOfListener |
Amazon Elastic MapReduce (EMR) is a data management service available for an AWS account. This service uses Hadoop processing combined with several AWS products to do tasks such as web indexing, data mining, log file analysis, machine learning, scientific simulation, and data warehousing.
The CloudTrail data source currently translates the event name for the following event types supported by the Amazon EMR API (https://docs.aws.amazon.com/emr/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Instance Groups | Adds an instance group to a running cluster. | AddInstanceGroups |
| Add Job Flow Steps |
Adds new steps to a running job flow. A maximum of 256 steps are allowed in each job flow. |
AddJobFlowSteps |
| Add Tags |
Adds tags to an Amazon EMR resource. Tags make it easier to associate clusters in various ways, such as grouping clusters to track your Amazon EMR resource allocation costs. |
AddTags |
| Describe Cluster | Provides cluster-level details, including status hardware and software configuration VPC settings. | DescribeCluster |
| Describe Job Flows |
Returns a list of job flows that match all of the supplied parameters. This action is deprecated and will eventually be removed. |
DescribeJobFlows |
| Describe Step | Provides more detail about the cluster step. | DescribeStep |
| List Bootstrap Actions | Provides information about the bootstrap actions associated with a cluster. | ListBootstrapActions |
| List Clusters |
Provides the status of all clusters visible to the AWS account. |
ListClusters |
| List Instance Groups | Provides all available details about the instance groups in a cluster. | ListInstanceGroups |
| List Instances |
Provides information about the cluster instances that Amazon EMR provisions on behalf of a user when it creates the cluster. For example this operation indicates when the EC2 instances reach the Ready state when instances become available to Amazon EMR to use for jobs and the IP addresses for cluster instances. |
ListInstances |
| List Steps | Provides a list of steps for the cluster. | ListSteps |
| Modify Instance Groups |
Modifies the number of nodes and configuration settings of an instance group. |
ModifyInstanceGroups |
| Remove Tags |
Removes tags from an Amazon EMR resource. |
RemoveTags |
| Run Job Flow |
Creates and starts running a new job flow. |
RunJobFlow |
| Set Termination Protection |
Locks a job flow so that Amazon EC2 instances in the cluster cannot be terminated by user intervention, an API call, or in the event of a job-flow error. The cluster still terminates upon successful completion of the job flow. |
SetTerminationProtection |
| Set Visible To All Users |
Sets whether all AWS Identity and Access Management (IAM) users under your account can access the specified job flows. This action works on running job flows. |
SetVisibleToAllUsers |
| Terminate Job Flows |
Shuts a list of job flows down. When a job flow is shut down, any step not yet completed is canceled and the EC2 instances on which the job flow is running are stopped. Any log files not already saved are uploaded to Amazon S3 if a LogUri was specified when the job flow was created. |
TerminateJobFlows |
AWS Identity and Access Management (IAM) is a user account management service available for an AWS account. This service manage users and user permissions for the AWS account in order to secure AWS resources.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS IAM API (https://docs.aws.amazon.com/IAM/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Client I D To OpenID Connect Provider | Adds a new client ID (also known as an audience) to the list of client IDs already registered for the specified IAM OpenID Connect provider. | AddClientIDToOpenIDConnectProvider |
| Add role to instance profile | Adds the specified role to the specified instance profile. | AddRoleToInstanceProfile |
| Add user to group | Adds the specified user to the specified group. | AddUserToGroup |
| User updated their password |
Changes the password of the IAM user who is calling this action. The root account password is not affected by this action. |
ChangePassword |
| Create remote API access key |
Creates a new AWS secret access key and corresponding AWS access key ID for the specified user. The default status for new keys is Active. |
CreateAccessKey |
| Create account alias | Creates an alias for your AWS account. For information about using an AWS account alias. | CreateAccountAlias |
| Create user group | Creates a new group. | CreateGroup |
| Create instance profile | Creates a new instance profile. | CreateInstanceProfile |
| Create password for user | Creates a password for the specified user giving the user the ability to access AWS services through the AWS Management Console. | CreateLoginProfile |
| Create OpenID Connect Provider | Creates an IAM entity to describe an identity provider (IdP) that supports OpenID Connect (OIDC). | CreateOpenIDConnectProvider |
| Create a new user role | Creates a new role for your AWS account. | CreateRole |
| Create SAML provider | Creates an IAM entity to describe an identity provider (IdP) that supports SAML 2.0. | CreateSAMLProvider |
| Create new user | Creates a new user for your AWS account. | CreateUser |
| Create a virtual MFA device | Creates a new virtual MFA device for the AWS account. | CreateVirtualMFADevice |
| Disable MFA device | Deactivates the specified MFA device and removes it from association with the user name for which it was originally enabled. | DeactivateMFADevice |
| Delete remote API access key | Deletes the access key associated with the specified user. | DeleteAccessKey |
| Deletes the specified AWS account alias. | Deletes the specified AWS account alias. | DeleteAccountAlias |
| Delete password policy | Deletes the password policy for the AWS account. | DeleteAccountPasswordPolicy |
| Delete user group |
Deletes the specified group. The group cannot contain any users or have any attached policies. |
DeleteGroup |
| Remove access policy from group | Deletes the specified policy that is associated with the specified group. | DeleteGroupPolicy |
| Delete instance instance profile |
Deletes the specified instance profile. The instance profile cannot have an associated role. |
DeleteInstanceProfile |
| Disable user account (delete password) | Deletes the password for the specified user, which terminates the user's ability to access AWS services through the AWS Management Console. | DeleteLoginProfile |
| Delete OpenID Connect Provider | Deletes an IAM OpenID Connect identity provider. | DeleteOpenIDConnectProvider |
| Delete Role |
Deletes the specified role. The role cannot have any policies attached. |
DeleteRole |
| Remove access policy from role | Deletes the specified policy associated with the specified role. | DeleteRolePolicy |
| Delete SAML provider | Deletes a SAML provider. | DeleteSAMLProvider |
| Delete server certificate | Deletes the specified server certificate. | DeleteServerCertificate |
| Delete user's signing certificate | Deletes the specified signing certificate associated with the specified user. | DeleteSigningCertificate |
| Delete user |
Deletes the specified user. The user cannot belong to any groups have any keys or signing certificates or have any attached policies. |
DeleteUser |
| Delete user access policy | Deletes the specified policy associated with the specified user. | DeleteUserPolicy |
| Delete MFA device | Deletes a virtual MFA device. | DeleteVirtualMFADevice |
| Enable MFA device for user |
Enables the specified MFA device and associates it with the specified user name. When enabled, the MFA device is required for every subsequent login by the user name associated with the device. |
EnableMFADevice |
| Generate Credential Report | Generates a credential report for the AWS account. | GenerateCredentialReport |
| View password policy | Retrieves the password policy for the AWS account. | GetAccountPasswordPolicy |
| View account IAM status | Retrieves account level information about account entity usage and IAM quotas. | GetAccountSummary |
| Get Credential Report | Retrieves a credential report for the AWS account. | GetCredentialReport |
| View users in a group |
Returns a list of users that are in the specified group. |
GetGroup |
| View a group access policy |
Retrieves the specified policy document for the specified group. |
GetGroupPolicy |
| View instance profile details | Retrieves information about the specified instance profile including the instance profile's path GUID ARN and role. | GetInstanceProfile |
| View user creation history |
Retrieves the user name and password-creation date for the specified user. If the user has not been assigned a password, the action returns a 404 (NoSuchEntity) error. |
GetLoginProfile |
| Get Open I D Connect Provider | Returns information about the specified OpenID Connect provider. | GetOpenIDConnectProvider |
| View role details | Retrieves information about the specified role including the role's path, GUID, ARN, and the policy granting permission to assume the role. | GetRole |
| View policy for role | Retrieves the specified policy document for the specified role. | GetRolePolicy |
| View SAML Provider metadata | Returns the SAML provider metadocument that was uploaded when the provider was created or updated. | GetSAMLProvider |
| View server certificate details | Retrieves information about the specified server certificate. | GetServerCertificate |
| View user details | Retrieves information about the specified user including the user's creation date, path, unique ID, and ARN. | GetUser |
| View a user access policy | Retrieves the specified policy document for the specified user. | GetUserPolicy |
| View keys associated with user |
Returns information about the access key IDs associated with the specified user. If there are none the action returns an empty list. |
ListAccessKeys |
| View account aliases | Lists the account aliases associated with the account. | ListAccountAliases |
| View group access policies |
Lists the names of the policies associated with the specified group. If there are none the action returns an empty list. |
ListGroupPolicies |
| View groups with path | Lists the groups that have the specified path prefix. | ListGroups |
| View groups associated with user | Lists the groups for the specified user. | ListGroupsForUser |
| View instance profiles |
Lists the instance profiles that have the specified path prefix. If there are none the action returns an empty list. |
ListInstanceProfiles |
| View instance profiles for role |
Lists the instance profiles that have the specified associated role. If there are none the action returns an empty list. |
ListInstanceProfilesForRole |
| View MFA devices |
Lists the MFA devices. If the request includes the user name, the action lists all the MFA devices associated with the specified user name. If the request does not specify a user name, IAM determines the user name implicitly based on the AWS access key ID signing the request. |
ListMFADevices |
| List OpenID Connect Providers | Lists information about the OpenID Connect providers in the AWS account. | ListOpenIDConnectProviders |
| View policies for role |
Lists the names of the policies associated with the specified role. If there are none, the action returns an empty list. |
ListRolePolicies |
| View roles |
Lists the roles that have the specified path prefix. If there are none, the action returns an empty list. |
ListRoles |
| View SAML providers | Lists the SAML providers in the account. | ListSAMLProviders |
| View server certificates |
Lists the server certificates that have the specified path prefix. If none exist, the action returns an empty list. |
ListServerCertificates |
| View user's signing certificate |
Returns information about the signing certificates associated with the specified user. If there are none, the action returns an empty list. |
ListSigningCertificates |
| View access policies for user |
Lists the names of the policies associated with the specified user. If there are none, the action returns an empty list. |
ListUserPolicies |
| View users |
Lists the IAM users that have the specified path prefix. If no path prefix is specified, the action returns all users in the AWS account. If there are none, the action returns an empty list. |
ListUsers |
| View virtual MFA devices |
Lists the virtual MFA devices under the AWS account by assignment status. If the request does not specify an assignment status, the action returns a list of all virtual MFA devices. Assignment status can be Assigned, Unassigned, or Any. |
ListVirtualMFADevices |
| Add access policy to group | Adds (or updates) a policy document associated with the specified group. | PutGroupPolicy |
| Update role access policy | Adds (or updates) a policy document associated with the specified role. | PutRolePolicy |
| Update user access policy | Adds (or updates) a policy document associated with the specified user. | PutUserPolicy |
| Remove Client I D From OpenID Connect Provider | Removes the specified client ID (also known as audience) from the list of client IDs registered for the specified IAM OpenID Connect provider. | RemoveClientIDFromOpenIDConnectProvider |
| Remove role from instance profile | Removes the specified role from the specified instance profile. | RemoveRoleFromInstanceProfile |
| Remove users from group | Removes the specified user from the specified group. | RemoveUserFromGroup |
| Sync MFA device with AWS | Synchronizes the specified MFA device with AWS servers. | ResyncMFADevice |
| Enable / Disable API access key |
Changes the status of the specified access key from Active to Inactive or the reverse. This action can be used to disable a user's key as part of a key rotation work flow. |
UpdateAccessKey |
| Update password policy | Updates the password policy settings for the AWS account. | UpdateAccountPasswordPolicy |
| Grant user permission to assume role | Updates the policy that grants an entity permission to assume a role. | UpdateAssumeRolePolicy |
| Update group name or path | Updates the name and/or the path of the specified group. | UpdateGroup |
| Update password for user | Changes the password for the specified user. | UpdateLoginProfile |
| Update OpenID Connect Provider Thumbprint | Replaces the existing list of server certificate thumbprints with a new list. | UpdateOpenIDConnectProviderThumbprint |
| Update SAML provider settings | Updates the metadata document for an existing SAML provider. | UpdateSAMLProvider |
| Update server certificate | Updates the name and/or the path of the specified server certificate. | UpdateServerCertificate |
| Enable / Disable signing certificate |
Changes the status of the specified signing certificate from active to disabled or the reverse. This action can be used to disable a user's signing certificate as part of a certificate rotation work flow. |
UpdateSigningCertificate |
| Update user name or path | Updates the name and/or the path of the specified user. | UpdateUser |
| Create new server certificate (upload) |
Uploads a server certificate entity for the AWS account. The server certificate entity includes a public key certificate, a private key, and an optional certificate chain, which should all be PEM-encoded. |
UploadServerCertificate |
| Create signing certificate (upload) |
Uploads an X.509 signing certificate and associates it with the specified user. Some AWS services use X.509 signing certificates to validate requests that are signed with a corresponding private key. When you upload the certificate, its default status is Active. |
UploadSigningCertificate |
Amazon Kinesis Data Streams is a streaming data processing service available for an AWS account. This service provides elastic scaling for real-time processing of streaming big data, such as video.
The CloudTrail data source currently translates the event name for the following event types supported by the Amazon Kinesis Data Streams Service API (https://docs.aws.amazon.com/kinesis/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Add Tags To Stream | Adds or updates tags for the specified Kinesis data stream. | AddTagsToStream |
| Create Stream |
Creates a Kinesis data stream. A stream captures and transports data records that are continuously emitted from different data sources or producers. |
CreateStream |
| Delete Stream | Deletes a Kinesis data stream and all its shards and data. | DeleteStream |
| Describe Stream | Returns information for the specified Kinesis data stream, including the stream name, Amazon Resource Name (ARN), creation time, enhanced metric configuration, and shard map. | DescribeStream |
| Get Records | Returns data records from a Kinesis data stream's shard. | GetRecords |
| Get Shard Iterator |
Returns an Amazon Kinesis shard iterator. A shard iterator expires five minutes after it is returned to the requester. |
GetShardIterator |
| List Streams | Lists your Kinesis data streams. | ListStreams |
| List Tags For Stream | Lists the tags for the specified Kinesis data stream. | ListTagsForStream |
| Merge Shards | Merges two adjacent shards in a Kinesis data stream and combines them into a single shard to reduce the stream's capacity to ingest and transport data. | MergeShards |
| Put Record | Writes a single data record into an Amazon Kinesis data stream. | PutRecord |
| Remove Tags From Stream | Removes tags from the specified Kinesis data stream. | RemoveTagsFromStream |
| Split Shard | Splits a shard into two new shards in the Kinesis data stream, to increase the stream's capacity to ingest and transport data. | SplitShard |
AWS Key Management Service (AWS KMS) is an encryption and key management service available for an AWS account. This service provides encryption and key management functionality used by other AWS services and applications running in the AWS environment.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS KMS API (https://docs.aws.amazon.com/kms/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Create Alias | Creates a display name for a customer master key (CMK). | CreateAlias |
| Create Grant | Adds a grant to a customer master key (CMK). | CreateGrant |
| Create Key | Creates a customer master key (CMK) in the AWS account. | CreateKey |
| Decrypt |
Decrypts ciphertext. Ciphertext is plaintext that has been previously encrypted by using any of the following operations: GenerateKeyData, GenerateDataKeyWithoutPlaintext, or Encrypt. |
Decrypt |
| Delete Alias | Deletes the specified alias. | DeleteAlias |
| Describe Key | Returns detailed information about the specified customer master key (CMK). | DescribeKey |
| Disable Key |
Sets the state of a customer master key (CMK) to disabled. This prevents its use for cryptographic operations. |
DisableKey |
| Disable Key Rotation | Disables automatic rotation of the key material for the specified customer master key (CMK). | DisableKeyRotation |
| Enable Key |
Sets the state of a customer master key (CMK) to enabled. This permits its use for cryptographic operations. |
EnableKey |
| Enable Key Rotation | Enables automatic rotation of the key material for the specified customer master key (CMK). | EnableKeyRotation |
| Encrypt | Encrypts plaintext into ciphertext by using a customer master key (CMK). | Encrypt |
| Generate Data Key | Returns a data encryption key that you can use in your application to encrypt data locally. | GenerateDataKey |
| Generate Data Key Without Plaintext |
Returns a data encryption key encrypted under a customer master key (CMK). This operation is identical to GenerateDataKey, but returns only the encrypted copy of the data key. |
GenerateDataKeyWithoutPlaintext |
| Generate Random | Returns a random byte string that is cryptographically secure. | GenerateRandom |
| Get Key Policy | Returns a key policy attached to the specified customer master key (CMK). | GetKeyPolicy |
| Get Key Rotation Status | Returns a Boolean value that indicates whether automatic rotation of the key material is enabled for the specified customer master key (CMK). | GetKeyRotationStatus |
| List Aliases | Lists of all aliases in the AWS account and region. | ListAliases |
| List Grants | Lists all grants for the specified customer master key (CMK). | ListGrants |
| List Key Policies | Lists the names of the key policies that are attached to a customer master key (CMK). | ListKeyPolicies |
| List Keys | Lists all customer master keys (CMKs) in the AWS account and region. | ListKeys |
| Put Key Policy | Attaches a key policy to the specified customer master key (CMK). | PutKeyPolicy |
| Re Encrypt | Encrypts data on the server side with a new customer master key (CMK) without exposing the plaintext of the data on the client side. | ReEncrypt |
| Retire Grant | Retires a grant. | RetireGrant |
| Revoke Grant | Revokes the specified grant for the specified customer master key (CMK). | RevokeGrant |
| Update Key Description | Updates the description of a customer master key (CMK). | UpdateKeyDescription |
AWS OpsWorks Stacks is an application management service available for an AWS account. This service provisions AWS resources, manages their configuration, deploys applications to those resources, and monitors their health.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS OpsWorks Stacks API (https://docs.aws.amazon.com/opsworks/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Assign Volume | Assigns one of the stack's registered Amazon EBS volumes to a specified instance. | AssignVolume |
| Associate Elastic Ip |
Associates one of the stack's registered Elastic IP addresses with a specified instance. An Elastic IP address is a static IPv4 address designed for dynamic cloud computing. |
AssociateElasticIp |
| Attach Elastic Load Balancer | Attaches an Elastic Load Balancing load balancer to a specified layer. | AttachElasticLoadBalancer |
| Clone Stack | Creates a clone of a specified stack. | CloneStack |
| Create App | Creates an app for a specified stack. | CreateApp |
| Create Deployment | Runs deployment or stack commands. | CreateDeployment |
| Create Instance | Creates an instance in a specified stack. | CreateInstance |
| Create Layer |
Creates a layer. Every stack contains one or more layers, each of which represents a stack component, such as a load balancer or a set of application servers. |
CreateLayer |
| Create Stack |
Creates a new stack. The stack is the top-level AWS OpsWorks Stacks entity. |
CreateStack |
| Create User Profile | Creates a new user profile. | CreateUserProfile |
| Delete App | Deletes a specified app. | DeleteApp |
| Delete Instance | Deletes a specified instance, which terminates the associated Amazon EC2 instance. | DeleteInstance |
| Delete Layer | Deletes a specified layer. | DeleteLayer |
| Delete Stack | Deletes a specified stack. | DeleteStack |
| Delete User Profile | Deletes a user profile. | DeleteUserProfile |
| Deregister Elastic Ip |
Deregisters a specified Elastic IP address. This makes the address available to be registered by another stack. |
DeregisterElasticIp |
| Deregister Rds Db Instance | Deregisters an Amazon RDS instance. | DeregisterRdsDbInstance |
| Deregister Volume |
Deregisters an Amazon EBS volume This makes the volume available to be registered by another stack. |
DeregisterVolume |
| Describe Apps | Returns a description of a specified set of apps. | DescribeApps |
| Describe Commands | Returns the results of specified commands. | DescribeCommands |
| Describe Deployments | Returns a description of a specified set of deployments. | DescribeDeployments |
| Describe Elastic Ips |
Returns information about the Elastic IP addresses. |
DescribeElasticIps |
| Describe Elastic Load Balancers | Returns the stack's Elastic Load Balancing instances. | DescribeElasticLoadBalancers |
| Describe Layers | Returns a description of one or more layers in a specified stack. | DescribeLayers |
| Describe Load Based Auto Scaling | Returns a description of load-based auto scaling configurations for specified layers. | DescribeLoadBasedAutoScaling |
| Describe My User Profile | Returns a description of the user's SSH information. | DescribeMyUserProfile |
| Describe Permissions | Returns a description of the permissions for a specified stack. | DescribePermissions |
| Describe Raid Arrays | Returns a description of an instance's RAID arrays. | DescribeRaidArrays |
| Describe Rds Db Instances | Returns a description of the Amazon RDS instances. | DescribeRdsDbInstances |
| Describe Service Errors | Returns a description of AWS OpsWorks Stacks service errors. | DescribeServiceErrors |
| Describe Stacks | Returns a description of one or more stacks. | DescribeStacks |
| Describe Stack Summary | Returns the number of layers and apps in a specified stack, and the number of instances in each state, such as running_setup or online. | DescribeStackSummary |
| Describe Time Based Auto Scaling | Returns a description of time-based auto scaling configurations for specified instances. | DescribeTimeBasedAutoScaling |
| Describe User Profiles | Returns a description of specified users. | DescribeUserProfiles |
| Detach Elastic Load Balancer | Detaches a specified Elastic Load Balancing instance from its layer. | DetachElasticLoadBalancer |
| Disassociate Elastic Ip |
Disassociates an Elastic IP address from its instance. The address remains registered with the stack. |
DisassociateElasticIp |
| Get Hostname Suggestion | Returns a generated host name for the specified layer, based on the current host name theme. | GetHostnameSuggestion |
| Reboot Instance | Reboots a specified instance. | RebootInstance |
| Register Elastic Ip | Registers an Elastic IP address with a specified stack. | RegisterElasticIp |
| Register Rds Db Instance | Registers an Amazon RDS instance with a stack. | RegisterRdsDbInstance |
| Register Volume | Registers an Amazon EBS volume with a specified stack. | RegisterVolume |
| Set Load Based Auto Scaling | Sets the load-based auto scaling configuration for a specified layer. | SetLoadBasedAutoScaling |
| Set Permission | Sets a user's permissions. | SetPermission |
| Set Time Based Auto Scaling | Sets the time-based auto scaling configuration for a specified instance. | SetTimeBasedAutoScaling |
| Start Instance | Starts a specified instance. | StartInstance |
| Start Stack | Starts a specified stack. | StartStack |
| Stop Instance |
Stops a specified instance. When stopping a standard instance, the data disappears and must be reinstalled at the restart for the instance. |
StopInstance |
| Stop Stack | Stops a specified stack. | StopStack |
| Unassign Volume |
Unassigns an assigned Amazon EBS volume. The volume remains registered with the stack. |
UnassignVolume |
| Update App | Updates a specified app. | UpdateApp |
| Update Elastic Ip | Updates a registered Elastic IP address's name. | UpdateElasticIp |
| Update Instance | Updates a specified instance. | UpdateInstance |
| Update Layer | Updates a specified layer. | UpdateLayer |
| Update My User Profile | Updates the user's SSH public key. | UpdateMyUserProfile |
| Update Rds Db Instance | Updates an Amazon RDS instance. | UpdateRdsDbInstance |
| Update Stack | Updates a specified stack. | UpdateStack |
| Update User Profile | Updates a specified user profile. | UpdateUserProfile |
| Update Volume | Updates an Amazon EBS volume's name or mount point. | UpdateVolume |
Amazon Redshift is a data warehouse service available for an AWS account. This service manages all of the work of setting up, operating, and scaling a data warehouse.
The CloudTrail data source currently translates the event name for the following event types supported by the Amazon Redshift API (https://docs.aws.amazon.com/redshift/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Authorize Cluster Security Group Ingress |
Adds an inbound (ingress) rule to an Amazon Redshift security group Depending on whether the application accessing a cluster is running on the Internet or an EC2 instance, this can authorize inbound access to either a Classless Interdomain Routing (CIDR) IP address range or an EC2 security group. |
AuthorizeClusterSecurityGroupIngress |
| Authorize Snapshot Access | Authorizes the specified AWS customer account to restore the specified snapshot | AuthorizeSnapshotAccess |
| Copy Cluster Snapshot | Copies the specified automated cluster snapshot to a new manual cluster snapshot | CopyClusterSnapshot |
| Create Cluster |
Creates a new cluster To create the cluster in virtual private cloud (VPC), this must specify the cluster subnet group name. The cluster subnet group identifies the subnets of the VPC that Amazon Redshift uses when creating the cluster. |
CreateCluster |
| Create Cluster Parameter Group |
Creates an Amazon Redshift parameter group Parameters in the parameter group define specific behavior that applies to the databases created on the cluster. |
CreateClusterParameterGroup |
| Create Cluster Security Group |
Creates a new Amazon Redshift security group Security groups are used to control access to non-VPC clusters. |
CreateClusterSecurityGroup |
| Create Cluster Snapshot |
Creates a manual snapshot of the specified cluster The cluster must be in the available state. |
CreateClusterSnapshot |
| Create Cluster Subnet Group |
Creates a new Amazon Redshift subnet group |
CreateClusterSubnetGroup |
| Create Hsm Client Certificate | Creates an HSM client certificate that an Amazon Redshift cluster will use to connect to the client's HSM in order to store and retrieve the keys used to encrypt the cluster databases | CreateHsmClientCertificate |
| Create Hsm Configuration |
Creates an HSM configuration that contains the information required by an Amazon Redshift cluster to store and use database encryption keys in a Hardware Security Module (HSM) |
CreateHsmConfiguration |
| Delete Cluster | Deletes a previously provisioned cluster | DeleteCluster |
| Delete Cluster Parameter Group | Deletes a specified Amazon Redshift parameter group | DeleteClusterParameterGroup |
| Delete Cluster Security Group | Deletes an Amazon Redshift security group. | DeleteClusterSecurityGroup |
| Delete Cluster Snapshot |
Deletes the specified manual snapshot The snapshot must be in the available state with no other users authorized to access the snapshot. |
DeleteClusterSnapshot |
| Delete Cluster Subnet Group | Deletes the specified cluster subnet group | DeleteClusterSubnetGroup |
| Delete Hsm Client Certificate | Deletes the specified HSM client certificate | DeleteHsmClientCertificate |
| Delete Hsm Configuration | Deletes the specified Amazon Redshift HSM configuration | DeleteHsmConfiguration |
| Describe Cluster Parameter Groups | Returns a list of Amazon Redshift parameter groups including created parameter groups and the default parameter group | DescribeClusterParameterGroups |
| Describe Cluster Parameters | Returns a detailed list of parameters contained within the specified Amazon Redshift parameter group | DescribeClusterParameters |
| Describe Clusters |
Returns properties of provisioned clusters including general cluster properties, cluster database properties, maintenance and backup properties, and security and access properties |
DescribeClusters |
| Describe Cluster Security Groups | Returns information about Amazon Redshift security groups | DescribeClusterSecurityGroups |
| Describe Cluster Snapshots |
Returns one or more snapshot objects which contain metadata about your cluster snapshots By default, this operation returns information about all snapshots of all clusters that are owned by the AWS customer account. It does not return information for snapshots owned by inactive AWS customer accounts. |
DescribeClusterSnapshots |
| Describe Cluster Subnet Groups |
Returns one or more cluster subnet group objects which contain metadata about your cluster subnet groups By default, this operation returns information about all cluster subnet groups that are defined in the AWS account. |
DescribeClusterSubnetGroups |
| Describe Cluster Versions | Returns descriptions of the available Amazon Redshift cluster versions. | DescribeClusterVersions |
| Describe Default Cluster Parameters | Returns a list of parameter settings for the specified parameter group family. | DescribeDefaultClusterParameters |
| Describe Hsm Client Certificates |
Returns information about the specified HSM client certificate. If no certificate ID is specified, it returns information about all the HSM certificates owned by the AWS customer account. |
DescribeHsmClientCertificates |
| Describe Hsm Configurations |
Returns information about the specified Amazon Redshift HSM configuration. If no configuration ID is specified, it returns information about all the HSM configurations owned by the AWS customer account. |
DescribeHsmConfigurations |
| Describe Logging Status | Returns status information about logging, such as queries and connection attempts being logged for the specified Amazon Redshift cluster. | DescribeLoggingStatus |
| Describe Orderable Cluster Options | Returns a list of orderable cluster options. | DescribeOrderableClusterOptions |
| Describe Reserved Node Offerings | Returns a list of the available reserved node offerings by Amazon Redshift with their descriptions, including the node type, the fixed and recurring costs of reserving the node, and duration the node will be reserved. | DescribeReservedNodeOfferings |
| Describe Reserved Nodes | Returns the descriptions of the reserved nodes. | DescribeReservedNodes |
| Describe Resize | Returns information about the last resize operation for the specified cluster. | DescribeResize |
| Disable Logging | Stops logging information such as queries and connection attempts for the specified Amazon Redshift cluster. | DisableLogging |
| Disable Snapshot Copy | Disables the automatic copying of snapshots from one region to another region for a specified cluster. | DisableSnapshotCopy |
| Enable Logging | Starts logging information, such as queries and connection attempts, for the specified Amazon Redshift cluster. | EnableLogging |
| Enable Snapshot Copy | Enables the automatic copy of snapshots from one region to another region for a specified cluster. | EnableSnapshotCopy |
| Modify Cluster | Modifies the settings for a cluster. | ModifyCluster |
| Modify Cluster Parameter Group | Modifies the parameters of a parameter group. | ModifyClusterParameterGroup |
| Modify Cluster Subnet Group |
Modifies a cluster subnet group to include the specified list of VPC subnets. This operation replaces the existing list of subnets with the new list of subnets. |
ModifyClusterSubnetGroup |
| Modify Snapshot Copy Retention Period | Modifies the number of days to retain automated snapshots in the destination region after they are copied from the source region. | ModifySnapshotCopyRetentionPeriod |
| Purchase Reserved Node Offering |
Submits a purchase for reserved nodes. |
PurchaseReservedNodeOffering |
| Reboot Cluster |
Reboots a cluster It results in a momentary outage to the cluster during which the cluster status is set to rebooting. A cluster event is created when the reboot is completed. Any pending cluster modifications are applied at this reboot. |
RebootCluster |
| Reset Cluster Parameter Group | Sets one or more parameters of the specified parameter group to their default values and sets the source values of the parameters to 'engine-default.' | ResetClusterParameterGroup |
| Restore From Cluster Snapshot | Creates a new cluster from a snapshot. | RestoreFromClusterSnapshot |
| Revoke Cluster Security Group Ingress | Revokes an ingress rule in an Amazon Redshift security group for a previously authorized IP range or Amazon EC2 security group. | RevokeClusterSecurityGroupIngress |
| Revoke Snapshot Access | Removes the ability of the specified AWS customer account to restore the specified snapshot. | RevokeSnapshotAccess |
| Rotate Encryption Key | Rotates the encryption keys for a cluster. | RotateEncryptionKey |
Amazon Simple Email Service (SES) is an email service available for an AWS account. This service provides a large-scale email solution that integrates with other AWS products.
The CloudTrail data source currently translates the event name for the following event types supported by the Amazon SES API (https://docs.aws.amazon.com/redshift/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Delete Identity | Deletes the specified identity (email address or domain) from the list of verified identities. | DeleteIdentity |
| Delete Verified Email Address | Deletes the specified email address from the list of verified addresses. | DeleteVerifiedEmailAddress |
| Get Identity Dkim Attributes |
Returns the current status of Easy DKIM signing for an entity. For domain name identities this action also returns the DKIM tokens that are required for Easy DKIM signing and whether Amazon SES has successfully verified that these tokens have been published. |
GetIdentityDkimAttributes |
| Get Identity Notification Attributes | Given a list of verified identities (email addresses and/or domains), returns a structure describing identity notification attributes. | GetIdentityNotificationAttributes |
| Get Identity Verification Attributes | Given a list of identities (email addresses and/or domains), returns the verification status and (for domain identities) the verification token for each identity. | GetIdentityVerificationAttributes |
| Get Send Quota | Returns the user's current sending limits. | GetSendQuota |
| Get Send Statistics |
Returns the user's sending statistics The result is a list of data points representing the last two weeks of sending activity. |
GetSendStatistics |
| List Verified Email Addresses | Returns a list containing all of the email addresses that are verified. | ListVerifiedEmailAddresses |
| Send Email | Composes an email message based on input data and queues the message for sending. | SendEmail |
| Send Raw Email |
Sends an email message with header and content specified by the client. |
SendRawEmail |
| Set Identity Dkim Enabled | Enables or disables Easy DKIM signing of email sent from an identity. | SetIdentityDkimEnabled |
| Set Identity Feedback Forwarding Enabled |
Given an identity (email address or domain), enables or disables whether Amazon SES forwards bounce and complaint notifications as email. |
SetIdentityFeedbackForwardingEnabled |
| Set Identity Notification Topic | Given an identity (email address or domain), sets the Amazon Simple Notification Service (Amazon SNS) topic to which Amazon SES will publish bounce complaint and/or delivery notifications for emails sent with that identity as the Source. | SetIdentityNotificationTopic |
| Verify Domain Dkim |
Returns a set of DKIM tokens for a domain. DKIM tokens are character strings that represent your domain's identity. |
VerifyDomainDkim |
| Verify Domain Identity | Verifies a domain. | VerifyDomainIdentity |
| Verify Email Address |
Verifies an email address. This action produces a verification email message sent to the specified address. |
VerifyEmailAddress |
| Verify Email Identity |
Adds an email address to the list of identities for the Amazon SES account in the current AWS region and attempts to verify it. This action produces a verification email message sent to the specified address. |
VerifyEmailIdentity |
Amazon Simple Notification Service (SNS) is a web messaging service available for an AWS account. This service enables hosted applications to easily push real-time notification messages to subscribers over multiple delivery protocols.
The CloudTrail data source currently translates the event name for the following event types supported by the Amazon SNS API (https://docs.aws.amazon.com/sns/latest/api/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Confirm Subscription |
Verifies an endpoint owner's intent to receive messages by validating the token sent to the endpoint by an earlier Subscribe action. If the token is valid, this action creates a new subscription and returns its Amazon Resource Name (ARN). |
ConfirmSubscription |
| Create Platform Application |
Creates a platform application object for one of the supported push notification services, such as APNS and GCM, to which devices and mobile apps may register. |
CreatePlatformApplication |
| Create Platform Endpoint |
Creates an endpoint for a device and mobile app on one of the supported push notification services, such as GCM and APNS. |
CreatePlatformEndpoint |
| Create Topic |
Creates a topic for notification publishing. |
CreateTopic |
| Delete Endpoint | Deletes the endpoint from Amazon SNS. | DeleteEndpoint |
| Delete Platform Application | Deletes a platform application object for one of the supported push notification services, such as APNS or GCM. | DeletePlatformApplication |
| Delete Topic |
Deletes a topic and all its subscriptions. Deleting a topic might prevent some messages previously sent to the topic from being delivered to subscribers. |
DeleteTopic |
| Get Endpoint Attributes | Retrieves the endpoint attributes for a device on one of the supported push notification services, such as GCM or APNS. | GetEndpointAttributes |
| Get Platform Application Attributes | Retrieves the attributes of the platform application object for the supported push notification services, such as APNS or GCM. | GetPlatformApplicationAttributes |
| Get Subscription Attributes | Returns all of the properties of a subscription. | GetSubscriptionAttributes |
| Get Topic Attributes | Returns all of the properties of a topic. | GetTopicAttributes |
| List Endpoints By Platform Application | Lists the endpoints and endpoint attributes for devices in a supported push notification service, such as GCM or APNS. | ListEndpointsByPlatformApplication |
| List Platform Applications | Lists the platform application objects for the supported push notification services, such as APNS or GCM. | ListPlatformApplications |
| List Subscriptions | Returns a list of the requester's subscriptions. | ListSubscriptions |
| List Subscriptions By Topic | Returns a list of the subscriptions to a specific topic. | ListSubscriptionsByTopic |
| List Topics | Returns a list of the requester's topics. | ListTopics |
| Publish |
Sends a message to all of a topic's subscribed endpoints. When a message ID is returned, the message has been saved and Amazon SNS will attempt to deliver it to the topic's subscribers. |
Publish |
| Set Endpoint Attributes | Sets the attributes for an endpoint for a device on one of the supported push notification services, such as GCM or APNS. | SetEndpointAttributes |
| Set Platform Application Attributes | Sets the attributes of the platform application object for the supported push notification services, such as APNS or GCM. | SetPlatformApplicationAttributes |
| Set Subscription Attributes | Allows a subscription owner to set an attribute of the topic to a new value. | SetSubscriptionAttributes |
| Set Topic Attributes | Allows a topic owner to set an attribute of the topic to a new value. | SetTopicAttributes |
| Subscribe | Prepares to subscribe an endpoint by sending the endpoint a confirmation message. | Subscribe |
| Unsubscribe | Deletes a subscription. | Unsubscribe |
AWS Storage Gateway is a cloud-based storage connection service available for an AWS account. This service enables an on-site software appliance to connect to the AWS storage infrastructure and securely upload data for backup and recovery.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS Storage Gateway API (https://docs.aws.amazon.com/storagegateway/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Activate Gateway | Activates the previously deployed gateway on the host and associates the gateway with your account. | ActivateGateway |
| Add Cache | Configures one or more gateway local disks as cache for a gateway. | AddCache |
| Add Upload Buffer | Configures one or more gateway local disks as upload buffer for a specified gateway. | AddUploadBuffer |
| Add Working Storage | Configures one or more gateway local disks as working storage for a gateway. | AddWorkingStorage |
| Cancel Archival | Cancels archiving of a virtual tape to the virtual tape shelf (VTS) after the archiving process is initiated. | CancelArchival |
| Cancel Retrieval | Cancels retrieval of a virtual tape from the VTS to a gateway after the retrieval process is initiated. | CancelRetrieval |
| Create Cached iSCSI Volume |
Creates a cached volume on a specified cached volume gateway. In response, the gateway creates the volume and returns information about it, including the volume Amazon Resource Name (ARN), its size, and the iSCSI target ARN that initiators can use to connect to the volume target. |
CreateCachediSCSIVolume |
| Create Snapshot From Volume Recovery Point | Initiates a snapshot of a gateway from a volume recovery point. | CreateSnapshotFromVolumeRecoveryPoint |
| Create Storedi S C S I Volume | Creates a volume on a specified gateway. | CreateStorediSCSIVolume |
| Create Tapes | Creates one or more virtual tapes. | CreateTapes |
| Delete Bandwidth Rate Limit | Deletes the bandwidth rate limits of a gateway. | DeleteBandwidthRateLimit |
| Delete Chap Credentials | Deletes Challenge-Handshake Authentication Protocol (CHAP) credentials for a specified iSCSI target and initiator pair. | DeleteChapCredentials |
| Delete Gateway | Deletes a specified gateway. | DeleteGateway |
| Delete Snapshot Schedule | Deletes a snapshot of a volume. | DeleteSnapshotSchedule |
| Delete Tape | Deletes the specified virtual tape. | DeleteTape |
| Delete Tape Archive | Deletes the specified virtual tape from the VTS. | DeleteTapeArchive |
| Describe Bandwidth Rate Limit | Returns the bandwidth rate limits of a gateway. | DescribeBandwidthRateLimit |
| Describe Cache |
Returns information about the cache of a gateway. The response includes disk IDs that are configured as cache, and it includes the amount of cache allocated and used. |
DescribeCache |
| Describe Cachedi S C S I Volumes | Returns a description of the gateway volumes specified in the request. | DescribeCachediSCSIVolumes |
| Describe Chap Credentials | Returns an array of CHAP credentials information for a specified iSCSI target, one for each target-initiator pair. | DescribeChapCredentials |
| Describe Gateway Information | Returns metadata about a gateway, such as its name, network interfaces, configured time zone, and the state. | DescribeGatewayInformation |
| Describe Maintenance Start Time | Returns the weekly maintenance start time for a gateway, including the day and time of the week. | DescribeMaintenanceStartTime |
| Describe Snapshot Schedule | Describes the snapshot schedule for the specified gateway volume. | DescribeSnapshotSchedule |
| Describe Stored iSCSI Volumes | Returns the description of the gateway volumes specified in the request. | DescribeStorediSCSIVolumes |
| Describe Tape Archives | Returns a description of specified virtual tapes in the VTS. | DescribeTapeArchives |
| Describe Tape Recovery Points | Returns a list of virtual tape recovery points that are available for the specified tape gateway. | DescribeTapeRecoveryPoints |
| Describe Tapes | Returns a description of the specified ARN of virtual tapes. | DescribeTapes |
| Describe Upload Buffer | Returns information about the upload buffer of a gateway. | DescribeUploadBuffer |
| Describe VTL Devices | Returns a description of VTL devices for the specified gateway. | DescribeVTLDevices |
| Describe Working Storage | Returns information about the working storage of a gateway. | DescribeWorkingStorage |
| Disable Gateway | Disables a tape gateway when the gateway is no longer functioning. | DisableGateway |
| List Gateways | Lists gateways owned by an AWS account in a specified region. | ListGateways |
| List Local Disks | Returns a list of the local disks for a specified gateway. | ListLocalDisks |
| List Volume Recovery Points | Lists the recovery points for a specified gateway. | ListVolumeRecoveryPoints |
| List Volumes | Lists the iSCSI stored volumes of a gateway, sorted by volume ARN. | ListVolumes |
| Retrieve Tape Archive | Retrieves an archived virtual tape from the VTS to a tape gateway. | RetrieveTapeArchive |
| Retrieve Tape Recovery Point | Retrieves the recovery point for the specified virtual tape. | RetrieveTapeRecoveryPoint |
| Shutdown Gateway |
Shuts down a specified gateway. The operation shuts down the gateway service component running in the gateway VM and not the host VM. |
ShutdownGateway |
| Start Gateway | Starts a gateway that was previously shut down. | StartGateway |
| Update Bandwidth Rate Limit | Updates the bandwidth rate limits of a gateway. | UpdateBandwidthRateLimit |
| Update Chap Credentials | Updates the CHAP credentials for a specified iSCSI target. | UpdateChapCredentials |
| Update Gateway Information | Updates a gateway metadata, which includes the gateway name and time zone. | UpdateGatewayInformation |
| Update Gateway Software Now | Executes an immediate update of the gateway VM software. | UpdateGatewaySoftwareNow |
| Update Maintenance Start Time | Updates a gateway weekly maintenance start time information, including day and time of the week. | UpdateMaintenanceStartTime |
| Update Snapshot Schedule | Updates a snapshot schedule configured for a gateway volume. | UpdateSnapshotSchedule |
| Update V T L Device Type | Updates the type of medium changer in a tape gateway. | UpdateVTLDeviceType |
AWS Security Token Service (STS) is a credential token service available for an AWS account. This service provides temporary, limited-privilege credentials for AWS Identity and Access Management (IAM) users or for authenticated (federated) users.
The CloudTrail data source currently translates the event name for the following event types supported by the AWS STS API (https://docs.aws.amazon.com/STS/latest/APIReference/Welcome.html).
Note: As Amazon adds other actions to the API that are not in the following list, the AWS Log Collection app parses the event and retains the raw value (API action) as the event name. Refer to the Amazon API documentation to determine these action names in order to use them as event names for rule conditions.
| Event type name | Event description | AWS reference |
|---|---|---|
| Assume Role |
Returns a set of temporary security credentials, consisting of an access key ID a secret access key and a security token. These credentials can be used to access AWS resources to which a user might not normally have access. |
AssumeRole |
| Assume Role With S A M L |
Returns a set of temporary security credentials for users who have been authenticated through a SAML authentication response. This operation provides a mechanism for tying an enterprise identity store or directory to role-based AWS access without user-specific credentials or configuration. |
AssumeRoleWithSAML |
| Assume Role With Web Identity |
Returns a set of temporary security credentials for users who have been authenticated in a mobile or web application with a web identity provider. Example providers include Amazon Cognito, Login with Amazon, Facebook, Google, or any OpenID Connect-compatible identity provider. |
AssumeRoleWithWebIdentity |
| Decode Authorization Message | Decodes additional information about the authorization status of a request from an encoded message returned in response to an AWS request. | DecodeAuthorizationMessage |
| Get Federation Token |
Returns a set of temporary security credentials for a federated user, consisting of an access key ID, a secret access key, and a security token. This operation is appropriate in contexts where those credentials can be safely stored usually in a server-based application. |
GetFederationToken |
| Get Session Token | Returns a set of temporary credentials for an AWS account or IAM user, consisting of an access key ID, a secret access key, and a security token. | GetSessionToken |
 Feedback
Feedback