 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
If the dashboard does not contain information and there are not detected vulnerabilities, click Run Authenticated Vulnerability Scan to run a scan to detect asset vulnerabilities. See Running Authenticated Asset Scans.
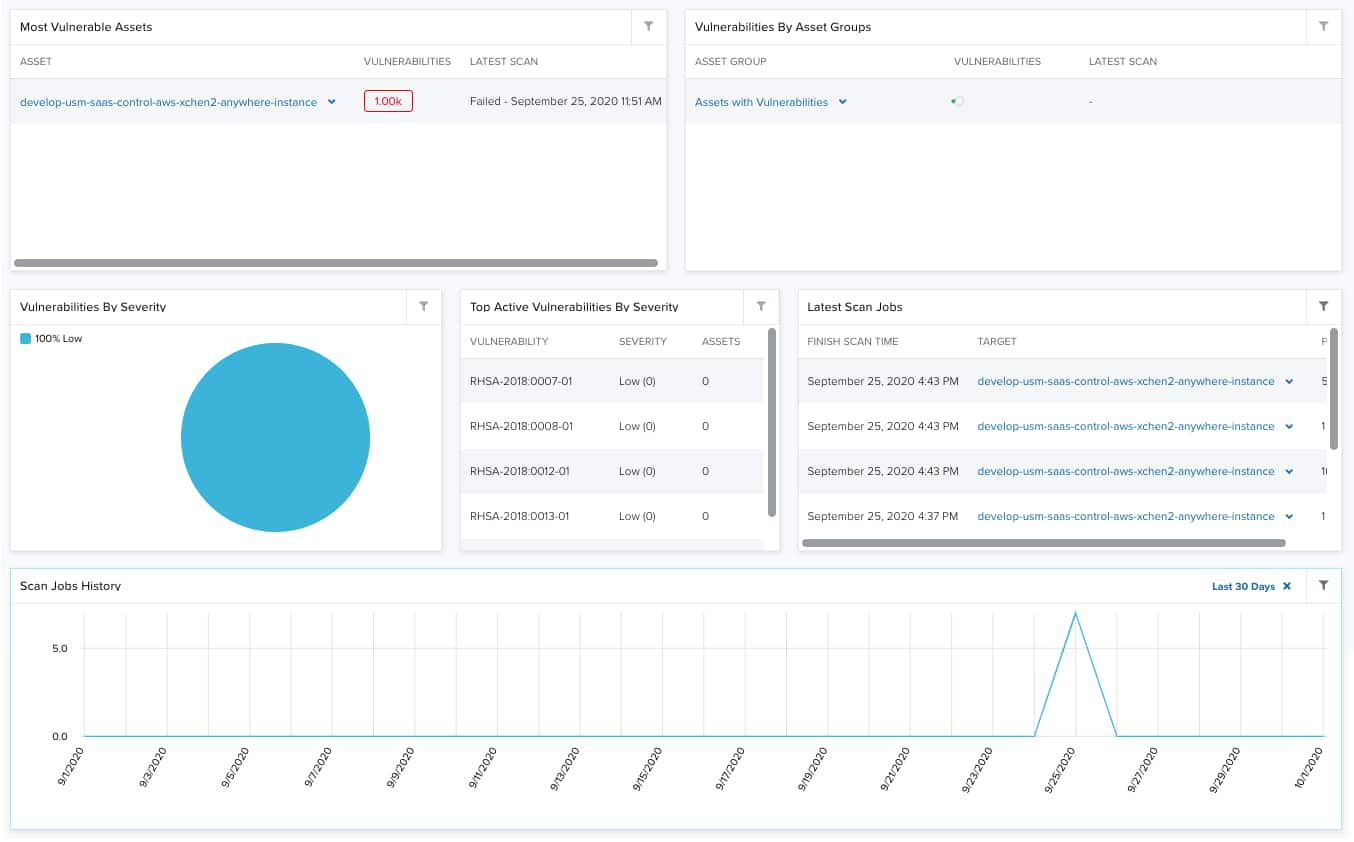
| Widgets | Description |
|---|---|
| Most Vulnerable Assets | List of most vulnerable assets in your environment. |
| Vulnerabilities by Asset Groups | List of most vulnerable asset groups in your environment. |
| Vulnerabilities by Severity | Pie chart displaying, in percentages, the severity of vulnerabilities, which can be Low, High, and Medium. See About Vulnerability Severity. |
| Top Active Vulnerabilities by Severity | List of the top active vulnerabilities by severity. You can see the CVE The CVE system provides a method, using CVE IDs, to reference publicly known information security vulnerability and exposures in publicly released software packages and environments. Identifier, its severity, and the affected assets. See About Vulnerability Severity. |
| Latest Scan Jobs | List of the 5 latest scans run in your environment. It includes the scan date and the number of vulnerabilities found. |
| Scan Jobs History | Graph that displays the total number vulnerability scans on each day in the current month. |
 Feedback
Feedback