To use the BlueApp for LevelBlue Forensics and Response for data collection and enforcement functions on remotes hosts, the target assets must meet the following requirements:
- The asset must be defined in the USM Anywhere asset inventory, be assigned to a sensor, and have configured credentials.
- A Windows asset must have PowerShell 3.0 or above installed.
- The Linux asset must be running Red Hat Enterprise Linux (RHEL) 5+, Fedora 14+, SUSE Desktop 10+, SUSE Enterprise Server 9+, Ubuntu 8.10+, or Debian 6.0+ with SSH Program to securely log into another computer over a network, execute commands in a remote machine, and move files from one machine to another through Secure Copy (SCP). enabled.
See System Settings for Authenticated Scans for information about configuring the host system to support remote management functions.
Access Rights for Credentials
USM Anywhere requires privileged access to execute system-level functions for monitored assets. Using an unprivileged account results in many "unknown" and potentially some "error" results. Make sure that you have credentials for the target assets that meet the following requirements:
-
For Windows systems, USM Anywhere uses Microsoft Windows Remote Management (WinRM) framework (version 2.0 or higher) to execute the corresponding commands. Therefore, if WinRM is unavailable on a target Windows system through the account credentials, USM Anywhere will be unable to connect.
Important: Only the members of the Remote Management Users and Administrators groups can log in through Web Services for Management (WS-Management).
- For Linux systems, USM Anywhere connects to the target host through SSH to run the supported functions. USM Anywhere supports the definition of credentials with
sudoprivilege escalation. It also supports login as a particular user followed by asuprivilege escalation, which executes every command as a root user.
Note: USM Anywhere does not support authenticated scans on Cisco IOS.
Manage Credentials for Your Assets
Before you use the BlueApp for LevelBlue Forensics and Response actions to perform collection and enforcement functions for your assets, you should make sure that each of the assets has assigned credentials that are able to connect to the system. In USM Anywhere, you can assign credentials for an individual asset An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. or for an asset group Asset groups are administratively created objects that group similar assets for specific purposes..
Note: Credentials assigned directly to an asset have higher priority than those assigned to an asset group.
When USM Anywhere runs a scan or executes a system-level action, it uses the credential set assigned directly to the asset, if there is one. If those credentials don't connect or the asset doesn't have an assigned credential set, it uses the credential set assigned to the group where the asset is a member, if that asset is a member of an asset group.
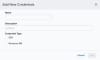
To add a new credential
-
Go to Settings > Credentials.
-
Click New Credentials.
The Add New Credential dialog box opens.
- Enter a name for the credential in the Name field and, if desired, a description to clarify its use in the Description field.
-
In Credential Type, select SSH Program to securely log into another computer over a network, execute commands in a remote machine, and move files from one machine to another through Secure Copy (SCP). or Windows RM based on the operating system Software that manages computer hardware resources and provides common services for computer programs. Examples include Microsoft Windows, Macintosh OS X, UNIX, and Linux. of the asset.
 Windows RM
Windows RM
Important: Only members of the Administrators or Remote Management Users groups are able to log in through WS-Management. The account used to log in to the target system must have remote and local log-on rights. See Setting Log on Locally and the Security Policy for more information.
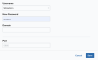
Use the Windows RM credential for a Windows operating system. After selecting Windows RM, complete these fields:
-
Username: Enter the username for the account with the required privileges.
Important: The username must have 20 characters or less.
- Password: Enter the password for the user account.
- Domain: (Optional.) Enter the domain name registered in the Domain Name System (DNS).
- Port: If an alternative port number is required, enter the port number. The default port, 5985, is standard.
Note: Use a fully qualified domain name (FQDN) instead of a Network Basic Input/Output System (NetBIOS) name. If you use a NetBIOS name, you will get an invalid SSH gateway error.
 SSH
SSH
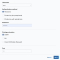
Use the SSH credential for a Linux, Apple macOS, or any other device that supports an SSH connection. After selecting SSH, complete these fields:
- Username: Enter the username for the account with the required privileges.
-
Authentication method: Set the SSH authentication mode and enter the password, private key, or both.
- Password: Select this option to use a simple password to authenticate the user account. It is mandatory if you do not use a private key Key used to decrypt and transform a message to plain text and generate signatures of the message. A private key is only known to the receiver, or both the sender and receiver. See also public key..
- Private key (no passphrase): Select this option to use a private key to authenticate the user account.
- Private key with passphrase: Select this option to use a private key and password combination to authenticate the user account.
Important: A private key must start with an appropriate header, such as "-----BEGIN RSA PRIVATE KEY----" and "-----END RSA PRIVATE KEY-----". Always copy the certificate Electronic document that uses a digital signature to bind a public key with an identity. Can be used to verify that a public key belongs to an individual. in the form with the header.
- Password: This field only appears if you select Password as authentication method. Enter the password that authenticates the user.
-
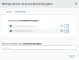
Privilege elevation: Select the elevated privilege to use for the credentials.
-
sudo A program for UNIX-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser.: Use this option to run single commands with root High-level user account with full administrative privileges. privileges. For example:
sudo 'command1'; sudo 'command2'; sudo 'command3' ...
-
su: Use this option to run single commands with superuser privileges. This requires you to enter the username and password for the superuser account. For example:
su username -c 'command1'; su username -c 'command2'; su username -c 'command3' ...
-
- Port: This is automatically set (SSH listens on port Endpoint of a communication stream identified by a unique integer number. Only one process per machine can listen on the same port number. 22 by default) and cannot be changed.
-
- Click Save.
There are a variety of ways to create an SSH key, and your company may already have predefined rules regarding an algorithm to use and what strength the key needs to be. However, if you need to create an SSH key manually and don't have a predefined company policy for the creation of the SSH key, you can use the following procedure to make a basic RSA SSH key to add to your credentials.
To create an SSH key manually
- Open the command line for Linux or Terminal for macOS.
-
Enter ssh-keyken to create a 2048-bit SSH key or ssh-keygen -b 4096 to create a 4096-bit SSH key, and then press Enter.
The command line prompts you to specify a file location.
-
Press Enter to use the default location (/home/<username>/.ssh/id_rsa for Linux, or /users/<username>/.ssh/id_rsa for macOS), or designate another location for the file.
The command line prompts you to specify a passphrase and enter it again to confirm it.
-
Specify a passphrase or, if you don't want to use a passphrase, leave the line blank, and then press Enter.
- The SSH key is saved to either the default location or the location you specified.
In USM Anywhere, you assign a defined credential set to an individual asset in order to use the credentials for authenticated scans, active directory (AD) scans, and BlueApp for Forensics and Response actions on the host. You can assign assets to a credential set in the Credentials page, or you can perform this task from the Assets page.
To assign a credential on the Credentials page
- Go to Settings > Credentials.
-
In the line of the credential you want to assign, click the
icon.
A dialog box opens.
-
Enter part of the asset name in the field at the bottom of the dialog box
This displays the matching items below the field. You can enter more text to filter the list further.
-
Select the asset to assign to the credential set.
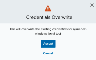
The credentials overwrite dialog box opens.
Warning: If the asset has already assigned credentials, these credentials are going to be overwritten.
-
Next to the displayed asset name, click Test to execute a test connection to the asset using the credentials.
If the test detects any warnings, a Permissions Warnings section displays. This section contains a Warning column that lists the individual warnings.
A permissions error doesn't prevent the scan from running, but it can result in the incomplete information being detailed in the scan results.
- Click the
icon to close the dialog box.
To assign a credential on the Assets page
- Go to Environment > Assets and locate the asset.
-
Next to the asset name, click the
icon and select Assign Credentials.
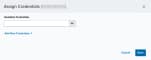
The assign credentials dialog box opens.
-
In the Available Credentials drop-down list, select the credential to use.
-
(Optional.) Select the Jump Box option if you want to authenticate through another asset.
Select the checkbox and use the field to search for the asset you want to use as an authentication server.
-
Click Test to execute a test connection to the asset using the selected credentials.
If the test detects any warnings, a Permissions Warnings section displays. This section contains a Warning column that lists the individual warnings and a Remediation that provides a suggested solution to resolve each warning. A permissions error doesn't prevent the scan from running, but it can result in the incomplete information being detailed in the scan results.
- Click Save.
Note: If the needed credentials do not already exist, you can select Add New Credentials to define them in USM Anywhere. See Creating Credentials for more information. Use the icon to modify any information.
In USM Anywhere, you assign a defined credential set to an asset group to use the credentials for authenticated scans, AD scans, and BlueApp Forensics and Response actions on members of the group. You can assign asset groups to a credential set in the Credentials page, or you can perform this task from the Asset Groups page.
Important: When you assign a credential to an asset group, USM Anywhere assigns the credential to the asset group instead of assigning it to all of its members.
To assign a credential on the Credentials page
- Go to Settings > Credentials.
-
In the line of the credential you want to assign, click the
icon.
A dialog box opens.
- Click the Asset Groups tab.
- At the bottom of the dialog box, enter part of the asset group name in the field.
-
Select the asset group to assign to the credential set.
- Click the
icon to close the dialog box.
This displays the matching items below the field. You can enter more text to filter the list further.
After you select the asset group, the dialog displays the item at the top. If needed, you can enter text for another asset group name and select it to assign multiple asset groups for the credential set.
To assign a credential on the Asset Groups page
- Go to Environment > Asset Groups.
-
Next to the asset name, click the
icon and select Assign Credentials.
The assign credentials dialog box opens.
-
In the Available Credentials drop-down list, select the credential to use.
- Click Save.
Note: If the needed credentials do not already exist, you can select Add New Credentials to define them in USM Anywhere. Use the icon to modify any information. Click Remove Current Credentials From Asset Group to remove that credential from the asset group.



 Feedback
Feedback