 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
USM Anywhere enables you to assign credentials to your assets. If the required credential set is not yet defined in USM Anywhere, you must add it before you can associate it with one or more assets. The Credentials page displays a list of all credential sets that are defined and available to be associated with an asset An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. or asset group Asset groups are administratively created objects that group similar assets for specific purposes..
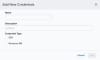
To add a new credential
-
Go to Settings > Credentials.
-
Click New Credentials.
The Add New Credential dialog box opens.
- Enter a name for the credential in the Name field and, if desired, a description to clarify its use in the Description field.
-
In Credential Type, select SSH Program to securely log into another computer over a network, execute commands in a remote machine, and move files from one machine to another through Secure Copy (SCP). or Windows RM based on the operating system Software that manages computer hardware resources and provides common services for computer programs. Examples include Microsoft Windows, Macintosh OS X, UNIX, and Linux. of the asset.
 Windows RM
Windows RM
Important: Only members of the Administrators or Remote Management Users groups are able to log in through WS-Management. The account used to log in to the target system must have remote and local log-on rights. See Setting Log on Locally and the Security Policy for more information.
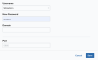
Use the Windows RM credential for a Windows operating system. After selecting Windows RM, complete these fields:
-
Username: Enter the username for the account with the required privileges.
Important: The username must have 20 characters or less.
- Password: Enter the password for the user account.
- Domain: (Optional.) Enter the domain name registered in the Domain Name System (DNS).
- Port: If an alternative port number is required, enter the port number. The default port, 5985, is standard.
Note: Use a fully qualified domain name (FQDN) instead of a Network Basic Input/Output System (NetBIOS) name. If you use a NetBIOS name, you will get an invalid SSH gateway error.
 SSH
SSH
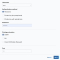
Use the SSH credential for a Linux, Apple macOS, or any other device that supports an SSH connection. After selecting SSH, complete these fields:
- Username: Enter the username for the account with the required privileges.
-
Authentication method: Set the SSH authentication mode and enter the password, private key, or both.
- Password: Select this option to use a simple password to authenticate the user account. It is mandatory if you do not use a private key Key used to decrypt and transform a message to plain text and generate signatures of the message. A private key is only known to the receiver, or both the sender and receiver. See also public key..
- Private key (no passphrase): Select this option to use a private key to authenticate the user account.
- Private key with passphrase: Select this option to use a private key and password combination to authenticate the user account.
Important: A private key must start with an appropriate header, such as "-----BEGIN RSA PRIVATE KEY----" and "-----END RSA PRIVATE KEY-----". Always copy the certificate Electronic document that uses a digital signature to bind a public key with an identity. Can be used to verify that a public key belongs to an individual. in the form with the header.
- Password: This field only appears if you select Password as authentication method. Enter the password that authenticates the user.
-
Privilege elevation: Select the elevated privilege to use for the credentials.
-
sudo A program for UNIX-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser.: Use this option to run single commands with root High-level user account with full administrative privileges. privileges. For example:
sudo 'command1'; sudo 'command2'; sudo 'command3' ...
-
su: Use this option to run single commands with superuser privileges. This requires you to enter the username and password for the superuser account. For example:
su username -c 'command1'; su username -c 'command2'; su username -c 'command3' ...
-
- Port: This is automatically set (SSH listens on port Endpoint of a communication stream identified by a unique integer number. Only one process per machine can listen on the same port number. 22 by default) and cannot be changed.
-
- Click Save.
There are a variety of ways to create an SSH key, and your company may already have predefined rules regarding an algorithm to use and what strength the key needs to be. However, if you need to create an SSH key manually and don't have a predefined company policy for the creation of the SSH key, you can use the following procedure to make a basic RSA SSH key to add to your credentials.
To create an SSH key manually
- Open the command line for Linux or Terminal for macOS.
-
Enter ssh-keyken to create a 2048-bit SSH key or ssh-keygen -b 4096 to create a 4096-bit SSH key, and then press Enter.
The command line prompts you to specify a file location.
-
Press Enter to use the default location (/home/<username>/.ssh/id_rsa for Linux, or /users/<username>/.ssh/id_rsa for macOS), or designate another location for the file.
The command line prompts you to specify a passphrase and enter it again to confirm it.
-
Specify a passphrase or, if you don't want to use a passphrase, leave the line blank, and then press Enter.
- The SSH key is saved to either the default location or the location you specified.

 Feedback
Feedback