 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
To install the LevelBlue Agent on Linux, you must run a script that you access from your USM Anywhere environment. When you run the installation on the Linux host system, the script downloads a .deb or .rpm file directly from USM Anywhere, and the agent automatically registers with your USM Anywhere environment. The installation process also configures a default set of paths to automatically support file integrity monitoring (FIM).
You can generate a script that is specific to a selected asset An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. in your USM Anywhere environment or generate a bulk deployment script that you can use to install the agent on multiple
At this time, agent support is limited to host systems running a 64-bit operating system (OS). Dependent libraries for 32-bit OS are not available.
Note: When you first deploy LevelBlue Agents on your host systems, you should install just a few to evaluate the events collected by the agent and the impact to your data consumption.
While there is no hard limit on the number of agents you can deploy, larger numbers of agents can eventually begin to impact the performance of USM Anywhere by transmitting more data than your pipeline can accommodate, causing latency in receiving and processing information.
Similarly, if your host system is consistently busy, such as a domain controller or an active directory (AD) server, deploying an agent on it may slow down its operations.
Note: LevelBlue Agents do not currently support the use of a proxy server.
Important: Before installing the Linux LevelBlue Agent, you should confirm that auditd is disabled on the targeted endpoint and is not configured to start at boot. This is because the agent uses syscalls to the kernel’s audit system to generate process events, which are then used in certain detection rules and queries. Official osquery documentation states that auditd should not be running when osquery is configured to use these syscalls because it can create a conflict with the osquery service over access to the audit Netlink socket.
Prerequisites
Before installing the LevelBlue Agent on a Linux host system, ensure that you have the prerequisites in place for that system.
-
The 64-bit Linux host system runs a Red Hat or Debian-based distribution, such as Ubuntu or Mint.
Note: The LevelBlue Agent installation has been tested on Ubuntu 14 and 16, a recent version of CentOS, Amazon Linux, and a handful of other Linux types. It is designed to work on any Linux version on 64-bit Intel that uses either APT or RPM to install packages.
-
Transport Layer Security (TLS) 1.2 must be enabled on the host system.
- rsyslog is installed on the host system (see https://www.rsyslog.com/).
- curl is installed on the host system (see https://curl.haxx.se/download.html).
- You have login credentials for the host system with sudo A program for UNIX-like computer operating systems that allows users to run programs with the security privileges of another user, by default the superuser. privileges.
Note: LevelBlue recommends that your host system has a minimum of 4 GB memory and 2 CPU cores.
You must configure your firewall to support ongoing event transmission to USM Anywhere.
Standard Firewall Setup
Your firewall needs to be configured to allow ongoing outbound connectivity from the host system using the HTTPS application protocol over port 443 to these USM Anywhere endpoints:
- <AWS region>-agent-entrypoint.alienvault.cloud (for example, eu-west-1-agent-entrypoint.alienvault.cloud)
See the LevelBlue Agent Endpoints by AWS Regions table for region-specific IP ranges.
- agent-packageserver.alienvault.cloud
-
api.agent.alienvault.cloud
-
prod-api.agent.alienvault.cloud
-
The package repo content is located in agent-packageserver.alienvault.cloud/repo/deb/ or agent-packageserver.alienvault.cloud/repo/rpm/
Important: The endpoints listed above are inside the 3.235.189.112/28 range.
GovCloud Setup
LevelBlue Threat Detection and Response for Government (LevelBlue TDR for Gov) customers need to configure ongoing outbound connectivity from the host system using the HTTPS application protocol over port 443 to these USM Anywhere endpoints:
- api.agent.gov.alienvault.us
- prod-api.agent.gov.alienvault.us
-
The package repo content is located in agent-packageserver.gov.alienvault.us/repo/deb/ or agent-packageserver.gov.alienvault.us/repo/rpm/
- us-gov-west-1-agent-entrypoint.gov.alienvault.us
Important: These endpoints are inside the 3.32.190.224/28 range.
For endpoints that rely on the Amazon Web Services (AWS) region, the endpoint to use depends on the AWS region where your USM Anywhere instance is deployed. See the following table for details. If you are unsure, consult the administrator who set up your USM Anywhere or LevelBlue TDR for Gov domain.
Note: LevelBlue owns the IP ranges listed in the following table. The IP ranges route agent traffic, and connectivity can move within the ranges according to the region.
LevelBlue Agent Installation on a Single Host System
For a Linux host system that is already identified as an asset in your USM Anywhere environment, you can install the agent using a generated bash script to run on that Linux host system. You can generate this script for the specific asset from the Agents page (Data Sources > Agents) or from the Asset Details page for the asset.
Note: If the host system is not in your asset inventory through discovery by a deployed USM Anywhere Sensor, you can manually add the asset using its IP address or fully qualified domain name (FQDN). See Adding Assets for more information.
Alternatively, you can use the script for multiple assets and then use the information provided by the unassociated agent to create a new asset.
Important: Some antivirus software may block the osqueryd service and prevent it from starting. If your service is not starting because of antivirus software, you need to add the /usr/bin/ path to your antivirus exclusions policy.
- In USM Anywhere, go to Data Sources > Agents.
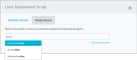
- Click Linux Deployment Script.
- In the dialog box, select the Single Asset tab.
-
Specify the asset where you want to install the agent.
You can start typing the name or IP address of the asset in the field to display matching items and select the one you want.
Or you can click the Browse Assets link to open the Select Asset dialog box and then browse the asset list to make your selection.
-
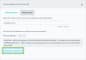
Select the Package Manager type for the Linux distribution.
The deb type is selected by default. If the asset uses a Red Hat distribution, select the rpm type.
-
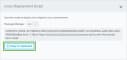
Click Copy to clipboard.
- Use an SSH client to connect and log in to the asset host system.
- Run the copied bash script.
- Go to Environment > Assets.
-
(Optional.) Use the Search & Filters option to filter the list and help you locate the asset you want.
See Searching Assets for more information.
- Click the
icon next to the asset name and then select Full Details.
-
In the Agent Status section, click Deploy Agent.
-
Select the Package Manager type for the Linux distribution.
The deb type is selected by default. If the asset uses a Red Hat distribution, select the rpm type.
-
Click Copy to clipboard.
- Use an SSH client to connect and log in to the asset host system.
- Run the copied bash script.
LevelBlue Agent Installation on Multiple Host Systems
If you have multiple Linux host systems that are not currently in your USM Anywhere asset inventory or you don't want to generate a separate script for each asset, you can install the LevelBlue Agent using a generated bash script on any Linux host system that meets the prerequisite requirements and supports the package type for the script. You can generate this script from the Agents page (Data Sources > Agents).
After you use the script to deploy the agent on your Linux host systems, you can view the list of unassigned agents and then associate each agent with an existing asset or add a new asset using the information provided by the agent.
To generate an agent deployment script for multiple host systems
- In USM Anywhere, go to Data Sources > Agents.
-
Click Linux Deployment Script.
Ensure that the Multiple Assets tab is selected in the dialog box.
-
Select the Package Manager type for the Linux distribution.
The deb type is selected by default. If the asset uses a Red Hat distribution, select the rpm type.
-
Click Copy to clipboard.
-
Run the script on each Linux host system where you want to deploy the agent.
- Use an SSH client to connect and log in to the asset host system.
- Run the copied bash script.
Note: If you use a multiple asset installation script to execute bulk deployment across multiple host systems, the script will not have the unique asset ID. In this case, USM Anywhere attempts to associate the LevelBlue Agent with an existing asset if there is enough information and it can make a definitive match. When a deployed agent does not have an associated asset, you must manually make this association in USM Anywhere to enable queries and log collection for the host system. See LevelBlue Agent and Asset Associations for more information.
Installation Error Resolution
If the LevelBlue Agent is installed using the single asset deployment script, its host identifier UUID and asset association is stored in the osquery.flags file in your system. Asset changes, specifically changes that result in an asset being removed and added back to USM Anywhere, can cause issues with the way the agent associates with the asset if you need to reinstall the agent for any reason.
If you encounter an error during the installation of an agent, you need to remove the osquery directory before you reinstall the agent. To do this, apt-get purge alienvault-agent or yum remove alienvault-agent in the command line, and then reinstall the agent.
Additional LevelBlue Agent Commands
The LevelBlue Agent also comes with a


 Feedback
Feedback