File integrity monitoring (FIM) is a mechanism for validating the integrity of operating system and application software files using a verification method between the current file state and a known, good baseline. It is one of the most powerful techniques used to secure IT infrastructures and business data against a wide variety of both known and unknown threats.
The LevelBlue Agent
LevelBlue offers the lightweight BlueApp Agent as the recommended option for FIM. See the section on The LevelBlue Agent to learn more about the agent.
For systems that don't have the LevelBlue Agent installed, you can manually enable FIM inside the system.
Manual FIM Configuration Options
If you choose not to use the BlueApp Agent for FIM, you can manually configure FIM on your Linux or Windows system.
Manual FIM Configuration for Linux
For Linux systems that do not have the LevelBlue Agent installed, you can enable FIM within USM Anywhere by configuring the osquery agent to monitor and track file changes on those systems. The osquery configuration file (typically named osquery.conf) contains the configuration options and queries that osquery uses when it runs. LevelBlue provides a default configuration file that you can use to enable FIM for Linux systems in your USM Anywhere environment to identify system and software file changes and forward this information to the USM Anywhere Sensor.
For more information about installing and configuring osquery on your Linux systems, see Linux Log Collection with Osquery.
Manual FIM Configuration for Windows
For Windows systems that do not have the LevelBlue Agent installed, you can use FIM to identify changes in system files, folders, and Microsoft Windows registries. To use FIM, you configure Windows systems so that USM Anywhere can view Windows audit object access events. To do so, you need to enable file auditing and update security policy settings. After applying policy changes to include audit object events in Windows security logs, NXLog will forward those events to the USM Anywhere Sensor.
See NXLog CE for Windows Hosts for detailed information about using NXLog to forward these events.
Local Policies determine the security options for a user or service account and are based on the computer and the rights for the account on that computer. These policies can be used to configure an audit policy, which determines which security events will be logged into the Security log on the computer (successful attempts, failed attempts, or both). This Security log is accessible from the Event Viewer.
To define local group policy settings for object access audit events
- On a selected Windows system, open the Local Group Policy Editor.
-
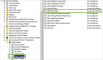
Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy.
- Open the Audit object access policy.
-
In the dialog, select the Success and Failure check boxes to enable auditing.
- Click Apply and then OK.
In order to track file system changes on a Microsoft Active Directory Domain so that USM Anywhere can view Windows audit object access events, first you must set the Windows group policy to keep track of file system changes.
The following example uses the default domain controller policy in order to track changes on a domain controller. Your actual policy might be different, depending on your particular domain configuration.
To audit changes on a domain controller
- From the Server Manager, open up Group Policy Management, and expand the domain to select the policy you want to edit.
- Right-click the policy and choose Edit.
-
Select the Security Options and change the Audit: Force audit policy subcategory settings option to enable it.
This allows the more granular advanced audit policy settings instead of the general categories that are enabled by default.
-
Locate and expand the Advanced Audit Policy Configuration option.
Note: This procedure is primarily concerned with object auditing, but you will need to make sure the other policies, such as account lockout, are correct for your organization. Remember, these advanced policies are now taking precedence.
-
For the Audit File System policy, change the configuration to Success and Failure.
- Verify that the Group Policy you just edited is enforced, and applied to the domain per your particular configuration.
In order for the policy to be effective, you need to enable auditing on the files and directories that you want to monitor. You might be tempted to just enable the entire filesystem, and inherit throughout, and you could do that — however, this will be extremely detrimental to the operation of the server, creating hundreds or thousands of events per minute. You should also consider how often you expect changes to the folders you are auditing because this can be quite noisy.
Note: You can only set up file and folder auditing on NTFS drives.
To apply or modify auditing policy settings
-
Open Windows Explorer and navigate to the file or folder you want to audit.
Note: Because the Windows security log is limited in size and new audit events will be stored there, carefully select the files and folders to be audited. Also, consider the amount of disk space that you want to devote to the security log. The maximum size for the security log is set in Event Viewer.
- Right-click the file or folder and select Properties.
- Select the Security tab and click Advanced.
-
Select the Auditing tab and click Continue if prompted.
This displays the auditing policies for the file or folder.
-
Perform one of the following operations:
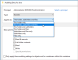
- To set up auditing for a new user or group, click Add. In the Enter the object name to select field, enter the name of the user or group that you want to audit and click OK.
- To remove auditing for an existing group or user, select the group or user name, click Remove, and click OK. You can skip the remaining steps.
- To view or change auditing for an existing group or user, select the name and click Edit.
-
Set the Applies to option to specify the location that you want to audit.
-
In the permissions box, select the actions that you want to audit.
You can click Show advanced permissions to display additional permissions for selection. For FIM enablement, Create, Write, Append, and Delete permissions are key.
- (Optional) If you want to prevent subordinate files and subfolders of the original object from inheriting audit settings, select the Apply these auditing entries to objects and/or containers within this container only option.
- Click OK.
After enabling object access auditing, view the security log in the Windows Event Viewer to see that the audit events are now collected. You can test to make sure the events are properly generated in Windows Event viewer by creating a file, editing it, moving it out of the folder, and then moving it back. This should generate the events in the Event Viewer of a Windows Server similar to the following example.
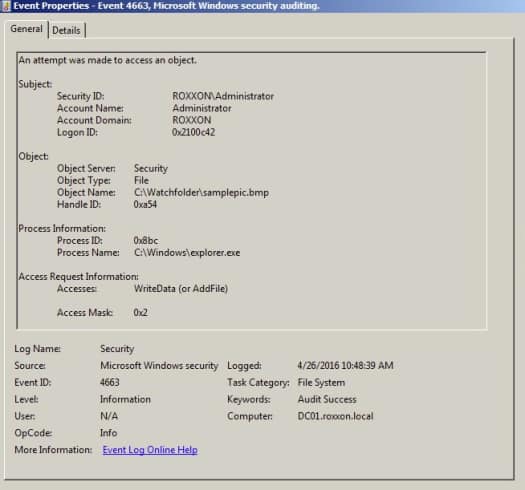
When NXLog is set up to forward these events to the USM Anywhere Sensor, the audit events are available in your USM Anywhere environment.
 Feedback
Feedback