Azure HIPAA compliance
AlienVault USM Anywhere simplifies HIPAA compliance on Microsoft Azure.
Comprehensive HIPAA Compliance Software for Your Azure Cloud Environment
Achieving HIPAA compliance is a major challenge for healthcare organizations, even more so for those organizations that have moved workloads and applications to Azure. HIPAA requirements put rigorous demands on these organizations, who are often have limited IT security resources. Yet, having robust security controls in place is critical to achieve HIPAA compliance.
Running applications and storing sensitive ePHI data in the Azure cloud adds to the complexity of achieving HIPAA compliance. You need a solution that can comprehensively monitor your Azure cloud environment and that simplifies HIPAA compliance across your Azure cloud, on-premises infrastructure, and other cloud or hosted environments.
AlienVault® Unified Security Management™ (USM), with its native Microsoft Azure security monitoring capabilities, is that solution. AlienVault USM delivers multiple essential security capabilities in a unified platform: asset discovery, vulnerability scanning, intrusion detection, behavioral monitoring, incident response, continuous threat intelligence, event correlation, compliance log management, and HIPAA reporting. Combined, these capabilities help you simplify HIPAA compliance within your Azure environment, as well as with your on-premises IT environments.
To meet HIPAA IT compliance requirements, AlienVault USM Anywhere delivers the essential security capabilities you need to monitor your applications and assets hosted in Microsoft Azure, all in one unified solution:
- Asset Discovery. Automated discovery of Azure VMs and other Azure services such as IIS, Azure Web Apps, and more.
- Vulnerability Assessment. Scans your Azure VMs to alert you to any vulnerabilities.
- Threat and Intrusion Detection. Delivers Azure IDS capabilities through direct access to the Azure Monitor API (formerly Azure Insights), and alarm notifications from the Azure Security Center.
- Incident Response. Provides response guidance and the ability to orchestrate responses manually or automatically.
- HIPAA Compliance-ready Log Management and Reporting. Aggregates events and logs from across your cloud and on-premises environments, retaining data for at least one year, and enabling rich insights through customizable reports and views.
Comprehensive Azure Security Monitoring for Effective Threat Detection
The HIPAA Security Rule places onerous stipulations on your organization to safeguard and monitor your infrastructure and applications. The compliance requirements are keenly focused on protecting patients’ electronic Personal Health Information (ePHI) data. For healthcare organizations trying to maintain HIPAA Compliance, that security challenge is compounded as you move infrastructure and workloads to the Azure cloud.
Comprehensive monitoring of your Azure cloud environment is fundamental to complying with HIPAA, yet traditional HIPAA compliance software was designed for on-premises and does not extend easily, if at all, to cloud environments. The ideal security tool must be purpose-built for the Azure cloud to take advantage of the APIs that Azure provides. It should also be able to monitor your on-premises environment to provide full visibility across your hybrid IT environment. To enable full compliance with HIPAA requirements, you need a complete solution that monitors your Azure environment as well as your on-premises environment.
USM Anywhere, with its purpose-built Azure sensor, delivers comprehensive security monitoring for your Azure cloud as well as your on-premises environments to support your HIPAA compliance efforts. Through a unified platform, USM Anywhere delivers these critical capabilities:
- Natively-built sensor supports deep monitoring of your assets and data hosted on Microsoft Azure.
- Integrated monitoring of user and administrator activities and actions within your Azure subscription(s), enabling identification of anomalous behavior.
- Automated discovery of Azure VMs, including installed software packages, running processes, and services.
- Vulnerability assessment scans of your Azure VMs let you know where exploitable risks exist, and with information on available patches.
- Direct access to the Azure Monitor API and Azure Security Center alerts deliver intrusion detection on Azure.
- Incident response guidance, helping accelerate your response so that you don’t have to do the research yourself.

HIPAA Compliance-Ready Azure Log Management & Retention
Log Management is a critical component of Azure HIPAA Compliance and simplifies satisfying multiple HIPAA requirements such as information system activity review (HIPAA requirement §164.308(a)(1)(ii)(D)), monitoring logon attempts (HIPAA requirement §164.308(a)(5)(ii)(C)), and more.
Logging events from your Azure environment is a bit different than on-premises log management, as there are various storage and compute (Azure VM) instances you must keep track of. Microsoft provides some native tools to capture events, such as Azure Monitor (formerly Azure Insights), and the ability to log events within Azure Storage instances, but these only support ad-hoc requests through PowerShell cmdlets or through a programmatic approach.
But capturing the logs is just one part of the process. You also need a tool that captures, parses, and analyzes the logs together to identify threats and help you respond to malicious activity in your Azure environment—all in an integrated solution.
AlienVault USM delivers these comprehensive Azure log management and log retention capabilities to help you achieve HIPAA compliance of your Azure environment.
- Automated collection and aggregation of events relating to activities across the Azure platform and services, as well as events from applications hosted with Azure VMs.
- Ability to collect events detailing user and administrator access and activities on your Azure subscription(s)=, helping identify trends and highlight anomalous behaviors.
- Events are normalized and enriched, enabling detection of threats and intrusions with USM Anywhere’s advanced correlation capabilities, and simplifying search across events from data sources.
- Compliance-ready log retention, storing events and logs for at least 12 months, with the option to extend to longer periods.
- Granular visibility into raw logs, combined with rich search and filtering capabilities, simplifies forensic analysis, making HIPAA compliance a much easier process.
- Attested as HIPAA Compliant, so you can be assured that AlienVault has the proper security controls in place to securely process, handle, and store your log data in the AlienVault Secure Cloud, in accordance with HIPAA compliance requirements.
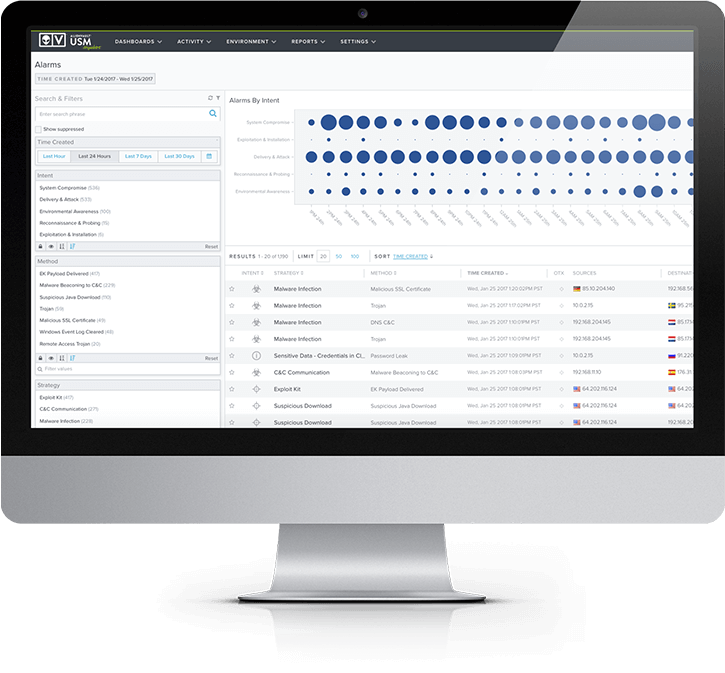
Simplify and Reduce the Cost of HIPAA Compliance on Azure
The number of different point HIPAA compliance tools required to meet the many HIPAA requirements can be daunting. It can be expensive to procure all of them, and the additional cost to deploy, integrate, and perform daily management of each HIPAA compliance tool can be challenging to resource-constrained IT security teams.
It is also worth noting that many traditional IT security tools were designed for on-premises environments, and perform poorly, at best, at successfully monitoring cloud environments like Microsoft Azure. This results is having to use native Azure tools, like the Azure Compliance Center, to monitor your Azure environment. However, these tools often carry additional costs and rarely provide sufficient coverage to deliver the coverage you need to comply with all your HIPAA requirements.
The security problem every organization has is that new threats arise every day. It is impossible for most organizations to keep up, particularly those healthcare organizations who have adopted a hybrid environment that encompasses cloud and on-premises infrastructure. Security and compliance within your Azure cloud environment is not truly possible without a solution designed for that environment, and ideally one that is able to provide security and compliance capabilities for all your environments.
AlienVault USM dramatically simplifies your efforts to satisfy the HIPAA Security Rule on your assets and data deployed to Microsoft Azure, and can reduce costs compared to deploying multiple point solutions to comply with multiple HIPAA requirements on Azure.
- Out-of-the-box and customizable compliance and security reports, as well as customizable data views on alarms and events, simplify your ability to perform day-to-day review and meet requests from management and compliance auditors
- Multiple security essentials – asset discovery, vulnerability assessment, threat detection, incident response, log management and reporting, and threat intelligence – in one unified solution, enables you to satisfy multiple HIPAA requirements relating to the HIPAA Security Rule
- Integrated monitoring of your Microsoft Azure subscriptions as well as your on-premises, hosted, and other public cloud environments, delivers a single view for HIPAA compliance across all environments where your healthcare assets reside
- Continuously updated threat intelligence from AlienVault Labs Security Research Team, as well as from the AlienVault Open Threat Exchange® (OTX™), delivers the latest correlation rules, vulnerability signatures, response guidance, and more, so you don’t have to do the research yourself
- Ability to monitor user and administrator activity in cloud applications, including Office 365 and G Suite, as well as authentication to other applications performed through Azure Active Directory or Okta, help you to meet the HIPAA requirement for logon monitoring
Discover How AlienVault USM Supports
HIPAA Requirements
HIPAA Standard
HIPAA Requirement
Examples of How AlienVault USM Helps
§164.308(a)(1) - Security Management Process
Implement policies and procedures to prevent, detect, contain, and correct security violations.
§164.308(a)(1)(ii)(A) - Risk Analysis
§164.308(a)(1)(ii)(D) - Information System Activity Review
- Built-in asset discovery discovers assets running on-premises, and in cloud environments (including Azure, VMware, Hyper-V, AWS).
- Identifies systems susceptible to known vulnerabilities, and ranks them as 'high', 'medium' and 'low' risk to aid prioritization.
- Identifies patches or workarounds available to vulnerable systems.
- Identifies where security tools, such as antivirus and firewalls, have been disabled or have failed to start.
- Monitors access to and attempt to modify system and application binaries, configuration files, log files.
- Monitors user and administrator activities in cloud environments such as Azure and AWS, and within cloud applications such as Office 365.
- Continuously updated threat intelligence ensures that USM is operating with the latest correlation directives, vulnerability signatures, IDS rules, reports, guided threat response and more.
- Aggregates, analyzes and archives logs and events from systems, applications and devices from across your on-premises and cloud environments.
- Identifies logon success and failures.
- Identifies privilege escalation attempts.
- Identifies unauthorized attempts to access or modify key logs.
§164.308(a)(3) - Workforce Security
Implement policies and procedures to ensure that all members of its workforce have appropriate access to electronic protected health information ..., and to prevent those workforce members who do not have access ... from obtaining access to electronic protected health information.
§164.308(a)(3)(ii)(A) - Authorization and/or Supervision
§164.308(a)(3)(ii)(C) - Termination Procedures
- Monitor access attempts to critical files and data, and alarm when unauthorized attempts are detected.
- Capture and monitor all login successes and failures to critical assets, particularly those containing electronic protected health information.
- Monitor for logon or access attempts from the accounts of users who have been de-provisioned.
§164.308(a)(4) - Information Access Management
Implement policies and procedures to prevent, detect, contain, and correct security violations.
§164.308(a)(4)(ii)(C) - Access Establishment and Modification
- Captures all user account creation and modification activities.
- Identifies logon success and failures.
- Identifies privilege escalation attempts.
§164.308(a)(5) - Security Awareness and Training
Procedures for monitoring log-in attempts and reporting discrepancies
§164.308(a)(5)(ii)(A) - Security Reminders
§164.308(a)(5)(ii)(B) - Protection from Malicious Software
§164.308(a)(5)(ii)(C) - Log-in Monitoring
§164.308(a)(5)(ii)(D) - Password Management
- Provision for automated updates of USM infrastructure whenever updates are made available.
- Continuously updated threat intelligence ensures that USM is operating with the latest correlation directives, vulnerability signatures, IDS rules, reports, guided threat response and more.
- Identifies systems susceptible to known vulnerabilities, or that may not have antivirus installed and/or operational.
- Identifies indicators of malware-based compromise, and enables orchestrated responses that can be automated or manually invoked to isolate infected systems and block malicious domains.
- Monitors and stores events from antivirus solutions that could indicate a compromise, or attempt to disable antivirus software.
- Monitors for changes to Office 365 policies including Information Management, and more.
- Continuously updated threat intelligence ensures that USM is operating with the latest correlation directives, vulnerability signatures, IDS rules, reports, guided threat response and more.
- Captures and enables monitoring of logon success and failures to systems, security devices, cloud environments, and more.
- Identifies where new user and administrator accounts are created and deleted.
- Monitors public and dark web sources for the trade or communication of stolen credentials.
- Identifies use of default system accounts on Windows machines.
- File Integrity Monitoring can detect changes and access to critical system and application files, and Windows Registry entries.
§1164.308(a)(6) - Security Incident Procedures
Implement policies and procedures to prevent, detect, contain, and correct security violations.
§164.308(a)(6)(ii) - Response and Reporting
- Correlates events to detects threats
- Generates alarms on threats, classifying them across a kill-chain taxonomy to inform the risk level of that threat.
- Enables threat investigation and provides context to determine the nature of the threat.
- Provides recommended incident response guidance to contain or remediate the threat.
- Enables labels to be applied to alarms.
- Security orchestration and response capabilities enable manual or automated incident response, driving actions with leading security and IT operations tools including Cisco Umbrella, Carbon Black, Palo Alto Firewalls, and more.
- Enables creation of incident tickets within popular solutions like ServiceNow, directly from within the USM Anywhere console.
- Continuously updated threat intelligence ensures that USM is operating with the latest correlation directives, vulnerability signatures, IDS rules, reports, guided threat response and more.
§164.308(a)(7) - Contingency Plan
Establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information.
§164.308(a)(7)(ii)(E) - Applications and Data Criticality Analysis
- USM Anywhere provides a fault resilient architecture that assures durability of all captured event and log data from your environments.
§164.312(a) - Access Control
Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights.
§164.312(a)(2)(iii) - Automated Logoff
§164.312(a)(2)(iv) - Encryption and Decryption
- Monitors for changes to Windows Group Policy and Office 365 policies that define automated logoff, session timeout, and access token timeout parameters.
- Monitors for changes to Windows Registry or application configuration files that define encryption settings for protected health information.
§164.312(b) - Audit Controls
Implement hardware, software, and/or procedural mechanisms that record and examine activity in information systems that contain or use electronic protected health information.
- Monitors for changes to Office 365 policies including Data Leakage Protection (DLP), information management, and more.
- File Integrity Monitoring can detect modification attempts to applications or online storage containing electronic protected health information.
- Unified log collection, review and analysis, with triggered alarms for high risk systems.
§164.312(c)(1) - Integrity
Implement policies and procedures to protect electronic protected health information from improper alteration or destruction.
§164.312(c)(2) - Audit Controls
- Monitors for changes to Office 365 policies including Data Leakage Protection (DLP), information management, and more.
- File Integrity Monitoring can detect modification attempts to applications or online storage containing electronic protected health information.
§164.312(e)(1) - Transmission Security
Implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network.
§164.312(e)(2)(i) - Integrity Controls
§164.312(e)(2)(ii) - Encryption
- Discover unauthorized communications, such as between untrusted networks and systems within the cardholder data environment.
- Monitors for changes to Office 365 policies including Data Leakage Protection (DLP), information management, and more.
- File Integrity Monitoring can detect modification attempts to applications or online storage containing electronic protected health information.
- Monitors for changes to Windows Group Policy and Office 365 policies that define automated logoff, session timeout, and access token timeout parameters.
- Monitors for changes to Windows Registry or application configuration files that define encryption settings for protected health information.





