| Applies to Product: |
|
|
When performing scans, you must select a scanning profile. Using a set of network vulnerability tests (NVTs) organized by families, each profile determines the type of scan to perform and how thorough the scan should be.
In USM Appliance, go to Environment > Vulnerabilities > Overview and then click Profiles to see the list of scan profiles. You can't view, modify, or delete the built-in scan profiles, but you can create new profiles by cloning the existing ones. You can view the cloned profiles and see what plugins are included in each profile. You can modify or delete any profile you created.
Starting from version 5.8.7, USM Appliance provides the following scan profiles for you to choose from:
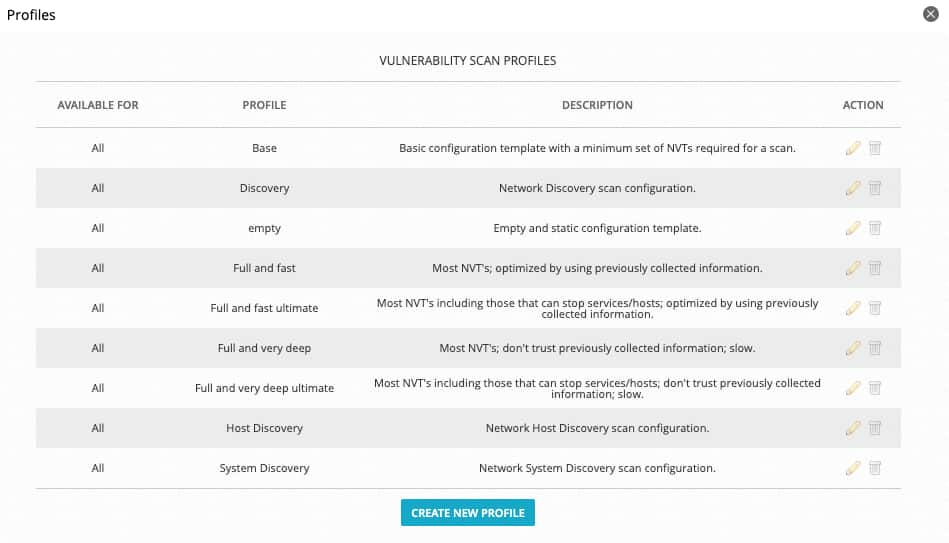
| Profile Name | Description |
|---|---|
| Base |
This scan profile contains NVTs that collect information about the target systems. It uses Ping and Nmap to detect if a host is alive and collects information about the operating system (OS). It doesn't detect vulnerabilities. The NVT families are static. After the profile is created, the set of NVTs stays the same. |
| Discovery |
This scan profile contains NVTs that provide information about the target systems. It collects information about open ports, used hardware, firewalls, installed software and certificates, and used services. It doesn't detect vulnerabilities. The NVT families are dynamic. After the profile is created, new NVTs in the selected NVT families are added and used automatically. |
| Empty | This scan profile contains no NVT. You can clone it and create a scan profile from scratch. |
| Full and fast |
This scan profile contains NVTs that won't damage the target systems. It conducts a port scan to gather information about the system first and use the relevant NVTs based on the information collected to complete the scan. These NVTs are optimized to keep the false negative rate low. The NVT families are dynamic. After the profile is created, new NVTs in the selected NVT families are added and used automatically. |
| Full and fast ultimate |
This scan profile expands the Full and fast profile with NVTs that could disrupt services or systems, or even cause shutdowns. It conducts a port scan to gather information about the system first and use the relevant NVTs based on the information collected to complete the scan. These NVTs are optimized to keep the false negative rate low. The NVT families are dynamic. After the profile is created, new NVTs in the selected NVT families are added and used automatically. |
| Full and very deep |
This scan profile is based on the Full and fast profile but without taking into account the result of the port scan. In other words, it includes NVTs that wait for a timeout and NVTs that test vulnerabilities of an application that wasn't detected, making the scan very slow. The NVT families are dynamic. After the profile is created, new NVTs in the selected NVT families are added and used automatically. |
| Full and very deep ultimate |
This scan profile expands the Full and very deep profile with NVTs that could disrupt services or systems, or even cause shutdowns. The scan is very slow. The NVT families are dynamic. After the profile is created, new NVTs in the selected NVT families are added and used automatically. |
| Aggressive |
This scan profile runs all vulnerability-related scripts regardless of whether they are safe for the scanned target. This can cause a significant performance drop as well as issues such as Denial of Service (DoS), malfunctions, and errors. |
| Host discovery |
This scan profile contains NVTs that use Ping to detect if a host is alive. It doesn't detect vulnerabilities. The NVT families are static. After the profile is created, the set of NVTs stays the same. |
| System discovery |
This scan profile contains NVTs that use Ping to detect if a host is alive and Nmap to collect information about the OS and hardware. It doesn't detect vulnerabilities. The NVT families are static. After the profile is created, the set of NVTs stays the same. |
Note: USM Appliance version 5.8.6 and earlier only has three scan profiles:
- Deep: A non-destructive full and slow scan.
- Default: A non-destructive full and fast scan. Use this profile if the target system tends to break or crash with the scanning requests.
- Ultimate: A full and fast scan including destructive tests. It includes stress tests that can crash the target system. For example, filling a network switch with random MAC addresses.
 Feedback
Feedback