| Applies to Product: |
|
|
You can create actions for USM Appliance to perform on security events. This includes sending an email, executing a script, or opening a ticket. One example of an action could be "When an attack against IP 192.168.1.1 occurs, send an email to an external ticketing system."
To configure an action
- Go to Configure > Threat Intelligence > Actions, select New.
- Type the name of the action in the Name field.
- From the Context list, select the context under which the action should occur.
-
In the Description field, click on any applicable keywords at the top of the page to automatically add them to the field.
For example, if you wanted to create an action to send an email to an administrator, you could include information from the normalized event in the email message, such as SRC_IP, DST_IP, PRIORITY, and RISK.
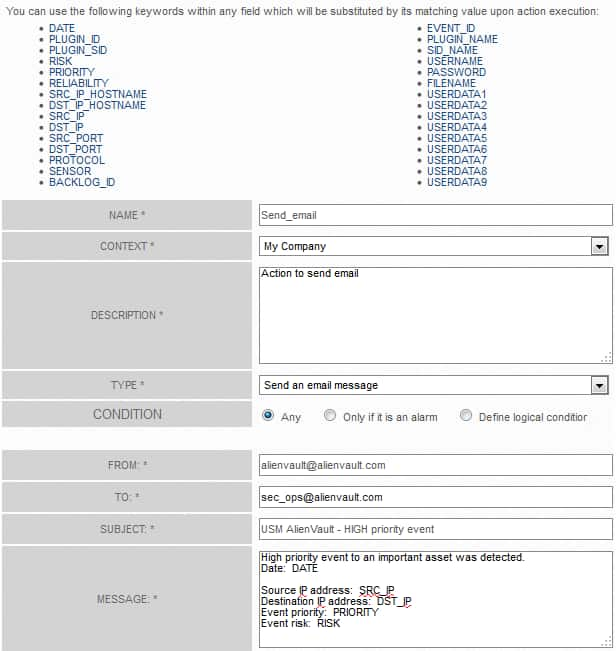
When the action is executed, USM Appliance substitutes the values from the event that triggered the action for the keywords.
Note: You can also use keywords when you want to execute an external program. One example might be an event that invokes a script that sends a shun command to a network firewall to prevent an attacker from making a connection through the firewall at the DST_IP address.
- From the Type list, select an action option.
- Send an email message about an event to a preconfigured email within your organization.
- Execute an external program by means of a script.
- Open a ticket in USM Appliance's internal ticketing system.
- In Conditions, indicate under what circumstances the action should occur:
- If you choose Any or Only if it is an alarm, no new fields display.
-
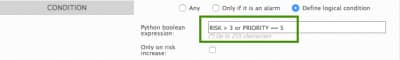
If you choose Define logical condition, two new UI fields display:
Python Boolean expression — True or False expressions in Python.
Only on risk increase check box — When checked, this condition must be met for this policy consequence to go into effect.
You can use Boolean comparison operators (==, !=, >, <, >=, <=) and logical operators (AND, OR, NOT) in combination with the provided keywords, such as "Date", "Risk", "Plugin_SID", to define conditions for an action to trigger. For example
Important: When writing an expression, only the following characters are allowed: A-Z, a-z, 0-9, _, ', and ".
Note: Starting from version 5.6, you can also use arithmetic operators, add (+), subtract (-), multiply (*), and divide (/), in an expression.
- Fill in the fields that appeared after you selected the action type:
- In the FROM field, type the email address from which the email message is being sent. This is frequently the USM Appliance administrator.
- In the TO field, type the email address or addresses to which USM Appliance should send the message.
- In the Subject field, type a subject for the email. For example, this may reflect the policy's purpose, such as "Escalation of event risk on critical asset."
- In the Message field, type the content for the email. You can also use the keywords used earlier in the description field.
- Click Save.
Options include:
You can also use this option to send notifications by phone messaging services, such as Short Message Service (SMS). However, to do this, you need an external messaging gateway capable of translating email messages to phone messages.
The Actions page expands to include more fields specific to the selection you made.
To send an email message:
For a detailed example, see Tutorial: Create a Policy to Send Emails Triggered by Events.
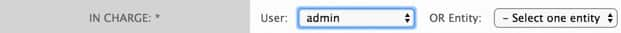
To open a ticket in USM Appliance:
In the In Charge field, select either a particular User or an Entity.
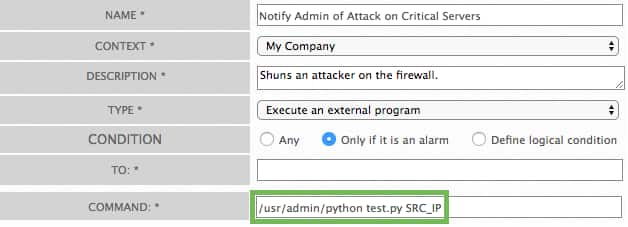
To execute an external program, using a script residing locally:
Type the path to the script in the Command field. Once the policy conditions have been met, the program or script will then run.
Important: The best practice is to use non-blocking scripts, as blocking scripts may create response issues or other undesired effects if there is any delay in the script's completion, including the possibility of breaking backup and purging processes.
 Feedback
Feedback