| Applies to Product: |
|
|
In this process we will configure an HIDS Agent, installed on a Windows system, to read logs from a file. This can be useful when we try to grab data from an application that logs directly into a file. For this purpose we have created a sample file C:\Users\WIN7PRO\Desktop\Test.txt with the following log line:
"myapplication: This is a test."
Task 1. Configure HIDS Agent to read a file on Windows
- Edit C:\Program Files (x86)\ossec-agent\ossec.conf.
- Add the following settings inside the <localfile> element of the ossec.conf file:
- Restart the ossec-agent service.
<localfile>
<location>C:\Users/WIN7PRO/Desktop/Test.txt</location>
<log_format>syslog</log_format>
</localfile>
Task 2. Enable "logall" on USM Appliance
Note: This task is only required for the initial configuration.
- In the USM Appliance web UI, go to Environment > Detection > HIDS > Config > Configuration.
-
Add <logall>yes</logall> to the <global> section of the file:
Adding this setting allows logging of all events to /var/ossec/logs/archives/archives.log.
- Click Save at the bottom of the screen.
-
Restart the HIDS Service:
- Go to Environment > Detection > HIDS > HIDS Control.
- Click Restart.
Task 3. Confirm that USM Appliance receives the log line
- Write a new log line in the Test.txt file and save, e.g. "myapplication: This is a test 2."
- On USM Appliance, check for the newly added line in /var/ossec/logs/archives/archives.log.
You can check for log line by running the following command:
cat /var/ossec/logs/archives/archives.log | grep -i "myapplication"
You should see an output similar to the following:
cat /var/ossec/logs/archives/archives.log | grep -i "myapplication"
2015 Jun 16 06:20:30 (TEST) 192.168.1.20->\Users/WIN7PRO/Desktop/Test.txt myapplication: This is a test 2
Task 4. Create a new decoder on USM Appliance to parse the incoming log lines
-
On USM Appliance edit /var/ossec/alienvault/decoders/local_decoder.xml (same as decoder.xml but this one is not overwritten when updating the system).
If this file does not exist you can create it with the following command:
touch /var/ossec/alienvault/decoders/local_decoder.xml
-
In local_decoder.xml add a new decoder to parse first part of the log message and save your changes:
<decoder name="myapplication">
<prematch>^myapplication: </prematch>
</decoder>
- In the USM Appliance web UI, go to Environment > Detection > HIDS > Config > Configuration.
-
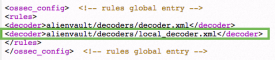
Add <decoder>alienvault/decoders/local_decoder.xml</decoder> right after <decoder>:
Adding this setting enables the usage of a custom decoder.
- Click Save at the bottom of the screen.
- Restart the HIDS service as detailed in Task 2 Step 4.
- Run /var/ossec/bin/ossec-logtest and paste the log line "myapplication: This is a test."
-
Check if it recognizes the decoder.
If it works you will see the newly created decoder listed.
Task 5. Create a new rule on USM Appliance to parse lines processed by the decoder
Important: Use a number between 190,000 and 199,999 as the rule id.
- On USM Appliance edit /var/ossec/alienvault/rules/local_rules.xml.
-
Add the following lines to the file:
<group name="myapplication">
<rule id="196000" level="0">
<decoded_as>myapplication</decoded_as>
<description>myapplication is enabled</description>
</rule>
<rule id="196001" level="1">
<if_sid>196000</if_sid>
<match>Test</match>
<description>Test string found</description>
</rule>
</group>
- Restart the HIDS service as detailed in Task 2 Step 4.
- Run /var/ossec/bin/ossec-logtest and paste a log line (in this case "myapplication: This is another Test").
-
Check if it recognizes the rule:
You will see Phase 3 of the Log Test has completed and matched our new rule:
Task 6. Create and configure local version of the ossec-single-line plugin
-
Create a .local version of the ossec-single-line plugin (if it does not already exist) and ensure it has the correct owner, group and permissions:
touch /etc/ossim/agent/plugins/ossec-single-line.cfg.local
chown root:alienvault /etc/ossim/agent/plugins/ossec-single-line.cfg.local
chmod 644 /etc/ossim/agent/plugins/ossec-single-line.cfg.local
-
Insert or add the following translation to the ossec-single-line.cfg.local file:
[translation]
196001=7999
-
Insert a new plugin_sid with value "196001" for the ossec-single-line plugin. This can be done using the following command:
echo 'INSERT IGNORE INTO plugin_sid(plugin_id, sid, category_id, class_id, reliability, priority, name) VALUES(7999, 196001, NULL, NULL, 1, 2, "ossec: my_application_test_rulematch");' | ossim-db
-
Run the command below to ensure the new configuration takes effect :
alienvault-reconfig
Task 7. Test your configuration
-
Generate new logs and check /var/ossec/logs/alerts/alert.log while the logs are being written to the file:
tailf /var/ossec/logs/alerts/alerts.log | grep myapplication
You should see an output similar to the following, which confirms correct operation:
tailf /var/ossec/logs/alerts/alerts.log | grep myapplication
AV - Alert - "1434530803" --> RID: "196001"; RL: "1"; RG: "ourapplication"; RC: "Test string found"; USER: "None"; SRCIP: "None"; HOSTNAME: "(TEST) 192.168.1.20->\Users/WIN7PRO/Desktop/Test.txt"; LOCATION: "(TEST) 192.168.1.20->\Users/WIN7PRO/Desktop/Test.txt"; EVENT: "[INIT]myapplication: This is a test log[END]";
AV - Alert - "1434530829" --> RID: "196001"; RL: "1"; RG: "ourapplication"; RC: "Test string found"; USER: "None"; SRCIP: "None"; HOSTNAME: "(TEST) 192.168.1.20->\Users/WIN7PRO/Desktop/Test.txt"; LOCATION: "(TEST) 192.168.1.20->\Users/WIN7PRO/Desktop/Test.txt"; EVENT: "[INIT]myapplication: This is another test log[END]";
-
(Alternatively) Generate new logs and look in theUSM Appliance web UI for results:
- Go to Analysis > Security Events (SIEM).
- Under Datasource, select "AlienVault HIDS".
- Click Grouped to view the events in groups.
You should see the newly created events with the event name: AlienVault HIDS: my_application_test_rulematch.
Task 8. Disable "logall"
Repeat all actions taken in Task 2. Enable "logall" on USM Appliance, but this time delete the line "<logall>yes</logall>" from ossec.conf. This is to prevent the archives.log file from growing too large.
Task 9. (Optional) Enable File Integrity Monitoring (FIM)
For details on how to configure FIM, see File Integrity Monitoring.
AlienVault OSSIM Limitations: Both LevelBlue OSSIM and the USM Appliance HIDS decoders are fully featured, with all of their information coming from the Plugin Feed Updates that USM Appliance and LevelBlue OSSIM provide. However, LevelBlue OSSIM lacks the depth of NIDS information that is provided to USM Appliance through the Threat Intelligence Updates.


 Feedback
Feedback