| Applies to Product: |
|
|
The Security Events (SIEM) page, under Analysis > Security Events (SIEM), consists of two views: SIEM View and Real-Time View. You can also create your own Custom Views with specific search criteria and column selections.
SIEM View
This view offers search and robust filtering categories for isolating types of events to review.
From the tabular summary listing of events, you can click on a specific event row to view further details about that event in a popup window. You can also click the More Details (![]() ) icon in an event row to display event details on a new page, which also lets you choose further actions to take with the current event. For field references, see Review Event Details
) icon in an event row to display event details on a new page, which also lets you choose further actions to take with the current event. For field references, see Review Event Details
Enter the keyword of the event and click GO to start the search. By default, USM Appliance searches the Event Name, but you can change it by using the drop-down menu. Other field include
- Event ID
- Payload
- IDM Username
- IDM Hostname
- IDM Domain
- Src or Dst IP
- Src IP
- Dst IP
- Src or Dst Host
- Src Host
- Dst Host
You can use logical operators such as AND, OR, or ! (negation) to form a complex search. For Advanced Search options, see Define Advanced Search Criteria for Security Events (SIEM).
Using the filtering categories at the top of the Security Events (SIEM) page, you can search for specific events. For example,
- Events having the same host as the traffic that triggered an alarm.
- Events coming through the same sensor.
- Events based on OTX pulses or on OTX IP Reputation.
When you use multiple filters, USM Appliance sees the relationship between them as AND. Although you can make a selection from multiple filter groups to search on, you cannot select multiples from the same filter group. You can clear any or all existing filters at far-right.
| Filter Name | Description |
|---|---|
| Show Events | Date oriented filters, including a range filter, so that you can search events occurring within a specific time period. |
| Userdata list |
Allows you to select from userdata1~userdata9, filename, username, or password to create a search criterion. Select the operator you want to use and enter the keyword in the field. |
| Data Sources | External applications whose data are collected and evaluated by a plugin, and translated into an event within the USM Appliance taxonomy. |
| Data Source Groups | A predefined list of usually related data sources, such as directive events. |
|
Sensors |
USM Appliance Sensor that captured the event. Select "Exclude" if you want to exclude events from this sensor instead. |
| Asset Groups |
List of predefined asset groups. |
| Network Groups |
List of predefined network groups. |
| Risk |
Risk level of the event, which can be Low (0), Medium (1), or High (>= 2). Risk calculation is based on the formula: Asset Value * Event Reliability * Event Priority / 25 = Risk. if Asset Value = 3, Reliability = 2 and Priority = 2, the risk would be 3 * 2 * 2 / 25 = 0.48 (rounded down to 0). Risk is Low. |
| OTX IP Reputation |
Clicking the list icon expands the list to show a set of IP Reputation filters. These let you see all events with IP Reputation data or, alternatively, only events with IP Reputation data of a specified severity level, or type of malicious activity. IP Reputation ranks severity based on the number of reports existing about an IP address, as well as the nature of the threat the IP poses. |
| OTX Pulse |
Double-clicking this field expands a list of pulse names, from which you then select a pulse to review as an event. If you know the pulse name, you can type it within the field. This quickly displays the pulse from the list. |
| Only OTX Pulse Activity |
Shows all events within your environment resulting solely from OTX pulse indicators. Note: You cannot filter on events with IP Reputation data and OTX pulses simultaneously. |
The events themselves appear in a list in the second half of the view.
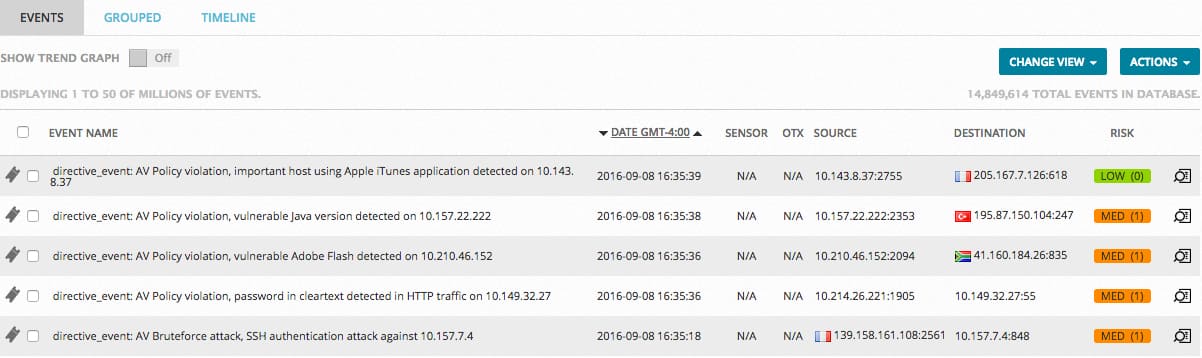
| Column Name | Description |
|---|---|
| Event Name |
Name of the event. |
| Date | Date and time registered by USM Appliance for the event. Date and time are user configured. |
| Sensor |
Name of USM Appliance Sensor detecting the event. |
| OTX |
|
| Source | Hostname or IP address of the host, with national flag if country is known, that initiates the event. |
| Destination | Hostname or IP address of the host, with national flag if country is known, that receives the event. |
| Risk |
Risk level of the event, which can be Low (0), Medium (1), or High (>= 2). Risk calculation is based on the formula: Asset Value * Event Reliability * Event Priority / 25 = Risk. if Asset Value = 3, Reliability = 2 and Priority = 2, the risk would be 3 * 2 * 2 / 25 = 0.48 (rounded down to 0). Risk is Low. |
| Magnifying glass icon ( |
Clicking the magnifying glass takes you to the Event Details. (See Review Event Details.) Note: You can go to Event Details by clicking anywhere within the event, with the exception of the OTX icon. |
In addition to other navigation options, in both Alarm and SIEM Event list views, you can right-click on Source and Destination IP addresses or host names, which will display a popup menu of available actions you can take corresponding to a specific IP address or host name.
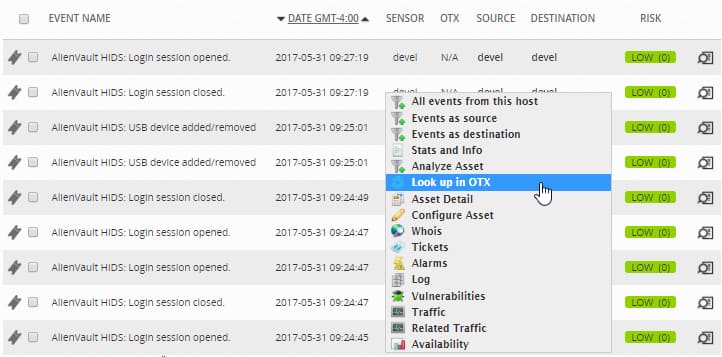
For example, the Look up in OTX option opens the OTX site to display potential and reported threats related to the selected location. If no threat information is found about the location, the Look Up in OTX option opens the Create New Pulse web page in OTX, which lets you create a new Pulse to report a possible new threat.
Real-Time View
The Real-Time view shows you an up-to-the-minute snapshot of all events occurring within your system.
This view may or may not contain any OTX data, depending on what events are currently transpiring in your system.
Real-Time view displays the Events list at the top of the page. The Events list in Real-Time view displays many of the same categories of information as SIEM view, but with some differences, and also unique information.
Filters correspond to the hosts displayed.
To expand a filter list
-
Left-click or start typing inside of the field.
This expands a list of filters for you to select from:
If you already know the individual filter
- Type the filter identifier into the field.
- If USM Appliance finds real-time events for the filter you select, they display in the Events list.
- If USM Appliance does not find real-time events for that filter, the Events list appears empty.
-
Click the Show Plugin filter.
A list of all supported system plugins displays at the bottom of the page. Not all of these are necessarily installed on your system. You must verify which plugins match your USM Appliance deployment.
The display jumps to that entry in the list.
To filter on plug-ins
Custom Views
When examining the Events list, USM Appliance allows you to edit the default views or create custom views with your specific search criteri and column selections.
To create a custom view for events
- Go to Analysis > Security Events (SIEM) and perform a search to include the events you want to see.
-
Click Change View to select a predefined view.
Predefined views include Default, Taxonomy, Reputation, Detail, Risk Analysis, and IDM. Each view displays the same events but with different columns.
-
Alternatively, click Change View and then select Create New View.
- In Create New Custom View, select the columns you want to see in this view.
- To apply the same query every time when you launch this view, select Include custom search criteria in this predefined view.
- Type a name for the view, and then click Create.
USM Appliance saves your changes and refreshes the page to display the view.
To delete a custom view for events
- On Analysis > Security Events (SIEM), click Change View to select the view you want to delete.
- Click Change View again and select Edit Current View.
- In Edit Current View, click Delete at the bottom.
-
Confirm the action when prompted.
USM Appliance deletes the corresponding view and refreshes the page to display the Default view.
AlienVault OSSIM Limitations: The USM Appliance SIEM engine has more diverse capabilities in handling events due to its built-in correlation abilities and graph-based analytics.

 Feedback
Feedback