| Applies to Product: |
|
|
The correlation engine uses cross-correlation rules to connect NIDS events and vulnerabilities discovered by the LevelBlue Vulnerability Scanner.
LevelBlue USM Appliance provides a web interface, Configuration > Threat Intelligence > Cross Correlation for you to examine, modify, and create cross-correlation rules.
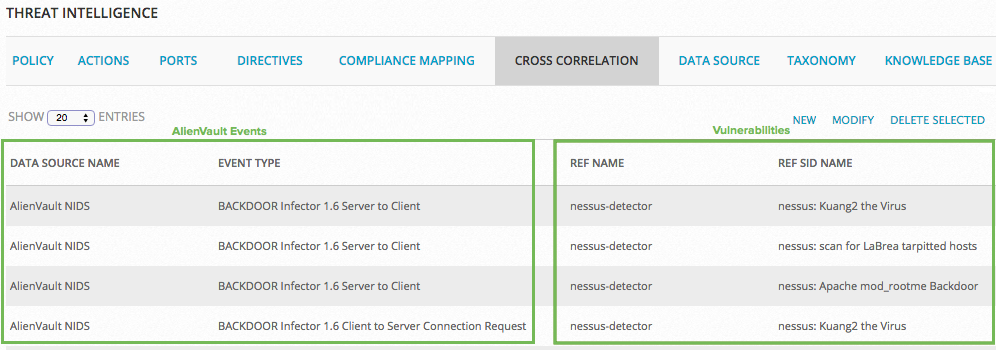
At the bottom of the page, you can navigate to the next pages to see more rules. You can also use the search icon to display the search box, and then search by Data Source Name, Event Type, Ref Name, and Ref SID Name.
To view a cross-correlation rule, do one of the following
- Double-click the rule.
- Highlight the rule and click Modify.
For example, the following cross-correlation rule ties an LevelBlue NIDS A USM Appliance feature and data source for intrusion detection that monitors network traffic and detects malicious events. In conjunction with event correlation, it enhances the threat detection capabilities of USM Appliance. login failed event (for the "sa" account on a Microsoft SQL Server), to when the account has a blank password. The correlated event created in this case would indicate that someone tries to log in to the system using a password, while the system itself has been configured without a password.

 Feedback
Feedback