| Applies to Product: |
|
|
A correlation rule defines a condition to match incoming events. Refer to How Does Correlation Work? for details. The table below summarizes the attributes used in the rules.
By default, USM Appliance only displays the attributes up to Event Type. To see the additional attributes, click the More button. The majority of the built-in directives do not use these attributes.

Note: To examine which event the SID represents, click the data source name, and then search for the SID in the resulting page. The SID does not respond even though it appears like a link.
To change which attributes to display
-
Click the […] next to the Event Type column.
The Customize Columns window opens.
-
Select which attributes you want display in a rule.
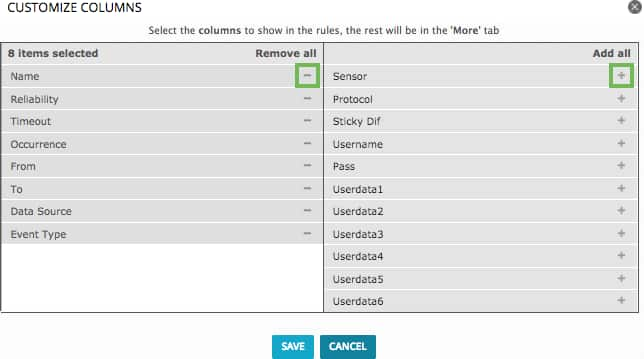
- Click Save.
Indentation of Rules
When a correlation directive contains multiple rules, the indentation of the rules reveals the relationship between the rules. Indented rules have an AND relationship while parallel rules have an OR relationship.
For example, the screenshot below shows one of the built-in directives, AV Network attack, too many dropped inbound packets from DST_IP, which detects network attacks by observing dropped packets from any source IP address to a specific destination IP address on the Cisco PIX firewall. This directive has three correlation levels (denoted by the black triangles) and four rules (all named Firewall dropped packets).

The first rule is matched when the cisco-pix plugin identifies a "PIX:Deny inbound (No xlate) string" (SID 106011) event. AND, if the second rule also matches, 3 more such events occur within 10 seconds toward the same destination, the reliability of the directive event increases to 4. AND, if the third rule also matches, 5 more such events occur within 20 seconds toward the same destination, the reliability increases to 6. OR, if the last rule matches, 10 more such events occurred within 30 seconds toward the same destination, the reliability of the directive event increases to 8.
Using Negation and Commas
You can use negation (inserting an exclamation point before an item) to exclude items in a rule. Commas can be used to separate items when creating lists. Specific considerations must be made when using commas and exclamation points together in lists. When using commas to separate multiple elements in a list, the list must consist of exclusively non-negated items, or only negated items, and not a combination of both. Because a negation implies anything which is not the item being negated, the inclusion of non-negated items in the same list will create a contradictory logic for the scope of the list. For example, using a negation such as plugin_sid="5901, !5902" states that the rule will occur when matched with the plugin signature ID of 5901, while simultaneously stating that everything that doesn't match plugin signature ID 5902 should be used to match the rule, creating a contradiction in what will trigger the event. This logic also extends to subsequent rules in the directive.
Using Attribute Values from the Previous Rule
When there are multiple rules in a directive, subsequent rules often use the same value set in the previous rule. In the example above, the "1:DST_IP" notation in the TO attribute means to keep using the same destination IP selected in the first rule, to look for attacks against the same host. You can manually select the destination IP again, or you can use the option From a parent rule: Destination IP from level 1:

You will find this option available when setting the Source, Source Port, Destination, Destination Port, Event Type (must select the data source first), and Sensor attributes. In addition, when editing String type attributes (see Correlation Rule Attributes), you can use the same <rule number>:<attribute name> notation. For example, "2:USERNAME" would mean to use the same user name chosen in the second rule.

 Feedback
Feedback