USM Anywhere implements the role-based access control (RBAC) Describes authentication and authorization scheme in which access to functionality is based on the privileges or permissions associated with the group or role a user is a member of., which provides users with the following:
- The ability to restrict certain users from accessing administrative capabilities like adding new users and sensors Sensors are deployed into an on-premises, cloud, or multi-cloud environment to collect logs and other security-related data. This data is normalized and then securely forwarded to USM Anywhere for analysis and correlation.
- Predefined roles Tasks and responsibilities based on job description and position within an organization. A user's role is often used to define access to functionality and privileges to perform specific tasks and operations. that range from read-only access to full administrative capabilities so users can easily select the appropriate role for a new user
There are four roles in USM Anywhere:
- Read-Only: You can access views and search the system, but you cannot make system changes that impact other users.
- Investigator: You can access views, search the system, and generate reports, but you cannot make system changes that impact other users.
- Analyst: You can view and search the system, schedule jobs, launch actions In USM Anywhere you can execute an action from alarms, events, and vulnerabilities to run a scan, get forensic information, or execute a response for a configured BlueApp., configure rules, and configure asset An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. credentials. But you cannot add or modify sensor configurations; configure credentials for AlienApp [[[Undefined variable Core.ProductBlueApps]]] extend the threat detection and security orchestration capabilities of the USM Anywhere platform to other security tools that your IT team uses, providing a consolidated approach to threat detection and response., notification Communication of an important event, typically through an email message or other desktop display. In USM Appliance, notifications are typically triggered by events, policies, and correlation directives, and in USM Anywhere, they are typically triggered by notification rules or directly from alarms. apps, and threat intelligence Evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice about an existing or emerging hazard to assets that can be used to inform decisions regarding the subject's response to that hazard. integrations; or add users.
- Manager: This role enables analyst permissions and enables you to add or modify sensor configurations; configure credentials for BlueApps, notification apps, and threat intelligence integrations; and add users.
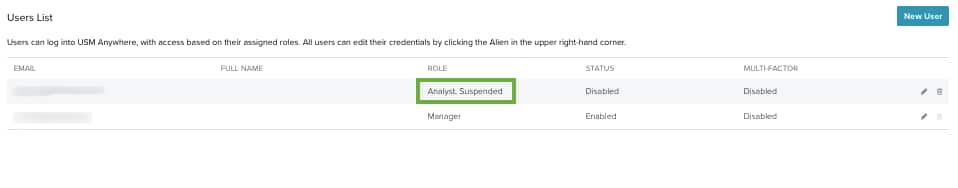
You can view a user's role under the Users List by going to Settings > Users.
Note: Only users in the Manager role can view the Users page.
When the status of a user changes to Disabled, the role column of that user in the User List will include Suspended.
All LevelBlue documentation will tell you which roles can perform a specific set of steps, using a table like the one below.
 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
You can see the predefined roles in USM Anywhere in the following table:
| Section | Action | Read-Only User | Investigator User | Analyst User | Manager User |
|---|---|---|---|---|---|
| Dashboards | Dashboard and dashboard views |

|

|

|

|
| Create custom dashboard |

|

|

|

|
|
| Upper Navigation | Access: documentation, support, and forum links |

|

|

|

|
| Profile settings |

|

|

|

|
|
| Activity > Alarms | View: alarms Alarms provide notification of an event or sequence of events that require attention or investigation. page and alarm details |

|

|

|

|
| Configure filters |

|

|

|

|
|
| Asset drop-down menu items: add to current filter, find in events, look up in AT&T LevelBlue Labs Open Threat Exchange OTX™ The world’s first truly open threat intelligence community that enables collaborative defense with actionable, community-powered threat data. This repository provides a continuous view of real time malicious activity. |

|

|

|

|
|
| Asset drop-down list: full details, configuration issues An identified configuration of deployed software or features of software that is in use, which is known to be insecure., vulnerabilities A known issue or weakness in a system, procedure, internal control, software package, or hardware that could be used to compromise security., alarms, events Any traffic or data exchange detected by LevelBlue products through a sensor or external devices such as a firewall. |

|

|

|

|
|
| Manage columns |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| Save views |

|

|

|

|
|
| Alarm details: suppress alarm, apply label, set a status, add to investigation |

|

|

|

|
|
| Alarm details: alarm action, create rule |

|

|

|

|
|
| Alarm labels: create, manage |

|

|

|

|
|
| Alarm labels: apply |

|

|

|

|
|
| Alarm status: update |

|

|

|

|
|
| Activity > Events | View: events page and event details |

|

|

|

|
| Configure filters |

|

|

|

|
|
| Asset drop-down list: add to current filter, look up in OTX |

|

|

|

|
|
| Asset drop-down list: add to current filter, full details, configuration issues, vulnerabilities, alarms, events |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| Save views |

|

|

|

|
|
| Events details: suppress event, add to investigation |

|

|

|

|
|
| Events details: event action, create rule |

|

|

|

|
|
| Environment > Assets | View: assets page and assets details |

|

|

|

|
| Configure filters |

|

|

|

|
|
|
Asset drop-down list: find in events, look up in OTX, full details, configuration issues, vulnerabilities, alarms, events |

|

|

|

|
|
|
Asset drop-down list: configure asset, delete asset, asset scan, authenticated scan Authenticated scans are performed from inside the machine using a user account with appropriate privileges. |

|

|

|

|
|
| Manage columns |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| Save views |

|

|

|

|
|
| Actions menu: create asset (quick, advanced), import assets, delete selected, edit fields, assign credentials, set sensor, set compliance scope, add to asset group Asset groups are administratively created objects that group similar assets for specific purposes. |

|

|

|

|
|
| Asset details: deploy an agent, assign credentials, schedule a job |

|

|

|

|
|
| Asset details, actions menu: configure asset, delete asset, add to asset group |

|

|

|

|
|
| Asset details, actions menu: agent query, asset scan, authenticated scan, assign credentials, schedule scan job |

|

|

|

|
|
| Create event if asset stops sending data |

|

|

|

|
|
| Environment > Asset Groups | View: asset groups page and asset groups details |

|

|

|

|
| Configure filters |

|

|

|

|
|
| Asset group drop-down list: full details, configuration issues, vulnerabilities, alarms, events |

|

|

|

|
|
| Asset group drop-down list: configure asset group, delete asset group, asset group scan, assign credentials, authenticated scan |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| Save views |

|

|

|

|
|
| Actions menu: create asset group (static and dynamic) |

|

|

|

|
|
| Asset group details, actions menu: configure asset group, delete asset group, edit fields, assign credentials to group members, assign agent profile, set sensor, set compliance scope, asset group scan, assign credentials, authenticated scan, schedule scan job |

|

|

|

|
|
| Environment > Vulnerabilities | View: vulnerabilities page and vulnerabilities details |

|

|

|

|
| Generate report |

|

|

|

|
|
| Save views |

|

|

|

|
|
| Vulnerability labels: apply, create, manage |

|

|

|

|
|
| Asset drop-down list: add to current filter, find in events, look up in OTX, full details |

|

|

|

|
|
| Asset drop-down list: configure asset, delete asset |

|

|

|

|
|
| Asset drop-down list: asset scan, assign credentials, authenticated scan |

|

|

|

|
|
| New scan |

|

|

|

|
|
| Vulnerabilities details: select action, apply label |

|

|

|

|
|
| Environment > Configuration Issues | View: configuration issues page and configuration issues details |

|

|

|

|
| Configure filters |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| Save view |

|

|

|

|
|
| Asset drop-down list: add to current filter, look up in OTX, full details, configuration issues, vulnerabilities, alarms, events |

|

|

|

|
|
| Asset drop-down list: configure asset, delete asset |

|

|

|

|
|
| Asset drop-down list: asset scan, assign credentials, authenticated scan |

|

|

|

|
|
| Configuration issues details, actions menu: configure asset, delete asset, add to asset group, agent query, asset scan, authenticated scan, assign credentials, schedule scan job |

|

|

|

|
|
| Configuration issues details: deploy an agent, assign credentials, schedule a scan job |

|

|

|

|
|
| Environment > Users | View users page and user details |

|

|

|

|
| User drop-down list: find in events, full details, configuration issues, alarms, events, configure user, delete user |

|

|

|

|
|
| User drop-down list: configure user, delete user |

|

|

|

|
|
| User drop-down list: user scan |

|

|

|

|
|
| Manage columns |

|

|

|

|
|
| Generate report |

|

|

|

|
|
| User menu: import users, delete selected, edit fields, configure user, user scan |

|

|

|

|
|
| Schedule user scan job |

|

|

|

|
|
| Reports > Saved Reports | View the saved reports page |

|

|

|

|
| Edit, copy, and delete reports |

|

|

|

|
|
| Reports > Compliance Templates | View the compliance templates reports page |

|

|

|

|
| Generate reports |

|

|

|

|
|
| Reports > Event Type Templates | View the event type templates reports page |

|

|

|

|
| Generate reports |

|

|

|

|
|
| Data Sources > Sensors | View the sensor page |

|

|

|

|
| Add a new sensor |

|

|

|

|
|
| Configure a sensor |

|

|

|

|
|
| Edit a sensor |

|

|

|

|
|
| Assign a sensor |

|

|

|

|
|
| Delete, redeploy a sensor |

|

|

|

|
|
| Data Sources > AlienApps | Available apps |

|

|

|

|
| Data Sources > Agents | Run an agent query |

|

|

|

|
| Delete an agent |

|

|

|

|
|
| Assign an agent configuration profile |

|

|

|

|
|
| Data Sources > Cloud Connector | View connector |

|

|

|

|
| Edit connector |

|

|

|

|
|
| Add a connector |

|

|

|

|
|
| Delete connector |

|

|

|

|
|
| Add new data source rule |

|

|

|

|
|
| Enable and disable a cloud connector |

|

|

|

|
|
| Investigations | View investigations page |

|

|

|

|
| Edit an investigation |

|

|

|

|
|
| Create a new investigation |

|

|

|

|
|
| View investigations details |

|

|

|

|
|
| Delete an investigation |

|

|

|

|
|
| Notification rule for investigations |

|

|

|

|
|
| Add a note |

|

|

|

|
|
| Run app action |

|

|

|

|
|
| Settings > Scheduler | View the job scheduler page |

|

|

|

|
| Create, edit, enable, disable a job |

|

|

|

|
|
| Settings > Rules | View the rules page |

|

|

|

|
| Create an orchestration rule |

|

|

|

|
|
| Create a correlation list |

|

|

|

|
|
| Settings > Notifications | Modify credentials |

|

|

|

|
| Settings > System | View the system monitor page |

|

|

|

|
| View the network settings page |

|

|

|

|
|
| Create asset field |

|

|

|

|
|
| Enable required multifactor authentication |

|

|

|

|
|
| Modify the session timeout |

|

|

|

|
|
| Settings > System Events | View the system events page |

|

|

|

|
| Settings > Console User Events | View the console user events page |

|

|

|

|
| Settings > OTX | Validate an OTX subscription key |

|

|

|

|
| Settings > Credentials | View the credentials page |

|

|

|

|
| Create a new credential |

|

|

|

|
|
| Edit, delete, and manage credentials |

|

|

|

|
|
| Settings > Users | |||||
| View the user page |

|

|

|

|
|
| Create a user |

|

|

|

|
|
| Edit a user |

|

|

|

|
|
| Delete a user |

|

|

|

|
|
| Settings > My Subscription | View the my subscription page |

|

|

|

|
| Purge data |

|

|

|

|
|
| Connect to USM Central™ |

|

|

|

|
 Feedback
Feedback