 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
Depending on the USM Anywhere Sensor you have installed, the widgets might be visible in the
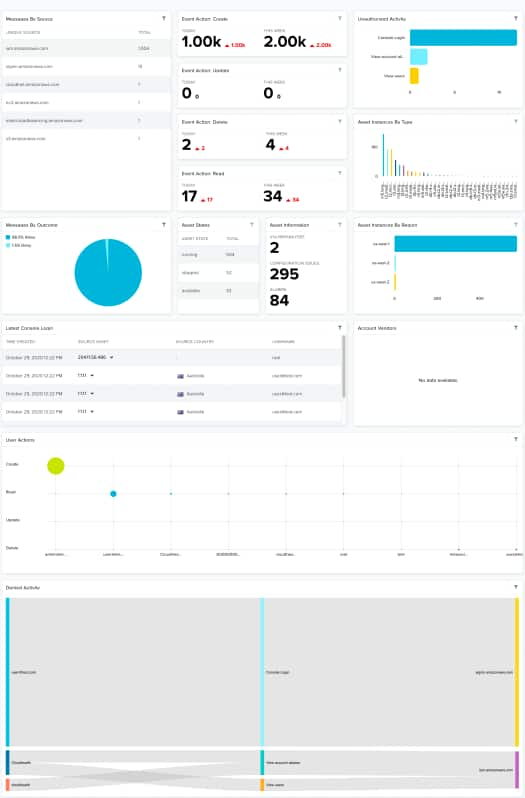
| Widgets | Description |
|---|---|
| Messages by Source | List of the fifteen assets An IP-addressable host, including but not limited to network devices, virtual servers, and physical servers. receiving the most messages. |
| Event Action: Create | Total number of assets created for the current day and for the current week. |
| Event Action: Update | Total number of assets updated for the current day and for the current week. |
| Event Action: Delete | Total number of assets deleted for the current day and for the current week. |
| Event Action: Read | Total number of assets read for the current day and for the current week. |
| Unauthorized Activity | List of the unauthorized activity that has been made on events Any traffic or data exchange detected by LevelBlue products through a sensor or external devices such as a firewall.. |
| Asset Instances by Type | List of asset instances ordered by type. |
| Messages by Outcome | Pie chart displaying, in percentages, the outcome for access control, which can be Allow or Deny. |
| Asset States | List of the state of the assets and the total number at each state. |
| Asset Information | Total number of assets having vulnerabilities A known issue or weakness in a system, procedure, internal control, software package, or hardware that could be used to compromise security., configuration issues An identified configuration of deployed software or features of software that is in use, which is known to be insecure., and alarms Alarms provide notification of an event or sequence of events that require attention or investigation.. |
| Asset Instances by Region | Total number of asset instances by region. |
| Latest Console Login | Date of the latest console login Log in (verb): Process in which an individual gains access to a computer system after providing sufficient credentials to authenticate their unique identity. Login (noun): User credentials, typically a username and matching password.. |
| Account Vendors | Pie chart displaying, in percentages, the known vendor services in AWS. |
| User Actions | Users related to the implied action of the event, which can be create, read, update, and delete. The size of the bubbles depends on the number of issues |
| Denied Activity | Sankey diagram which displays the source username, the event name, and the data in which the events were received. |
 Feedback
Feedback