The simplest method to receive NXLog messages is to install NXLog Community Edition (CE) on each Microsoft Windows host and configure it to forward messages to the USM Anywhere Sensor. In the event of a sensor disconnect, NXLog messages are cached locally and will be forwarded when the connection resumes.
To install NXLog and create your configuration file
-
On your Windows host, download and install the latest version of NXLog.
Note: The NXLog Community Edition is open source and free of charge. But to use the File Integrity Monitoring plugin, you must download and install the NXLog Enterprise Edition instead. See vendor documentation for more information.
- Make a backup copy of the original file and give it another name. Depending on the version, this file can be C:\Program Files (x86)\nxlog\conf\nxlog.conf (32-bit) or C:\Program Files\nxlog\conf\nxlog.conf (64-bit).
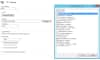
- Log in to USM Anywhere and go to Settings > System.
-
In the left navigation panel, click NXLog Configuration to open the page.
By default, USM Anywhere displays all the plugins available for the 32-bit Windows system.
-
Select the desired Windows system and the plugin (or plugins) to collect NXLogs. You don't need to select any plugin to collect default Windows Logs or Sysmon logs.
Note: Plugins with asterisk require additional configuration on the Windows host. See Enable Logging in Vendor Software for details.
-
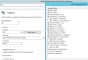
Select the protocol you want to use.
 Download the TLS Certificate
Download the TLS Certificate
To use TLS, you need to download the certificate and save the file USM-NXLog-Agent-TLS-CA.pem in the \nxlog\cert\ directory on your machine.
- Enter the IP address of your USM Anywhere Sensor.
- Click Create File to generate the new nxlog.conf file and save it to the \nxlog\conf\ directory on your machine.
- Open Windows Services and restart the NXLog service.
- In USM Anywhere, verify that you are receiving NXLog events.
If you decide not to use NXLog after the installation, you can uninstall the program using the Add or Remove Programs feature in the Windows Control Panel, or see How to Uninstall NXLog for detailed instructions from the vendor.
PatternDB
If you want to limit the events collected and sent to USM Anywhere, you can download the patterndb file provided by LevelBlue and place it in the \nxlog\conf\ directory on your machine. Follow the procedure above to download the NXLog configuration file and select the PatternDB plugin.
Important: Windows Event IDs not present in patterndb.xml are not forwarded. Excluding events not relevant to security helps improve the overall performance of the plugin. Consequently, some correlation rules may not be triggered because they rely on those events.
Microsoft Sysmon
System Monitor (Sysmon) is a Windows system service and device driver that remains resident across system reboots to monitor and log system activity to the Windows Event Log. It provides detailed information about process creations, network connections, and changes to file creation time. Sysmon is a free Windows Sysinternals tool from Microsoft. Using NXLog, you can send Sysmon logs to USM Anywhere for event correlation.
To collect Sysmon logs
- Download the NXLog configuration file from USM Anywhere. You do not need to select any plugin for Sysmon.
-
Open the NXLog configuration file, look for the <Input eventlog> tag and add this line under <QueryList>:
<Select Path="Microsoft-Windows-Sysmon/Operational">*</Select>\
With the line added, it should look like this example:
<Input eventlog>
Module im_msvistalog
Query <QueryList>\
<Query Id="0">\
<Select Path="Application">*</Select>\
<Select Path="System">*</Select>\
<Select Path="Security">*</Select>\
<Select Path="Microsoft-Windows-Sysmon/Operational">*</Select>\
</Query>\
</QueryList>
</Input>
- Save the file.
- Open Windows Services and restart the NXLog service.
- In USM Anywhere, verify that you are receiving Sysmon events.
Enable Logging in Vendor Software
Some of the vendor plugins need to be configured to enable logging so that USM Anywhere can receive the logs. If you are using any of the plugins below, follow the described integration process to initiate system logging for the plugin.
Before configuring NXLog, you must download and install the Dell Boomi Atom on your host. Follow the steps in the Boomi AtomSphere Documentation to download the local Atom installer.
Before configuring NXLog, you must export the Duo Authentication Proxy events to a secondary log file. See Enabling SIEM Logging in the Duo Authentication Proxy for detailed instructions from the vendor.
Before configuring NXLog, you need to format data in Forcepoint (formerly Websense) Web Security Cloud for use by USM Anywhere. See Exporting data to a third-party SIEM tool for detailed instructions from the vendor.
Before configuring NXLog, you need to configure logging in the Microsoft 365 SharePoint Server. See Configure diagnostic logging in SharePoint Server for detailed instructions from the vendor.
Before configuring NXLog, you need to enable debug logging on the DNS server.
To enable DNS server debug logging
- From the Windows Start Menu, select All Programs > Administrative Tools > DNS.
- From the console tree, right-click the applicable DNS server, and then click Properties.
-
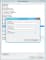
Click the Debug Logging tab.
-
Select Log packets for debugging.
The most useful debug logging output comes from selecting at least three options:
- One option under Packet direction
- One option under Transport protocol
- At least one more option in another category
-
(Optional) Consider limiting the traffic captured by applying filters:
- Select Filter packets by IP address.
- Add the appropriate IP addresses by clicking Filter.
Warning: Do not select the Details option, because it produces logs in multi-line format instead of single-line, which the USM Anywhere plugins cannot process.
-
Specify the name and location for the log file.
For example, in the screenshot above, the file path and name is C:\logs\dns.log. If you use a different file path, you will need to open the nxlog.conf file with a text editor and update the file path in the DNS-NXLOG section to reflect the file path you are using.
- Click Apply to save and apply the settings.
- Ensure that the log messages use the MM/DD/YYYY date format so USM Anywhere can parse the data correctly.
The Microsoft Internet Information Services (IIS) Management Pack includes a FTP Server that you can configure. (See vendor website for documentation.)
Before configuring NXLog, you must configure FTP logging in IIS.
To configure FTP Logging in IIS Manager
- Open IIS Manager.
- In the Connections tab, select either the server or the site, and then click the FTP Logging icon.
-
Under Log File, click Select W3C Fields, and then select the information you want to log.
Make sure to select the items checked in the screenshot below and click OK.
- Select UTF8 under Encoding and Daily under Schedule.
- Click Apply.
- Restart the FTP Server for the changes to take effect.
Before configuring NXLog, you need to configure logging for the Microsoft HTTP Server API. See Configuring HTTP Server API Error Logging for detailed instructions from the vendor.
Before configuring NXLog , you need to first configure logging on IIS.
To configure logging at the server level
- Open the IIS Manager.
- In the Connections tab, select the server and double-click the Logging icon.
- Under One log file per, select Site.
-
Under Log File, click Select Fields to choose the information you want to log.
Make sure to match the following screenshot because the Windows IIS plugin will look for these fields:
-
To use the Windows IIS Extended plugin, you must also enable Bytes Sent (sc-bytes), Bytes Received (cs-bytes), and Host (cs-host). In addition, you can add a custom field for X-Forwarded-For by clicking Add Field to fill in the information as shown:
Note: If you're using Microsoft Windows Server 2008, which doesn't provide an option to add more fields, the Window IIS Extended plugin won't work. Please use the Windows IIS plugin instead.
- Click Apply.
Before configuring NXLog, you need to configure logging for Network Policy Server (NPS) in Microsoft Windows Server 2016 and Server 2019. See Configure NPS Log File Properties for detailed instructions from the vendor. Make sure to select DTS Compliant as the log format.
Before configuring NXLog, you must have enabled the SQL Server Audit feature and send audit results to the Windows Application Log.
Note: You can use SQL Server Management Studio or Microsoft Transact-SQL (T-SQL) to perform this task. See the Microsoft documentation if you need detailed step-by-step assistance.
To use the SQL Server Management Studio
-
Create a new server audit:
- In Object Explorer, expand the Security folder, right-click the Audits folder, and select New Audit.
- In the Audit destination list, select Application Log.
- Select the other options as needed and click OK.
-
Create a database-level audit specification
- In Object Explorer, expand the database you want to send log to USM Anywhere.
- Expand the Security folder, right-click the Database Audit Specifications folder and select New Database Audit Specification.
- In the Audit list, select the audit you created in the previous step.
- Select the other options as needed and click OK.
Netwrix provides a free add-on for LevelBlue to integrate Netwrix Auditor with USM Anywhere through the RESTful API. Before configuring NXLog, you must first use the add-on to generate special Windows event logs for USM Anywhere.
If you haven't already, download the add-on from the Netwrix website. Follow the detailed instructions in their Quick-Start Guide to install and properly configure the add-on. Make sure you have reviewed the events generated by the add-on, as documented in the Quick-Start Guide.
The ObserveIT plugin leverages the integration support that ObserveIT provides for the HP ArcSight SIEM monitoring software. To configure the SIEM Log Integration, follow the ObserveIT documentation, Configuring CEF Log Integration.
Warning: ObserveIT has been renamed Proofpoint Insider Threat Management.
Important: Follow the steps closely and keep all the default values even though they contain the word "ArcSight". The NXLog configuration file that you download from LevelBlue has been specified to parse logs in the default location.
Before configuring NXLog, you need to request a bulk export of audit logs for Oracle Cloud Infrastructure. See Bulk Export of Audit Log Events for detailed instructions from the vendor.
You must download and install the Sophos Reporting Log Writer for this integration. Follow the instructions in the Sophos Reporting Log Writer user guide.
Before configuring NXLog, you must first enable logging in Windows Firewall with Advanced Security.
To enable logging in Windows Firewall
- Open Windows Firewall with Advanced Security.
- In the Actions panel, click Properties.
- On the Domain Profile tab, click the Customize button in Logging.
-
In the new window, complete these steps:
- Keep the name as default.
- Increase the Size limit (KB) to 8192.
- Change both Log dropped packets and Log successful connections to Yes.
-
Click OK.
Manual File Creation and Installation Process
If you are unable to create the nxlog.conf file using the process above, or if you wish to edit it manually, you can use the manual process instead.
To install NXLog CE and configure forwarding
-
Download the latest stable version of NXLog.
Note: The NXLog Community Edition is open source and free of charge. But to use the File Integrity Monitoring plugin, you must download and install the NXLog Enterprise Edition instead. See vendor documentation for more information.
- Make a backup copy of the original file, C:\Program Files (x86)\nxlog\conf\nxlog.conf (32-bit) or C:\Program Files\nxlog\conf\nxlog.conf (64-bit), and give it another name.
- Download the NXLog configuration for USM Anywhere and save it as your new nxlog.conf file.
-
Open the configuration file for editing and replace usmsensoriphere with the IP address of the USM Anywhere Sensor.
USM Anywhere listens for syslog at UDP port 514, TCP port 601, or TLS/TCP port 6514.
-
Depending on the protocol you decide to use, edit the configuration file as detailed below. Make sure USM Anywhere allows inbound requests to the corresponding port.
 To Use UDP
To Use UDP
Keep the defaults and move to the next step.
 To Use TCP
To Use TCP
- Replace define OUTPUT_DESTINATION_PORT 514 with define OUTPUT_DESTINATION_PORT 601.
-
In <Output out>, replace Module om_udp with Module om_tcp.
Note: If you are collecting logs from other products as detailed in the next step, you must modify the Output settings in the corresponding section as well. For example, if you are collecting logs from Microsoft Internet Information Services (IIS), you will need to update the <Output IIS_OUT> section too.
 To Use TLS
To Use TLS
-
First, you need to download the certificate from USM Anywhere, and place the file USM-NXLog-Agent-TLS-CA.pem in the \nxlog\cert\ directory on your machine.
-
In the nxlog.conf file, add define CERTDIR %ROOT%\cert after the last define statement.
- Replace define OUTPUT_DESTINATION_PORT 514 with define OUTPUT_DESTINATION_PORT 6514.
-
In <Output out>, complete these steps:
- Replace Module om_udp with Module om_ssl.
-
Add these two lines:
CAFile %CERTDIR%\USM-NXLog-Agent-TLS-CA.pem
AllowUntrusted TRUE
Note: If you are collecting logs from other products as detailed in the next step, you must modify the Output settings in the corresponding section as well. For example, if you are collecting logs from IIS, you will need to update the <Output IIS_OUT> section too.
- Some sections in the nxlog.conf file have been commented out to improve performance. Depending on which product you want to collect logs from, you need to uncomment the corresponding section or sections.
- Save the file.
- Open Windows Services and restart the NXLog service.
- Log in to USM Anywhere and verify that you are receiving NXLog events.
Note: If you need to debug NXLog, open \nxlog\data\nxlog.log.




 Feedback
Feedback