With Amazon Web Services (AWS) Virtual Private Cloud (VPC) Traffic Mirroring, network traffic from your AWS environment can be mirrored and sent directly to your sensor for monitoring, bringing network intrusion detection system (NIDS) Network Intrusion Dectection System (NIDS) monitors network traffic and events for suspicious or malicious activity using the sensors that provide management and network monitoring interfaces to networks and network devices. functionality to your AWS Sensor.
Important: AWS has a limit of 10 mirror sources per interface. In situations where you need to accommodate a higher number of mirror sources, you will need to deploy additional AWS sensors to mirror or create a NLB as VPC Target. See (Optional.) Create NLB as VPC Target for more information.
See Amazon's documentation on traffic mirroring for more information regarding mirroring.
Prepare Your Environment for VPC Traffic Mirroring
To enable VPC Traffic Mirroring, you must first ensure the following:
- Your sensor is at least an m5.xlarge
- Your sensor has a second network interface configured, called the traffic interface
- Your firewall rules allow virtual extensible local area network (VXLAN) traffic through your traffic interface (inbound UDP 4789 is applied)
Note: If you select Enable Traffic Mirroring when you first deploy (or redeploy) the sensor, these requirements are automatically set up for you. Otherwise, you must make all three of these changes manually.
Configuring VPC Traffic Mirroring
To run VPC Traffic Mirroring in your environment, you must create and configure the following:
- Create a security group: The security group configures the UDP protocol, and the inbound and outbound traffic.
- Create a network interface: The network interface specifies the subnet you want to monitor.
- Attach the sensor: Attach the sensor to the configured information.
- Create a target: This target serves as the destination for your mirrored traffic.
- Define a mirror filter: The mirror's filter specifies which traffic is mirrored for your AWS Sensor.
- Create the mirror session: This session configures precisely how your traffic is mirrored.
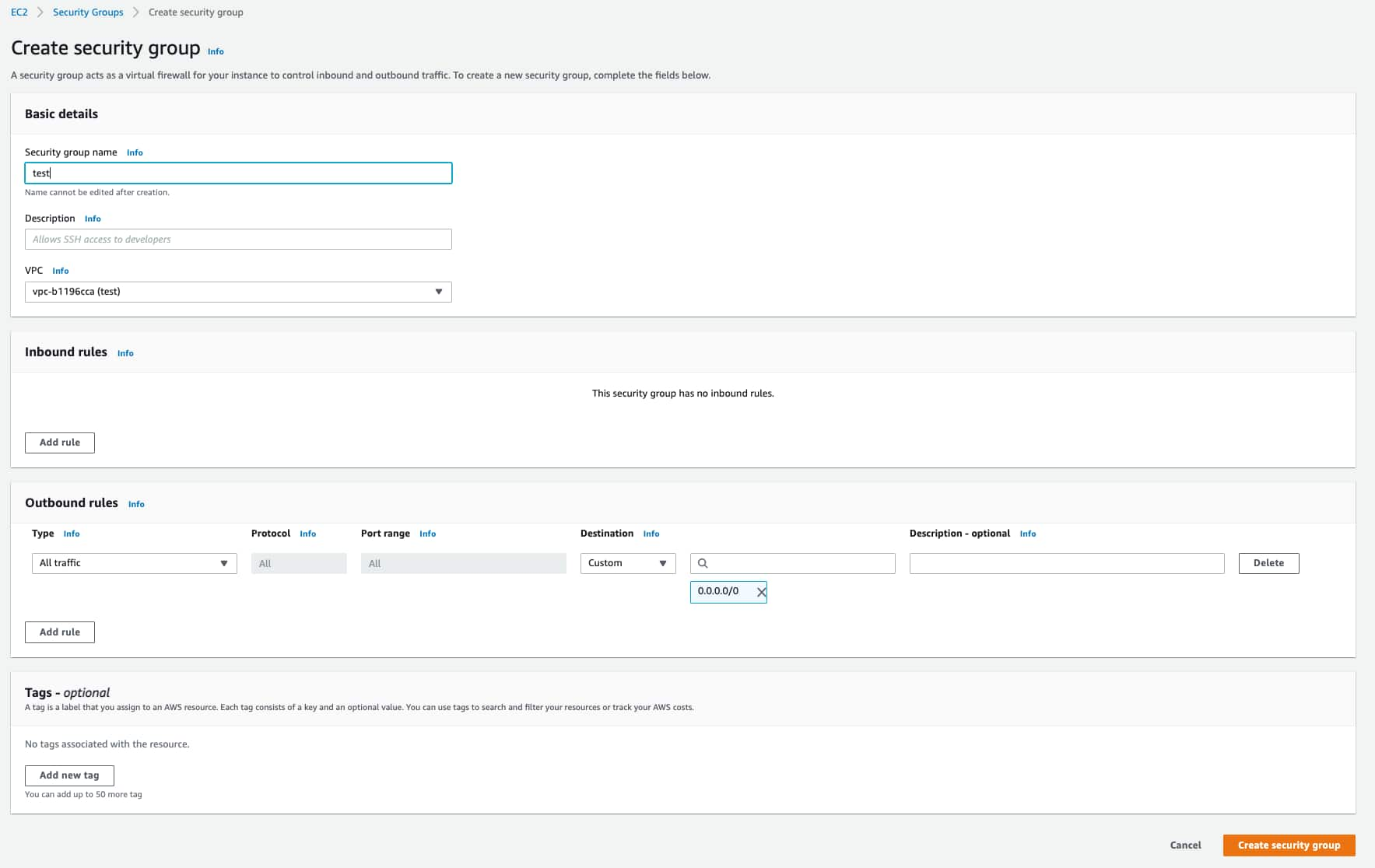
To create a security group
- Go to Network & Security > Security Groups in your AWS Management Console.
- Click Create security group.
- Enter the following:
- Security group name: A name for this security group
- Description: A description of this security group
- VPC: A VPC for this security group
- UDP Protocol: Enter the 4789 port
- Inbound: The traffic must be admitted
- Outbound: Select all traffic, all protocol, all port range, and 0.0.0.0/0 as the destination
-
Click Create security group.
To create a network interface
- Go to Network & Security > Network Interfaces in your AWS Management Console.
- Click Create Network Interface.
- Enter the following:
- (Optional.) Description: A description of this network interface
- (Optional.) Subnet: Select the subnet you want to monitor
- Security group: Select the security group you've created
- Click Create Network Interface.
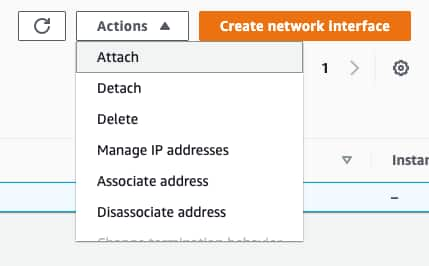
To attach the sensor
- Go to Network & Security > Network Interfaces in your AWS Management Console.
- Click Actions > Attach.
- Select your instance.
- Click Attach.
- Reload the sensor.
To create a target
- Go to Networking & Content Delivery > VPC in your AWS Management Console and click Mirror Targets under Traffic Mirroring.
- Click Create traffic mirror target.
- Enter the following:
- (Optional.) Name tag: A name for this target
- (Optional.) Description: A description of this target
- Target Type: This value must be Network Interface
- Target: The identification (ID) of your instance's traffic interface
-
(Optional.) If you use tags to organize your AWS resources, you can add tags to this target.
- Click Create.
Important: Each elastic network interface (ENI) has a three session limit per ENI. If you use a Network Load Balancer (NBL) as your mirror target, there is no session limit. See (Optional.) Create NLB as VPC Target for more information.
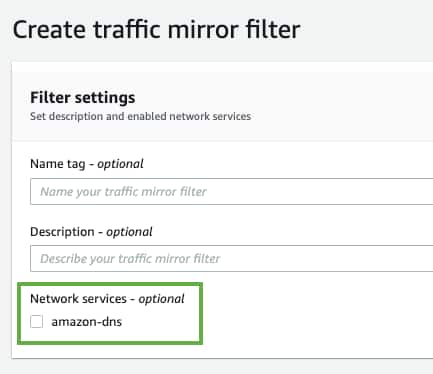
To define the mirror filter
This filter defines what traffic is mirrored to your AWS Sensor. You can specify inbound and outbound filters, as well as applying filters for Amazon network services.
- Go to Networking & Content Delivery > VPC in your AWS Management Console and click Mirror Filters under Traffic Mirroring.
- Click Create traffic mirror filter.
- (Optional.) Enter the following information:
- Name tag: A name for your traffic mirror filter
- Description: A description for your traffic mirror filter
- Network services: Select this checkbox to have your filter mirror network services data
- Configure your inbound and outbound filtering rules.
- Click Add rule.
- Use the options provided to define these rules:
- Number: Priority settings to order which rules are evaluated before others
- Rule Action: Specify the action (accept or reject) to take for the filtered packet
- Protocol: Specify one protocol to collect specific traffic, or select All protocols to collect all traffic
- (Optional.) Source Port Range: Specify the source port range you want to filter
- (Optional.) Destination Port Range: Specify the destination port range you want to filter
- Source CIDR Block: Specify the source IP ranges you want to filter
- Destination CIDR Block: Specify the destination IP ranges you want to filter
- (Optional.) Description: A description for this filtering rule
- (Optional.) If you use tags to organize your AWS resources, you can add tags to this filter.
- Click Create.
Note: If you want your filter to capture Domain Name System (DNS) traffic, you must select the amazon-dns checkbox.
To create a session
- Go to Networking & Content Delivery > VPC in your AWS Management Console and click Mirror Sessions under Traffic Mirroring.
- Click Create traffic mirror session.
- Enter the following information:
- (Optional.) Name tag: A name for your traffic mirror session
- (Optional.) Description: A description for your traffic mirror session
- Mirror Source: The network interface ID of the instance you want to monitor
- Mirror Target: The ID of your instance's traffic interface
- Session Number: Priority settings to order which sessions are evaluated before others
- VNI: Set this to 1169
- (Optional.) Packet length: The number of bytes from each packet to mirror
- Filter: The filter you have created for your VPC Traffic Mirroring session
(LevelBlue recommend leaving this blank to mirror the entire packet)
Important: You must select a supported instance type to successfully create a mirror session. See Amazon's documentation on traffic mirroring limitations for a list of supported and unsupported instance types.
- (Optional.) If you use tags to organize your AWS resources, you can add tags to this session.
- Click Create.
Important: You must create one mirror session per device.
(Optional.) Create NLB as VPC Target
You can create a Network Load Balancer (NLB) to use as your VPC target. To create an NLB, follow Amazon's Create a Network Load Balancer instructions, and for the Target Group and Health Check portions of the setup, use the settings provided below.
When you configure the Target Group section, use the following settings:
- Target Type: IP
- Protocol: UDP
- Port: 4789
When you configure the Health Checks section, use the following settings:
- Protocol: HTTP
- Path: /api/2.0/status
Advance Health Check Settings:
- Override: Port - 80

 Feedback
Feedback