Introduction
As of today, no laws or regulations, even the latest version of PCI-DSS, HIPAA, and HITECH, do not make network segmentation or micro-segmentation compulsory to comply with the rule. By making network segmentation discretionary -- even when transmitting, processing, or storing regulated data, the number of breaches will continue to rise as companies err on the side of doing less with more.
The purpose of this article is not to explain the contemporary need of network segmentation and micro-segmentation. Instead, it attempts to clarify the antithetical distinction between the two to reframe the widely used narrative that the two concepts are one and the same.
History
In March of 2017, I wrote my first article on network segmentation titled A Project Management Approach to Designing, Implementing, and Operationalizing Network Isolation and Micro-Segmentation. Over the last two years, since that article was published, flat networks still seem to be a problem endemic to every industry. Even entities operating in regulated environments, such as the payment card industry (PCI) or in healthcare where we’ve seen connected biomedical devices accessible from a hospital’s guest wireless network.
Similarly, as of PCI-DSS version 3.2, network segmentation is still not compulsory to comply with PCI for merchants. However, if network segmentation is not implemented, it brings the entire network into scope of the PCI assessment, which can add significant time and costs to the entity for passing its annual QSA audit to earn its report on compliance (ROC).
While it’s widely understood what network segmentation is, the concept of micro-segmentation seems to keep becoming conflated with network segmentation when in fact they describe two completely separate concepts that can be mutually exclusive; meaning, you can have both network segmentation and micro-segmentation - so they are not one and the same. I present examples of separate implementations of why conflating the two concepts can be costly or introduce pivoting potentials in a breach, especially in conflict areas when connecting forward operating bases (FOBs) to classified networks,
What is network segmentation?
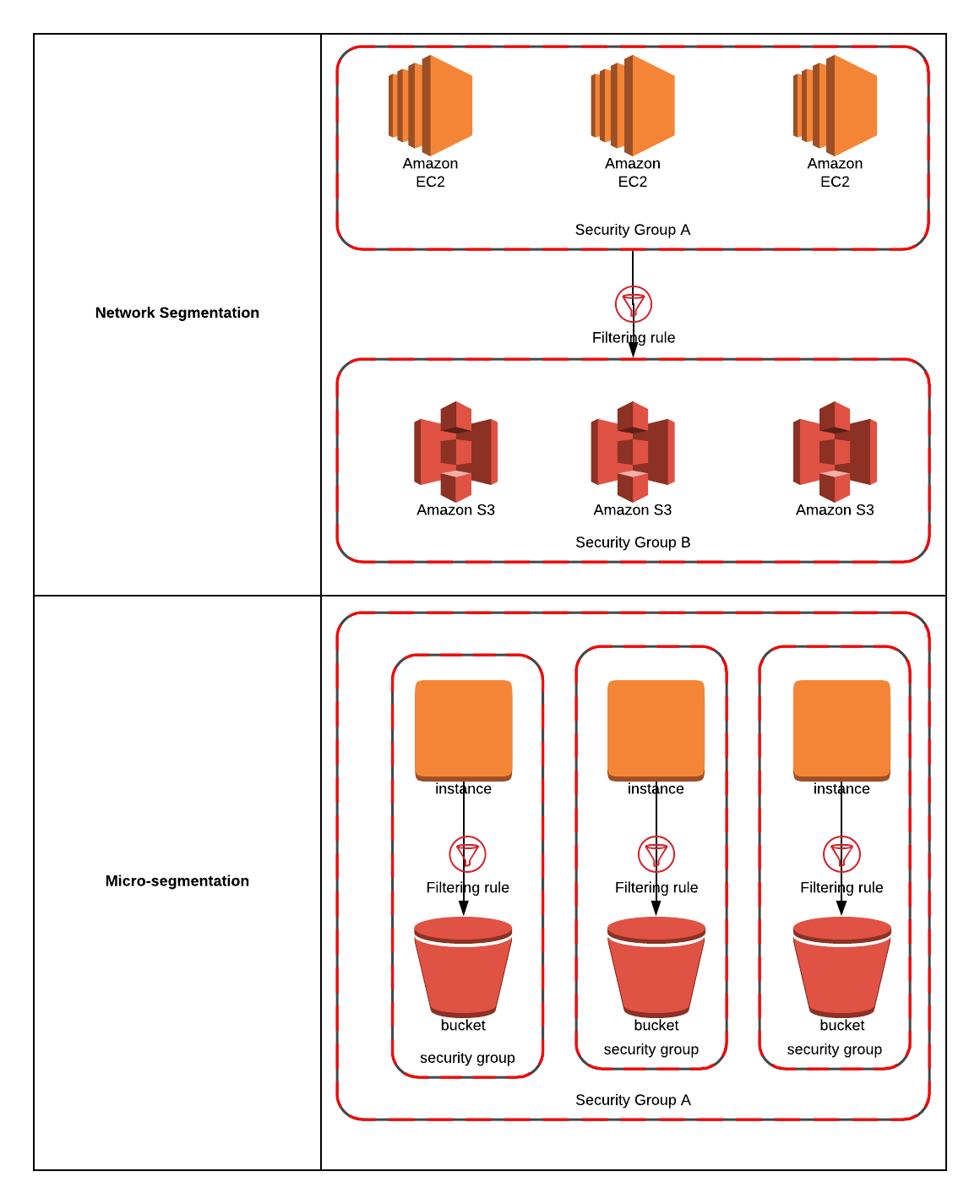
Figure 1. Segmentation versus Micro-Segmentation.
Source: Alissa Knight
Network segmentation can be easily described as taking one large flat network and using firewall rules or VLAN access control lists (VACLs), define rules that permit or deny the directionality of traffic between hosts.
What is micro-segmentation?
Micro-segmentation is the concept of network segmentation but at a much more diminutive scale where nodes within the same VLAN are isolated into a sort-of enclave. Micro-segmentation is akin to a client VPN where two hosts communicate with one another and the rest of the hosts within the same network are unable to talk to or see those hosts. When network segmentation is implemented, the default route of the VLAN is set to a firewall or VACLs are used to control what hosts they can communicate with outside the VLAN. With micro-segmentation, isolation of hosts can happen between hosts in different VLANs or in an enclave within the same VLAN.
The business case for micro-segmentation
Your first question might be when micro-segmentation should be applied and what the business case is for such a scenario. Here, I provide three examples of scenarios where micro-segmentation makes sense.
Network-in-a-Box (NIB). When the United States deploys ground forces to a new area of operation and a base is constructed, such as a forward operating base (FOB), servers and network connectivity must be implemented. Products created from companies, such as Tecore Networks provide all-in-one wireless systems that house both servers and wireless (4G/LTE, Satellite, etc) connectivity for a FOB to establish connectivity with SIPRNET, NIPRNET, and JWICS within hours.
However, with some vendors that manufacture these NIBS, the three systems are virtual machines all running in a hypervisor sitting behind a single firewall running within that hypervisor's virtual switch. While this prevents pivoting to these systems, it does not protect the hosts from each other within that same enclave. So if the host connecting to SIPRNET were compromised, that host would be capable of talking to the host on NIPRNET, two completely different levels of classification. By implementing micro-segmentation, these three hosts can be completely isolated from one another even though they are running within the same hypervisor.
Limiting PCI scope. When a company that transmits, processes, or stores payment card information, they must perform annual QSA audits by a certified QSA as a result of the number of credit card transactions they process per year. If employees process credit cards on their workstations while connected to the corporate network alongside other employees not performing in-scope PCI activities, it can cause the entire user VLAN in the corporate network to become in-scope for the QSA audit. By implementing micro-segmentation, this one employee or several employees, no matter what VLANs they are in, can be isolated into the in-scope PCI network, removing the corporate network from scope of the QSA audit.
Solution
There are several solutions available now that eliminate the old ways of implementing segmentation at the switch level using VACLs and firewall rules in a new product category called software defined perimeter (SDP) solutions. One particular solution is Stealth by Unisys. Stealth sits at layer 3 in the stack leveraging the operating system of the host the agent has been installed on to create an IPSec tunnel with other hosts, which Unisys refers to as a community of interest (COI).
Stealth incorporates additional capabilities beyond just allowing the administrator to define micro-segmented COIs, but also the ability to “cloak” assets that darkens the host out from being able to be reached by the other hosts outside the COI.
SDP makes implementing micro-segmentation possible with large-scale, disparate networks made of up thousands of nodes around the world that wouldn’t otherwise be possible with a traditional approach through hardware segmentation at the switch level.
If your requirement to implement micro-segmentation extends beyond your premise to the cloud or even multi-cloud assets, Stealth supports cloud service providers and really any network fabric since the micro-segmentation is done at the network layer.
In summary, network segmentation is necessary in a zero-trust security (ZTS) framework, but should be considered different from micro-segmentation, which is far more granular.