Our current global landscape is testing resiliency. As organizations continue to shift to a remote work business model, the rush to digitally transform has created new and heightened cyber risk concerns. Protecting these digital connections needs to stay top of mind for leaders looking to help their organizations adapt to these changes while continuing to innovate.
In this blog, we will look to set the cyberscene and focus on a security first mindset. We will look at the biggest risks facing organizations today, and considerations for CISOs in adapting to the ever-changing landscape.
Security is a process, it's a thought process, it's an approach, and when you approach it from a mindset of Zero Trust, that I can't trust the network, I might not be able to trust the peer services that I'm talking to at some point in the future, it makes you rethink how you would build and design these things. And, I think that puts us on a strong path for how we dig out of the situation that we find ourselves in today, where things just are not as secure as they should be.
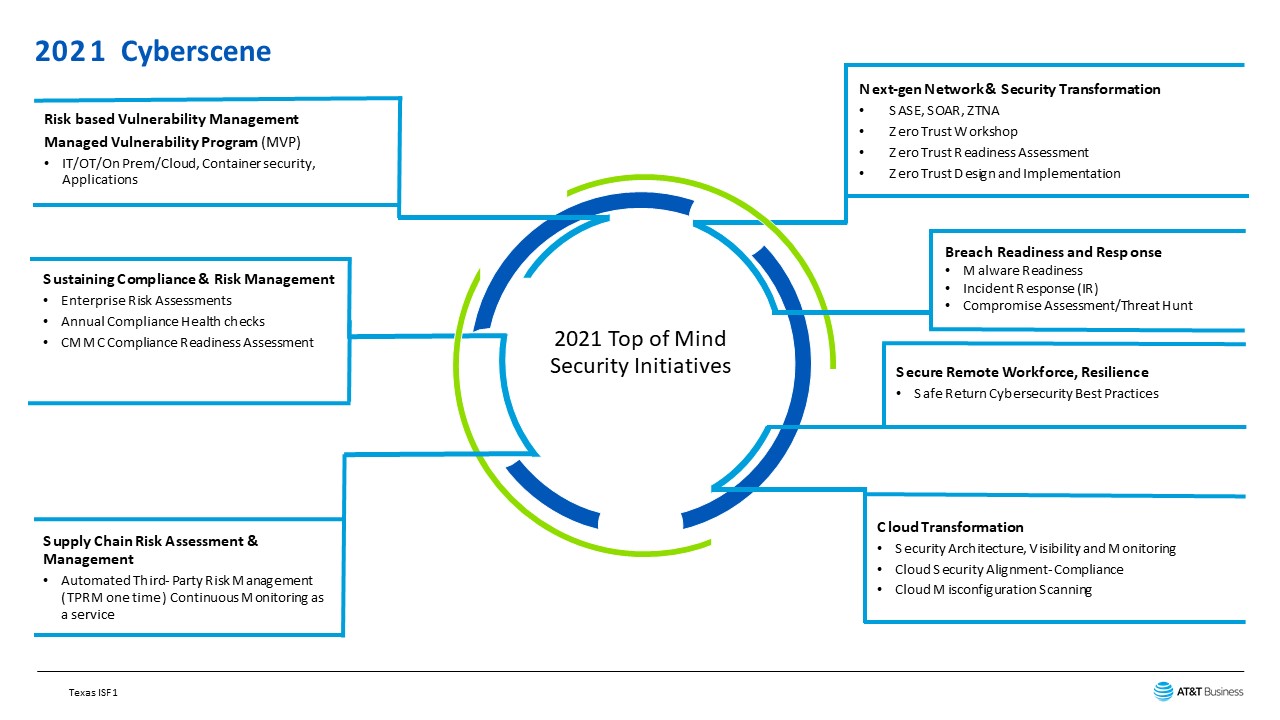
Let’s look at the seven topics that are top-of-mind with CIO’s and CISO’s across the country. Let’s go clockwise from the 1:00 position. This first is a fascinating topic to many – Zero Trust and the many iterations like Zero Trust. We have seen a recurring theme across the breaches over the years: misplaced trust and a focus on perimeter-centric controls. Organizations need to approach Zero Trust as a strategic initiative and not focus on a product-centric strategy. Zero Trust is a security model that takes for granted that threats are omnipresent inside and outside networks. Zero trust instead relies on continuous verification via information from multiple sources.
The Zero Trust approach assumes the inevitability of a data breach. Instead of focusing exclusively on preventing breaches, Zero Trust security ensures that damage is limited and that the system is resilient and can quickly recover.
It's no secret that attacks are constantly evolving and can come from within an organization. Zero Trust security was conceptualized to address vulnerabilities no matter where they may come from. It takes an 'always verify, never trust' approach to network security. This means that every user and device is always verified, regardless of whether they've had previously been granted access.
Because business is becoming more distributed, organizations are moving away from the castle-and-moat approach. Zero Trust security is a robust and thorough security solution that addresses the need for the total protection of global networks. With the Zero Trust model, you gain better visibility across your users, devices, containers, networks, and applications because you verify their security status with every access request.
You can reduce your organization's attack surface by segmenting resources and only granting the absolute minimum access needed. Adopting a Zero Trust approach provides you with a balance between security and usability. Security teams can make it harder for attackers to collect what they need (user credentials, network access, and the ability to move laterally), and users can get a consistent and more productive security experience, regardless of where they are located, what endpoints they are using, or whether their applications are on-premises or in the cloud. With the workforce more dispersed than ever and network perimeters almost non-existent, it is now prime time to adopt a Zero Trust approach.
Breach response and readiness:
When you hear of ransomware in today's world, you read stories of complete shutdowns of companies or organization's means of production or revenue. Demanding increasingly higher ransom amounts, the threat actors appear to have no problems targeting any organization with a computer.
Recently ransomware attacks have targeted companies and organizations involved in critical infrastructures, such as oil and gas delivery, manufacturing, transportation, and even health care. These recent attacks are showing that organizational cybersecurity has more impact than just on the organization. The organization's ability to recover depends not only on having good backups but also on the ability of your IT teams to recover with these backups.
Conducting a recovery from a backup on a system takes time. There may be hundreds of systems that need to be re-imaged in a ransomware situation across critical servers and end-user workstations. The ability to recover from a backup should not be learned when the worst happens. AT&T suggests you practice restoring from a backup at least twice a year under the most realistic circumstances you can replicate. By performing this with your teams, you will enable them to perform at a high level, which can be the difference between a ransomware incident being an annoyance or a full-fledged shutdown of systems.
Securing remote workforce and resilience
Although businesses have been tasked with addressing several remote assets associated with off-site resources, such as a sales force that’s often mobile, the number of remote endpoints has grown exponentially. The laptops and mobile devices needed to facilitate working from home full-time for a large percentage of their workers, given recent global events have exploded.
Companies across all spectrums are challenged with establishing and maintaining an appropriate security posture holistically across their entire Information Technology environment. Against this backdrop of increased cyber risk in a new era of remote access and new work arrangements, organizations must develop new policies, processes, and technical solutions to support this new breed of the mobile-centric workforce.
To provide highly secure, frictionless remote access, organizations must rethink their tactics at all points in the IT ecosystem—data centers, departmental systems, edge computing, and cloud gateways. Overcoming the numerous new and intensified threat vectors requires organizations to think and act upon the following security issues:
- Identity management
- Permissions and privileges
- Policy management
- Bring-your-own policies for devices, applications, and cloud services•
Working remotely is fast becoming the “new normal” for employees and their organizations. The flexibility for employees and organizations is far too compelling for enterprises to go back to a headquarters-based model. Providing secure remote access for onsite and virtual workforces is essential for organizations, especially with remote workers often using under-protected or even unsecured endpoints and network connections. That means that organizations need to make intelligent, strategic decisions on the tools and services they use to bolster cybersecurity readiness.
Regardless of industry, geography, or number of employees, organizations must look for remote access tools that unify their visibility and protection. It is also crucial that organizations look at these and other cybersecurity tools holistically, rather than as individual point products, to help prevent security remote access gaps and promote efficient deployment and management.
Cloud security
Utilizing the cloud to power applications and storing data online meant most could continue to work from home with minimal disruption. Cybercriminals were aware of this and quickly began exploiting weaknesses and vulnerabilities within the cloud. Indeed, there has been a 630% rise in cloud-based attacks since 2020. Multiple factors contribute to the issues associated with deploying and maintaining highly secure cloud environments. It is vital to consider the shared responsibility model, Lack of visibility, and misconfiguration / configuration drift.
Third-party risk management
Attacks via third parties are increasing every year as reliance on third-party vendors continues to grow. Organizations must prioritize the assessment of top-tier vendors, evaluating their network access, security procedures, and interactions with the business. Unfortunately, many contradicting factors make this assessment difficult, including a lack of resources, increased organizational costs, and insufficient processes. The lack of up-to-date risk visibility on current third-party ecosystems can lead to loss of productivity, monetary damages, and loss of reputation.
Sustaining compliance and risk management
The scale and scope of risks are changing at an unprecedented pace, propelled by the increasing interconnectedness of organizations, as well as rapid disruptions in business models and technology landscapes. As organizations strive to manage these risks, what will some of their top priorities be in 2021 and beyond to focus on an integrated risk management approach beyond GRC.
It is not about listing out all the potential risks but about connecting them to business outcomes and, more importantly, seeing it through risk mitigation. As organizations embark on this journey of implementing integrated risk management and at the same time realizing the benefits of their existing GRC (Governance, Risk and Compliance programs), it is vital to adopt a building block approach with unifying risks across the organization, adding automation to improve accuracy and consistency, linking incidents, claims, risks, and controls to action plans and providing the right metrics to assist with actionable enterprise decisions.
Risk-based vulnerability management
Managing vulnerabilities inside of your environment is challenging. New attack vectors for threat actors to breach your network are identified daily. Organizationally, the attack surface is constantly changing due to IT device and platform lifecycle issues, changing operational priorities, and the adoption of emerging technologies. With every change comes the risk that a new flaw or configuration issue will provide a threat actor with the final link in their attack chain, resulting in an impact on your users, operations, and customers.
Your network is expanding, not only in the traditional sense, but also with the ever-increasing role of endpoints, devices, and the Internet of Things. Each year you see the amount of data multiply exponentially, the threat of attacks become more sophisticated, and the challenge of minimizing risk and optimizing operations grow more challenging. It can feel like a never-ending battle, yet identifying, prioritizing, and managing vulnerabilities all the way through remediation is not only possible—it can be simple.
Vulnerability management is an established function of information security, but with technology configurations constantly evolving and cloud and container infrastructure expanding, the complexities of vulnerability management persist. Today’s best vulnerability management platforms have been designed with the principles of visibility, automation of remediation, and improved prioritization of vulnerabilities.
Ask the right questions
Security needs to be a business imperative and should be woven into the fabric of all business decisions, whether that is regarding digital risk, business continuity, or business adaptability.
Organizations should review their current state of cybersecurity to understand where there may be red flags or glaring gaps. Be honest and ask difficult questions. Does positive cybersecurity hygiene exist in your organization? Is the company doing enough to raise security awareness? Are there adequate protections in place to allow employees to work remotely? Are the cloud infrastructures being continuously monitored and highly secured? Do all endpoints, including dedicated IoT devices, have security in place? Do we have defenses to help mitigate potential DDoS and other network-based attacks? Can we guarantee that we understand the business’ attack surface? Is security deeply embedded and rooted within the company’s culture? And most importantly, do you have a ‘security first’ mindset?