Purple Teaming is for Red Teamers too. No, really! Sure, the job is ultimately to help the Blue Team be able to fight off more sophisticated attacks, but this is not a bad thing. It means as a Red Teamer you must get better, which means cooler attacks!
So the normal Red Team / pentest involves executing attacks, trying NOT to get detected, gaining domain admin or access to sensitive data and handing a report over. In a Purple Team exercise there is the ability to do all this and more, repeatedly, to try for more sophisticated attacks. You learn by getting caught then trying different techniques to not get caught. It’s an iterative process.
For a more in-depth Red Team description please visit the Red Team Journal
In a simple example, a pentester may drop a basic executable on disk assuming that it will not get caught by antivirus. It gets caught when the Blue Team discovers it. Game over.
In comparison, a pentester drops an executable and it gets caught by antivirus. The Blue Team lets them know, so they restart and try again with something else (potentially running in memory). Thus the iterative process which increases the Blue Team's security controls and has the added benefit of increasing the Red Team pentester’s ability
There are multiple advantages of Purple Teaming for a Red Teamer. Below I outline several different attack steps, some things to try, and the value you will get out of it.
Most clients are Windows-heavy so I reached out to a good friend of mine, @invokethreatguy (https://twitter.com/InvokeThreatGuy), who is a co-founder of a local Canadian ‘Red Team’ (that's how I distinguish it from a pentest puppy mill) to get some advanced examples of PowerShell to use (as presented later in this piece.)
Why as a Red Teamer You Should Purple Team It
Gaining Access
Phishing is extremely successful. Users click, but it's not that simple to get command execution. There are many items to bypass: first, the email filter (spam, attachment); then the antivirus scan; and potentially sandbox analysis. This is known as the “email minefield” by Red Teamers, and it is very treacherous. Even if a user clicks the link (if it is delivered), any detection in the chain and the Red Teamer will not get the desired command-execution.
Thus, learning the different parts of the chain and how to bypass each one is extremely valuable as an attacker.
These can include:
Different ways to infect, like droppers, .exe, .dll and in memory
- Testing with different file attachments
- Using this tool by Chris Gates (https://twitter.com/carnal0wnage) to help
- Making the phish less obvious – looking at whether it ‘looks’ the same on the receiving end as it does when launching the email
Here’s an example of a security tool that will give you trouble:
- Ironport - Understanding why and how to bypass this tool is very advantageous
Privilege Escalation:
The OSCP course is great for teaching many different privilege escalation techniques inboth Linux and Windows, but it does not allow you to test against any security devices (it’s privilege escalation specific).
With new technology such as white-listing applications, kiosk-type desktops and Device Guard, attempting to not get caught ‘trying’ to escalate privileges is becoming increasingly more difficult. This is partly due to security analytics and behavioral heuristics.
Some ideas for what to think about and tools to test are listed below:
- Manually - cmd or via the terminal
- Reading up on PowerView
- A usage guide
- Playing with Pentest monkey
- Playing with the application white-listing tool to understand how it works
- Figuring out why one technique gets flagged but another does not?
- Looking at Bypass UAC (not a true Privilege Escalation in the normal sense) to get into a higher context
- Understanding the 'opsec' safe warning is important (artifacts left, or requires user interaction, or something shows on screen). ‘Opsec’ being the term of not getting caught, aka operational security
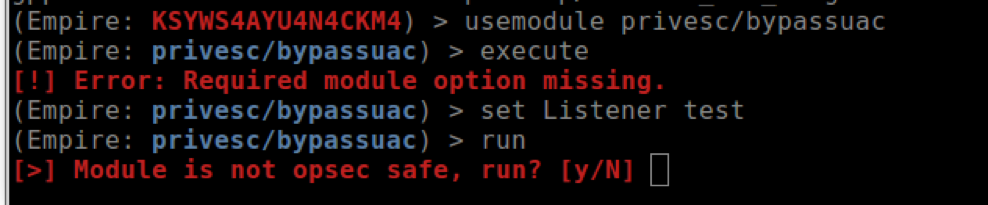
Host Reconnaissance:
After initial access to a network, you need to figure out where you are, who you are and what system you are on. Again - host based detection is improving, so attackers should be too.
Things to test when you have infiltrated a host are listed below, as well as some questions to ask yourself as a pentester:
- Common CMD & Terminal commands – “Ipconfig” & “whoami”
- Beware: a company may alert of any actions they deem as ‘having malicious intent’, as a result they could alert on simple commands an attacker would use to identify which system they are on.
- Network shares
- Understanding how to access a network share as normal traffic (not as a user that would NEVER access it) will / should bypass any alerts. This can be as simple as identifying network shares that are accessible from the system you have access on and accessing them as the ‘local user’ / normal use that would be on that system.
- Gaining host information with WMI
- Cookbook
- Administering WMI
- Are any PowerShell modules blocked?
- Get-AD may not be enabled on a workstation so look for cmdlets that allow similar functionality
- How locked down is the system, and can you transfer files onto it? Perhaps via Notepad, Internet Explorer etc.
Network Recon:
Once having mastered the initial host, an attacker will look to move laterally. There are many different techniques for this: some use network scanning tools like Nmap and others will use PowerShell (although these are not the only techniques)
Things to look at:
- Internal Network scanning - Nmap
- Nmap is the most basic tool to identify systems and the subsequent ports that are open. A real attacker would not use this, so testing this most basic tool is crucial.
- When using Nmap in an environment, think about things like “Does this get picked up?” or “Can you slow the scan down to avoid detection?”. Ask the defensive team if they detected the scanning, as understanding how to tweak Nmap to be less detectable makes you a better attacker.
- Network Traffic Monitoring
- Having awareness on what a defender can see through different networking monitoring tools can be very useful. A few clients of mine have been able to detect traffic out of the network, but not internal workstation-to-workstation communication.
- Arp packet sniffing is much stealthier
- This is passive reconnaissance and does not require any active connections to remote systems.
- To add to this, passively sniffing the network traffic in its entirety may reveal move information than just IP addresses. Hint: passwords
- PowerShell (more stealth)
- As Active Directory is typical in a client environment, so is PowerShell and thus its importance, backed up by multiple talks on this at DerbyCon 6.
The image below shows using PowerShell to gain a system's hostname; a simple way to identify hosts:
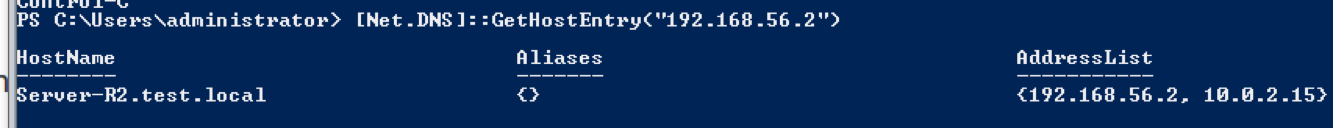
To scan a network, the command can be placed into a for-each loop such as:
Foreach ($i in 1..10)
{
[Net.DNS]::GetHostEntry(“10.132.34.$_"}
}
Lateral Movement
Say you are in a client's environment with some type of privilege. How do you move laterally and why? Do you know which techniques are stealthier than others, or which look like normal user traffic? Learning the why and what - not just the how - is extremely important for attackers.
These can include:
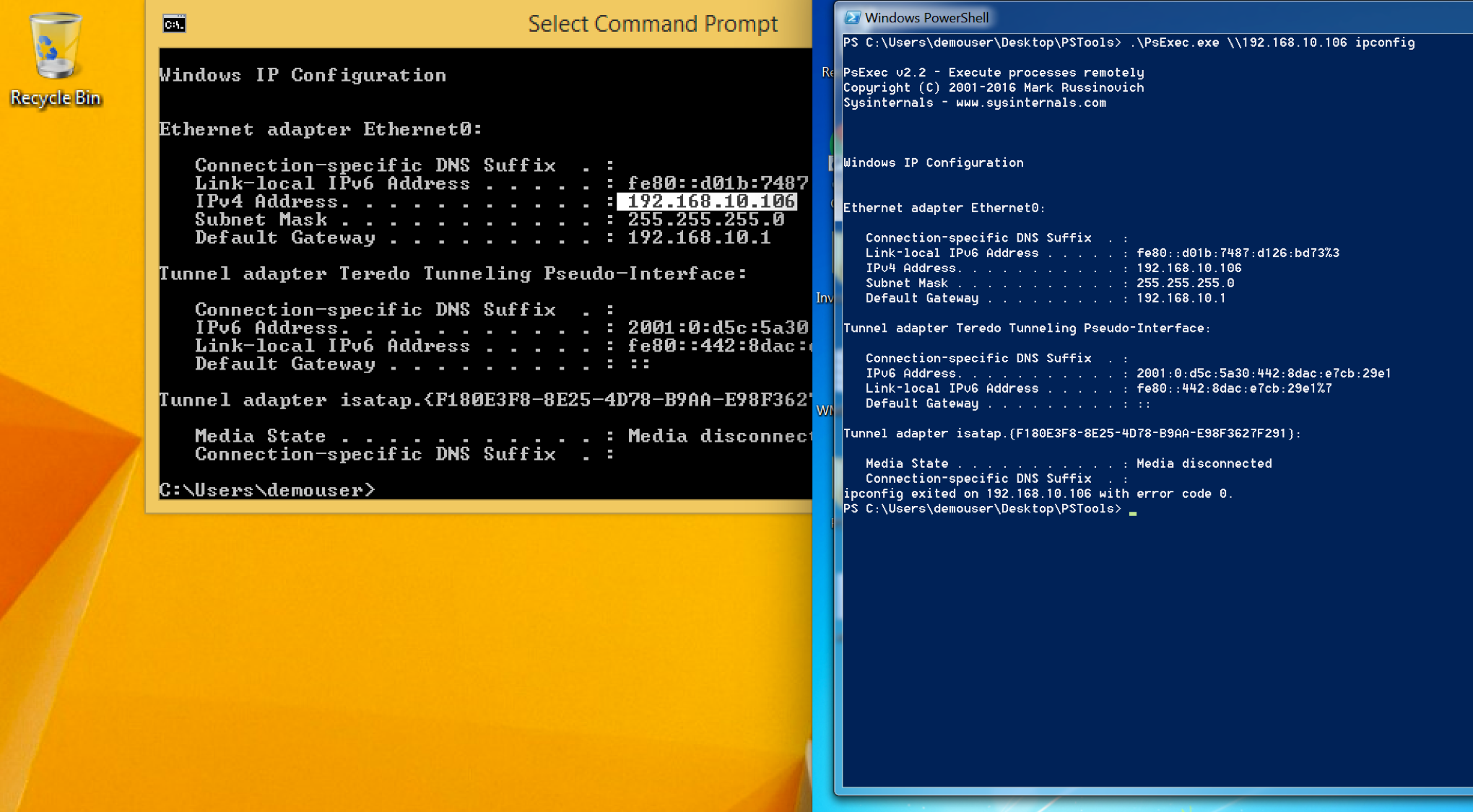
- Using PsExec to execute:
- Metasploit
- Impacket Psexec.py
Below is the native Windows PsExec to execute ipconfig on a remote host:
- Windows Management Instrumentation (WMI)
- Anything native to the Windows environment should be looked at. As such, WMI has many options for host and network reconnaissance and user identification.
PowerShell Remoting, using PowerShell on remote computers with a persistent connection (https://msdn.microsoft.com/en-us/powershell/reference/5.0/microsoft.powershell.core/new-pssession)
PowerShell remoting is another way to move laterally or create a file on another machine as per the image below:
Executing a command on a remote host can also be used with PowerShell but via Invoke-Command (https://msdn.microsoft.com/en-us/powershell/reference/5.1/microsoft.powershell.core/invoke-command) as shown below reading a text file:
Learn Blue Team's Defense - Security Controls / Applications / Response
Attempting different attacks enables attackers to be more aware of the Blue Team side, which results in becoming a better attacker! Below are some examples, and things to be aware of when working with the Blue Team. This will help you get the most out of the exercise. Do not just think of your toolset and what gets caught, but also how the network is set up and what processes could be in place by a response team.
As a side note, Cheryl Biswas (https://twitter.com/3ncr1pt3d) and I did a Blue Team talk (https://www.youtube.com/watch?v=bd9g--uq7PE), and if you go through that talk with an attacker mindset, you can understand the basics of network defense with Threat Intelligence in order to identify what gaps a company may have; because really, the basics are not being done.
Artifacts
As an attacker we rarely get to see the artifacts we leave behind. We can test at home, but there is nothing like an enterprise environment. Attackers can use Blue Team insights to identify what tools are better for which situations, and which should be left as emergencies (based on chance of detection).
- Understand which event logs are left behind by each attack
- Understand what the Blue Team uses as an indicator of compromise
- Understand different types of logs (network, host, web application)
Applications
Blinky boxes (InfoSec tools) are pricey! I do not have the money to purchase all the different types of Firewalls and IDS available. So any chance a client will allow me to see or play with one, I jump at the chance to do so. The benefit to a pentester is in learning them and how to bypass them:
- Learn different antivirus products
- Understand what alerts are given
- Work with enterprise security tools - this will raise your game.
- Understand the response process when an alert is given
- Think of potential ways to distract them during a response.
- Learn Firewall | IDS | Application white-listing | Applocker
Incident Response:
If you are lucky enough to pentest a company that has an investigations team, you can understand how they respond to alerts and investigate those. If not, maybe you can see how the IT team would respond (if at all).
Even understanding the 6 SANS IR steps will improve attackers’ awareness on a network.
Questions to help Red Teamers make the most of understanding the Blue Team's response:
- Will they look at the host first?
- Do they investigate network traffic?
- How deep do they go?
- How do they determine if the system is infected or if it's a false positive?
- Are samples run through automated analysis tools like Cuckoo?
- Do they analyze targeted malware or outsource it?
- When and how do they escalate?
- What is the mean time to detection?
Internal or External Red Team for Purple Team?
In closing, I want to discuss my thoughts on the benefits of an Internal Red Team over an External Red Team for Purple Team exercises.
An external Red Team has the benefits of seeing different environments which results in having to change different techniques and tactics. However, as I have experienced in Canada, this benefit becomes limited very fast as most companies are at a similar level, thus more generic techniques work. For example, Nmap scans (default settings) can scan multiple subnets, either due to flat networks or routing traffic forward for convenience.
An internal Red Team will only see the internal network, and the changes it goes through over time. This can be a huge limiting factor for skills of a Red Teamer, as they may be testing new systems or networks but only allowed to test for the same things (although notably the external team may also have such constraints).
An internal Red Team must conduct regular Purple Team exercises to stay up to date. Testing the same things on slightly different systems and networks is not going to improve the organization. In order for the Red Team to improve, the Blue Team must improve. Thus, it is a very symbiotic relationship. To be a serious attacker, you must test your skills and understand them in more detail. Through this, all of the above examples can be tested and verified for the Blue Team. Which only makes the Red Team better!
I am very open for discussion, difference of opinion and always wanting to learn. You can find me on Twitter at https://twitter.com/haydnjohnson.




