Internal Vulnerability Scanning for PCI Compliance
Accelerate PCI Compliance with Internal Vulnerability Scanning and More in One Powerful Product
Simplify Your Internal Vulnerability Scans to Meet PCI Compliance Faster
For organizations that must comply with PCI DSS, establishing a robust internal vulnerability scanning program is essential to passing the next audit. Specifically, PCI Requirements 6 and 11 define the security technologies and processes required to detect and remediate vulnerabilities on critical infrastructure in scope of PCI.
However, IT security teams in pursuit of PCI compliance typically need more than vulnerability assessment technologies to bring their organizations into full PCI compliance. And, they are typically working on very tight deadlines to get audit-ready.
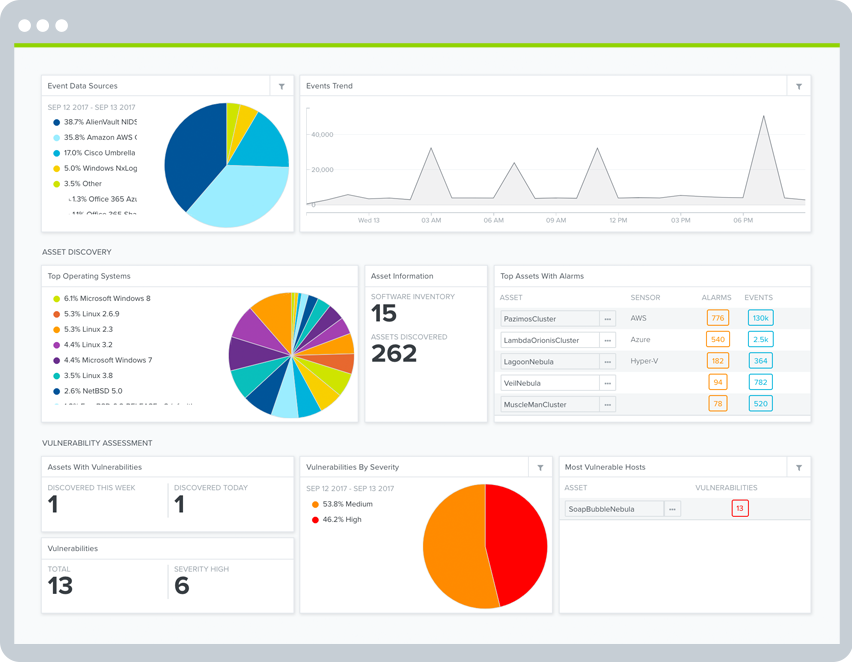
Unified Security Management™ (USM) delivers the essential internal vulnerability scanning capabilities needed for PCI Requirements 6 and 11, combined with multiple other essential security technologies that address the remaining 10 PCI Requirements: asset discovery, intrusion detection, behavioral monitoring, SIEM, and log management.
A unified, easy-to-deploy security and compliance solution, the USM platform helps IT organizations of all sizes to achieve PCI compliance faster and at a fraction of the cost of deploying multiple point security solutions.
In just 1 to 2 days, you can get started with USM for your on-premises, AWS cloud, or Azure cloud PCI environments.
USM delivers the essential security capabilities needed to demonstrate PCI compliance for internal vulnerability scanning and much more. Discover the advantages of the USM platform for compliance, including —
The Fastest Way to Pass the Toughest PCI Requirements
- Understand what it takes to pass PCI DSS requirement 11
- Discove USM's comprehensive approach to vulnerability management
PCI-Friendly Vulnerability Ranking & Remediation Support
- Prioritize your remediation activities with PCI-friendly "high, medium, low" risk ranking
- Unify asset, vulnerability, and intrusion data to investigate and remediate faster
- Apply asset & real-world threat context to assess your vulnerabilities & prioritize response
Compliance & Security Management Delivered in One Affordable Solution
- Deploy a single solution with unified capabilities for security & compliance success
- Use continuous threat intelligence updates from the Alien Labs Security Research Team
The Fastest Way to Pass the Toughest PCI Requirements
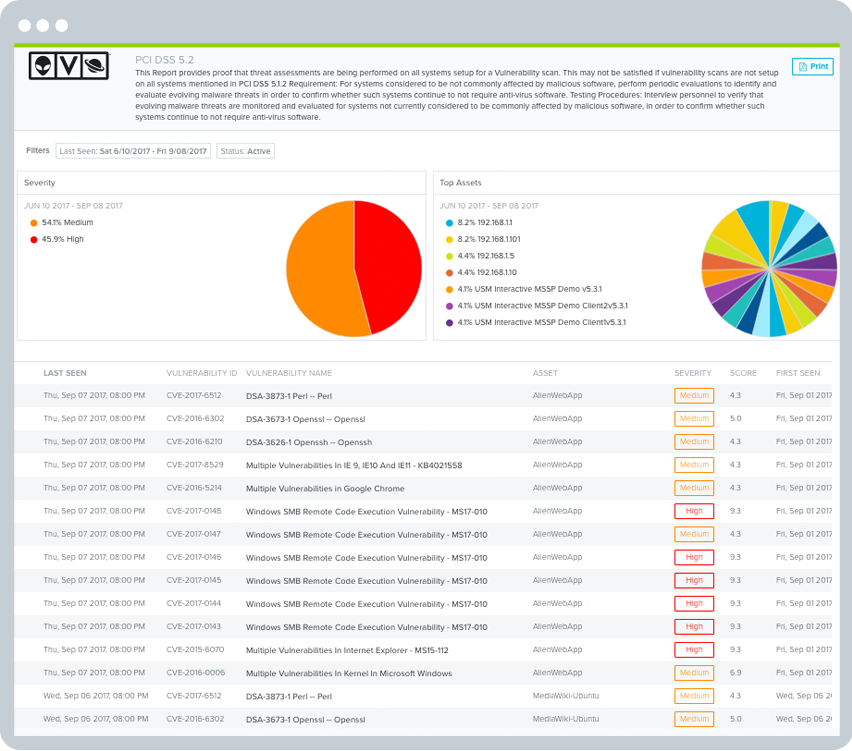
Industry data indicates that PCI DSS Requirement 11, "Regularly test security systems and processes," is the most commonly failed requirement. Internal vulnerability scanning is a key component of this challenging requirement.
It's important to understand that, while there are six sections in PCI Requirement 11, only one section (11.2) outlines internal vulnerability scanning requirements. The other five sections require entirely different security system tests or processes.
Requirement 11.2 reads:
"Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (such as new system component installations, changes in network topology, firewall rule modifications, product upgrades)."
It's also important to understand the difference between internal and external network vulnerability scans. For external scans, you must contract the services of an approved scanning vendor (ASV).
For internal vulnerability scans, you should have in place a robust vulnerability scanning tool, develop a quarterly scanning cadence, and be ready to scan on demand whenever major system changes occur.
USM supports the aspects of Requirement 11 that relate to security technology requirements for internal vulnerability scans.
USM delivers simple yet flexible vulnerability assessment tools. The USM platform combines asset discovery with vulnerability assessment, so you always have the most accurate, up-to-date asset inventory for your vulnerability scans.
USM supports the following vulnerability scanning capabilities:
- Regularly scheduled auto-scans that run daily, weekly, or quarterly as required by PCI. Automated scanning ensures continuous visibility of your vulnerabilities.
- Authenticated scans use host credentials to scan assets, identifying vulnerable software packages, local processes, and installed services.
- AWS vulnerability scans in USM Anywhere automatically perform internal vulnerability scans within your AWS PCI environment.
- Azure vulnerability scans in USM Anywhere automatically perform internal vulnerability scans within your Azure PCI environments.
In addition, rescans can be easily scheduled or run on demand as soon as you've implemented the necessary patch or deployed a new configuration. What's more, each scan preserves a time-stamped historical record, so you can easily show your assessor that you're actively rescanning to achieve and maintain a compliant posture.
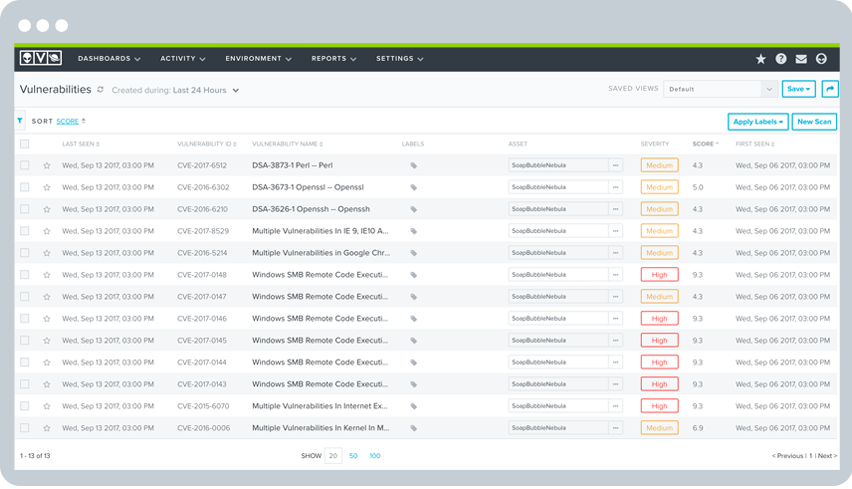
PCI-Friendly Vulnerability Ranking & Remediation Support
Internal vulnerability scanning is only half the battle. To meet compliance requirements, you need to take action to remediate high-risk vulnerabilities and then demonstrate that your remediation has in fact fixed the vulnerability.
USM eases and accelerates vulnerability remediation activities in several ways —
Prioritize Remediation Activities with “High, Medium, Low” Risk Ranking
Section 11.2.1b states that you can only pass your audit if all vulnerabilities ranked “high-risk” are resolved (as defined in 6.1). Thus, a prerequisite to meeting requirement 11.2.1b. is to assign a risk ranking to newly discovered vulnerabilities.
The USM platform automatically assigns risk ranking to vulnerabilities in a PCI-friendly way, using the CVSS base score taxonomy as suggested in PCI DSS. You can readily search, analyze, and report on vulnerabilities according to their ranking, making it easier to prioritize remediation and show compliance.
Reduce False Positives
When it comes time to remediate vulnerabilities, the less time spent removing false positives the better. USM works to reduce false positives, maximizing your time, and making those vulnerability reports look good for your PCI DSS assessor.
Unify Asset, Vulnerability, and Intrusion Data to Investigate and Respond Faster
USM brings together critical security data from asset inventory, vulnerability assessment, and intrusion detection systems in a single pane of glass, so you can prioritize your vulnerability remediation efforts according to the significance of the asset (e.g., the vulnerable asset is in-scope of PCI) and if there are active threats targeting the asset. Having a unified view of all relevant security data in one location makes remediation faster, easier, and more accurate than using siloed security tools.
Apply Real-World Threat Context to Your Vulnerabilities
The Alien Labs Security Research team fuels the USM platform with continuous threat intelligence updates, including the latest vulnerability signatures, so you know exactly which vulnerabilities are actively being targeted in the wild and if any of your systems are communicating with known malicious hosts. In addition, integrated remediation guidance gives you a head start on tackling remediation.
This integrated intelligence helps you to better prioritize remediation, improve security, and lends itself to the PCI incident response requirements included in Requirement 12—all of which are good.
Align Your Compliance & Security Objectives with Unified Security Essentials
Security and compliance are often seen as divergent goals. Improving your security posture doesn't guarantee that you will easily pass your next PCI audit. On the other hand, just because you passed your audit doesn't mean that you are secure.
To meet your compliance requirements and to continuously maintain a healthy security posture, you need to align your security and compliance objectives and activities.
USM makes it simple to align your compliance and security work onto a single pane of glass. It not only helps you to achieve compliance quickly and stay in compliance all year long, but also it simplifies and accelerates your security monitoring with unified security essentials and integrated threat intelligence.
USM delivers the following essential capabilities that help you to achieve PCI compliance and a healthy security posture. (Click on each link to learn more):